Understanding and Preventing SQL Injection Attacks: A Comprehensive Guide
Executive Summary

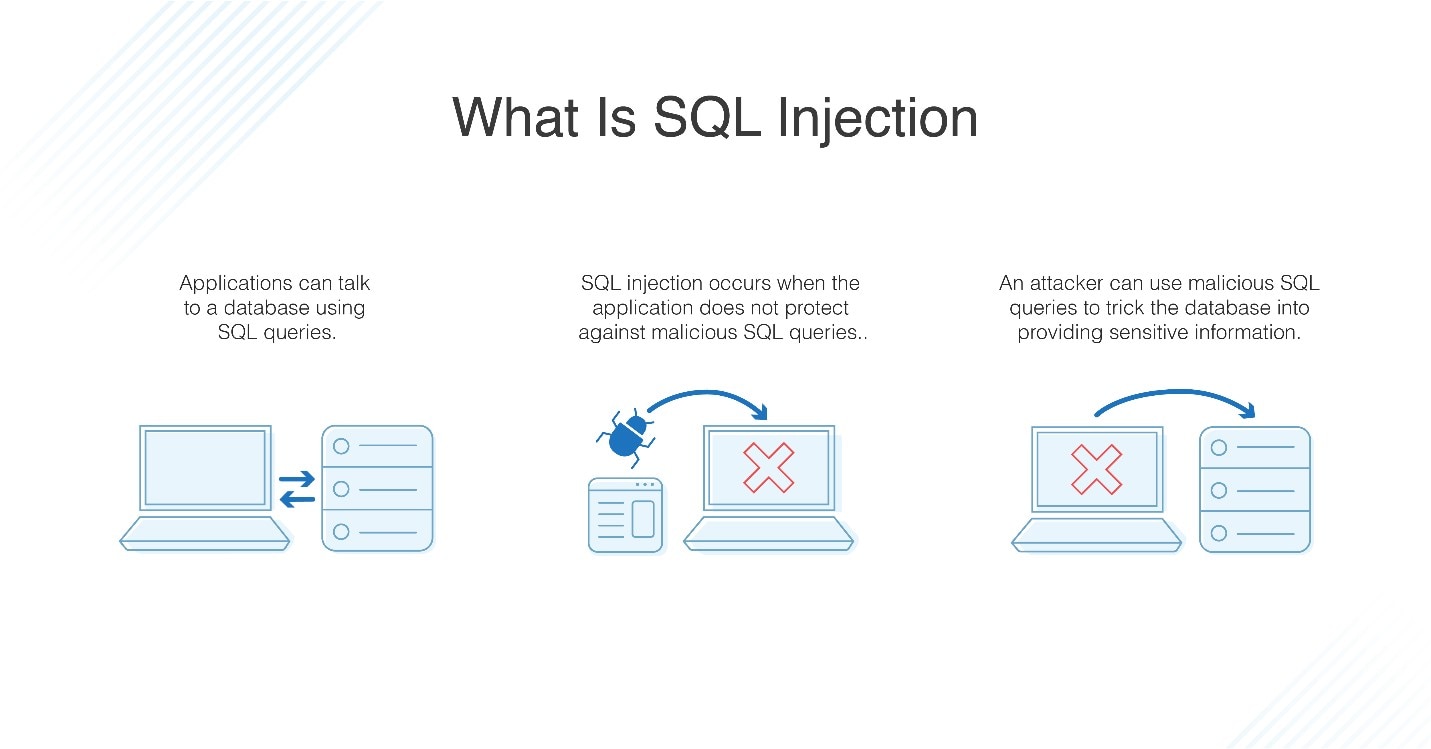
SQL injection attacks pose a significant threat to the security of data stored in databases. By exploiting vulnerabilities in SQL queries, malicious actors can gain unauthorized access, manipulate data, or even take control of databases. Understanding the nature of SQL injection attacks and implementing effective preventive measures is crucial for protecting your organization’s data and reputation.

Introduction
SQL injection attacks occur when attackers inject malicious code into SQL statements through user input or application vulnerabilities. This allows them to execute arbitrary SQL commands against the database, potentially exposing sensitive information, modifying data, or causing system disruption.
Top 5 Subtopics for Preventing SQL Injection Attacks
1. Input Validation
- Purpose: Validate user input to prevent malicious characters from being injected into SQL statements.
- Key Points:
- Use parameterized queries: Pass parameters to SQL statements instead of concatenating strings, making it harder for attackers to inject malicious code.
- Sanitize user input: Remove or encode special characters and keywords that could be used for SQL injection.
- Restrict input patterns: Use regular expressions to ensure that user input matches expected patterns.
2. Query Parameterization
- Purpose: Bind user-supplied parameters to SQL statements securely, preventing direct execution of malicious code.
- Key Points:
- Use prepared statements: Specify placeholders in SQL statements and bind user parameters separately, isolating user input from the SQL code.
- Validate parameter types: Ensure that user-supplied parameters are of the expected type (e.g., integer, string).
- Restrict parameter values: Define allowed parameter values to prevent out-of-range or malicious inputs.
3. Output Encoding
- Purpose: Encode SQL query results before displaying them to prevent code injection into user output.
- Key Points:
- Use HTML or XML entities: Convert special characters to their corresponding entities (e.g., ‘<‘ to ‘<‘).
- Escape quotes and other characters: Surround potentially malicious characters with escape sequences.
- Use a URL-safe encoding: Encrypt or encode output in a way that prevents it from being used for malicious purposes in web applications.
4. Database Permissions and Access Control
- Purpose: Restrict database user permissions to the minimum necessary to prevent unauthorized access and data manipulation.
- Key Points:
- Grant only necessary privileges: Assign users only the permissions they need to perform their job duties.
- Use role-based access control: Create roles with specific permissions and assign users to appropriate roles.
- Regularly review and revoke unused permissions: Ensure that users do not have access to data or functionality that is no longer required.
5. Secure Coding and Vulnerability Management
- Purpose: Implement secure coding practices and regularly patch software to prevent vulnerabilities from being exploited.
- Key Points:
- Use secure coding frameworks: Adhere to best practices and use tools designed to prevent SQL injection vulnerabilities.
- Regularly update software and dependencies: Patch known vulnerabilities by applying software updates promptly.
- Monitor for suspicious activity: Log and analyze application events to detect and respond to potential SQL injection attempts.
Conclusion
SQL injection attacks remain a significant threat to data security, and organizations must take proactive measures to prevent them. By implementing robust input validation, query parameterization, output encoding, access control, and secure coding practices, organizations can protect their databases and sensitive data from malicious attacks.
Keyword Tags
- SQL Injection
- SQL Vulnerability
- Data Security
- Database Protection
- Cyber Security
FAQ
1. What are the signs of a SQL injection attack?
- Malicious code in database queries
- Unexpected database behavior
- Error messages indicating SQL syntax errors
- Access to sensitive information without authorization
- Unusual user activity patterns
2. How can I prevent SQL injection in my website or application?
- Input validation
- Query parameterization
- Output encoding
- Database access control
- Secure coding practices
3. What should I do if I suspect a SQL injection attack has occurred?
- Isolate the affected systems
- Gather evidence (e.g., log files)
- Contact security experts or law enforcement
- Implement measures to prevent future attacks
4. What are the common injection vectors for SQL injection attacks?
- Web forms
- API endpoints
- URL parameters
- Cookies
- HTTP headers
5. How can I stay up-to-date on the latest SQL injection threats and vulnerabilities?
- Monitor security news and advisories
- Subscribe to security blogs and newsletters
- Attend industry conferences and webinars
- Implement vulnerability scanning and penetration testing
