StackPath’s Security-First Approach to CDN
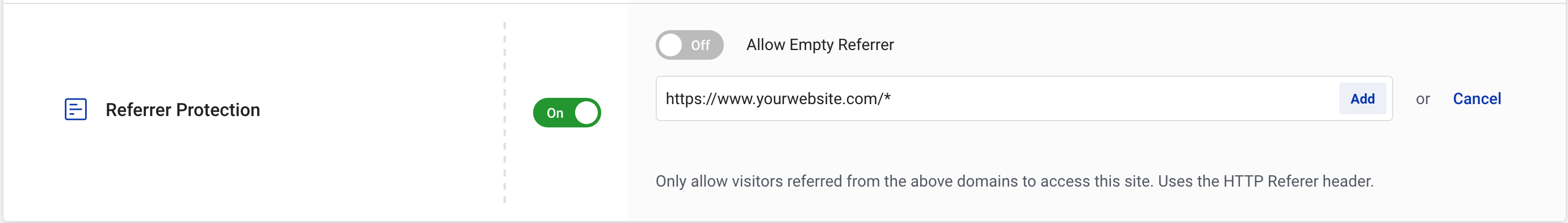
StackPath prioritizes security in its Content Delivery Network (CDN) services to protect customer data and ensure content integrity. Here are the key aspects of its security-first approach:

1. Network Security:
- Distributed Edge Network: StackPath’s CDN spans over 50 locations globally, providing geographical redundancy and reducing latency. Each location features dedicated security appliances and firewalls to prevent unauthorized access.
- SSL/TLS Encryption: All traffic on the StackPath CDN is encrypted using SSL/TLS certificates, safeguarding data from eavesdropping and man-in-the-middle attacks.
- IP Whitelisting: Customers can restrict access to their CDN content by whitelisting specific IP addresses, allowing only authorized entities to connect.
2. Application Security:
- Web Application Firewall (WAF): StackPath offers a fully managed WAF that blocks malicious traffic, such as SQL injections, cross-site scripting (XSS), and distributed denial-of-service (DDoS) attacks.
- DDoS Protection: StackPath’s DDoS mitigation service automatically detects and blocks DDoS attacks, protecting customer websites and applications from downtime.
- Rate Limiting: Customers can configure rate limits to prevent excessive requests and protect against brute-force attacks and denial-of-service conditions.
3. Data Protection:
- Encryption at Rest: All customer data stored on StackPath’s CDN is encrypted using industry-standard algorithms, ensuring confidentiality and preventing data leaks.
- Data Retention Policies: StackPath implements configurable data retention policies, allowing customers to control the duration of data storage and minimize the risk of data breaches.
- Compliance Certifications: StackPath adheres to rigorous compliance standards, including ISO 27001, SOC 2 Type II, and GDPR, demonstrating its commitment to data security and privacy.
4. Security Monitoring and Incident Response:
- 24/7 Security Monitoring: StackPath’s security team continuously monitors its CDN network and applications for suspicious activity, identifying and responding to threats promptly.
- Incident Response Plan: StackPath has a comprehensive incident response plan in place to minimize the impact of security breaches and restore normal operations as quickly as possible.
- Transparency and Communication: Customers are kept informed of security incidents through clear and timely communication channels.
Benefits of StackPath’s Security-First Approach:
- Enhanced protection against cyberattacks and data breaches
- Reduced risk of downtime and business disruptions
- Improved compliance with data privacy regulations
- Increased confidence in the integrity and availability of content
- Peace of mind knowing that data is secure and protected## Understanding Stackpath’s Security-first Approach to CDN
Executive Summary
Stackpath is a leading Content Delivery Network (CDN) provider that prioritizes security as a cornerstone of its service. By deploying a comprehensive suite of security measures, Stackpath empowers businesses to safeguard their digital assets, enhance data protection, and maintain compliance with industry regulations.
Introduction
In today’s digital landscape, the need for robust cybersecurity measures is paramount. For businesses relying on CDNs to deliver their content, choosing a provider with a strong security posture is crucial. Stackpath stands out as a leader in this regard, offering a comprehensive security-first approach to CDN operations.
FAQs
-
What sets Stackpath’s security approach apart?
- Stackpath is SOC 2 Type II and ISO 27001 certified, demonstrating compliance with industry best practices.
- Deploys advanced threat intelligence and 24/7/365 security monitoring to detect and mitigate threats promptly.
- Leverages multi-layered DDoS protection, web application firewall (WAF), and TLS encryption to safeguard against cyberattacks.
-
How does Stackpath’s security benefit businesses?
- Protects sensitive customer data and intellectual property from unauthorized access and data breaches.
- Enhances website performance by preventing malicious traffic and downtime.
- Boosts customer confidence and trust by providing a secure and reliable online experience.
-
What are the key features of Stackpath’s security-first approach?
- Edge security: Implements a WAF and DDoS protection at the network edge to block malicious traffic before it reaches the origin server.
- Content security: Uses SSL/TLS encryption and Origin Shield to protect data in transit and at rest.
- Network security: Leverages global Points of Presence (PoPs) with redundant infrastructure and multiple transit providers for maximum uptime and resilience.
Subtopics:
Edge Security
- Web Application Firewall (WAF): Identifies and blocks malicious traffic, including SQL injection, cross-site scripting, and DDoS attacks.
- DDoS Protection: Mitigates distributed denial-of-service attacks by absorbing and redirecting malicious traffic away from the origin server.
- IP Reputation Filtering: Blocks known malicious IP addresses to prevent phishing, malware, and botnet attacks.
- SSL/TLS Encryption: Protects data in transit between the CDN edge and the origin server using industry-standard encryption protocols.
- Origin Shield: Protects the origin server by hiding its IP address and minimizing its exposure to direct attacks.
Content Security
- Data Encryption: Encrypts data stored on Stackpath’s servers using AES-256 encryption, ensuring data protection at rest.
- HTTPS Delivery: Forces all website traffic to use HTTPS, enforcing secure communication between the CDN edge and end users.
- Content Integrity Monitoring: Detects and alerts on changes to website content, preventing unauthorized modifications or content hijacking.
- Origin Authorization: Restricts access to the origin server to authorized personnel, preventing unauthorized access to sensitive data.
- Geo-Blocking: Limits access to content based on geographical location to comply with local laws and regulations.
Network Security
- Global Points of Presence (PoPs): Distributes CDN infrastructure globally to provide low latency and high-performance content delivery.
- Redundant Infrastructure: Utilizes multiple data centers and transit providers for increased uptime and resilience, ensuring uninterrupted service.
- BGP Anycast Routing: Optimizes routing paths to deliver content from the closest PoP, reducing latency and improving user experience.
- BGP Security: Monitors BGP routing tables to detect and mitigate routing anomalies, preventing network hijacking or malicious redirection.
- DNS Security: Implements DNSSEC and other security measures to prevent DNS cache poisoning and DNS hijacking attacks.
Application Security
- API Security: Secures APIs using authentication, authorization, and rate limiting to prevent unauthorized access and abuse.
- Bot Management: Detects and mitigates malicious bots, including web crawlers, scrapers, and spam bots.
- Payload Inspection: Inspects incoming and outgoing HTTP requests and responses for malicious content, preventing data exfiltration and malware infections.
- Rate Limiting: Controls the rate of API calls and website requests to prevent denial-of-service attacks and API abuse.
- WebSockets Security: Enforces secure WebSocket connections using TLS encryption and rate limiting to prevent unauthorized access and malicious activity.
Compliance and Monitoring
- SOC 2 Type II and ISO 27001 Certification: Demonstrates adherence to strict security standards and best practices, providing peace of mind for businesses.
- 24/7/365 Security Monitoring: Continuously monitors network traffic, logs, and security events to detect and respond to threats promptly.
- Incident Response Plan: Defines clear procedures for responding to security incidents, minimizing downtime and damage.
- Vulnerability Management: Regularly scans for and patches security vulnerabilities to prevent exploitation by attackers.
- Security Audit Trails: Maintains detailed logs of security events, user activities, and configuration changes for auditing purposes.
Conclusion
Stackpath’s security-first approach to CDN is a testament to its commitment to providing businesses with a secure and reliable content delivery solution. By deploying advanced security measures across the entire CDN stack, Stackpath empowers businesses to enhance data protection, safeguard their digital assets, and maintain compliance with industry regulations. In today’s increasingly complex cyber landscape, choosing Stackpath as your CDN provider ensures a proactive and comprehensive approach to cybersecurity, giving your business the confidence and peace of mind to thrive in the digital realm.
Relevant Keyword Tags
- CDN Security
- Web Application Firewall
- Content Delivery Network
- Cybersecurity
- Data Protection
