Significance of Secure Token Authentication in CDN Services

Content Delivery Networks (CDNs) are crucial for delivering high-quality online content quickly and efficiently. Secure token authentication plays a pivotal role in ensuring the security and integrity of CDN services, providing the following benefits:
1. Authorization and Authentication:
Secure tokens act as authentication credentials that prove the identity of a user or device. They allow CDN providers to differentiate between authorized and unauthorized access, preventing unauthorized parties from accessing sensitive content.
2. Access Control:
Tokens grant specific access privileges to users based on their roles or permissions. This enables CDNs to implement fine-grained access control, limiting the distribution of content to only those who are authorized to view it.
3. Data Protection:
Content delivered through CDNs often contains sensitive information. Secure tokens help protect this data by ensuring that only authenticated entities can access it. Tokens can be encrypted and signed to prevent unauthorized decryption or alteration.
4. Prevention of Content Theft and Piracy:
Token authentication helps deter content theft and piracy by preventing unauthorized downloads or sharing of protected content. By authenticating users and devices, CDNs can identify and block suspicious activities that could lead to piracy.
5. Scalability and Performance:
Secure tokens can be efficiently processed and validated at scale, even during high traffic scenarios. This ensures that CDN services can handle large volumes of authentication requests without compromising performance.
6. User Convenience:
Token authentication can provide a more seamless and secure user experience. Users can log in once using a token and gain access to protected content without having to repeatedly enter credentials.
7. Compliance and Regulations:
Secure token authentication helps organizations meet compliance and regulatory requirements that mandate the protection of sensitive data. By ensuring authorized access and data integrity, CDNs can assist organizations in meeting industry standards and legal obligations.
Implementation of Secure Token Authentication:
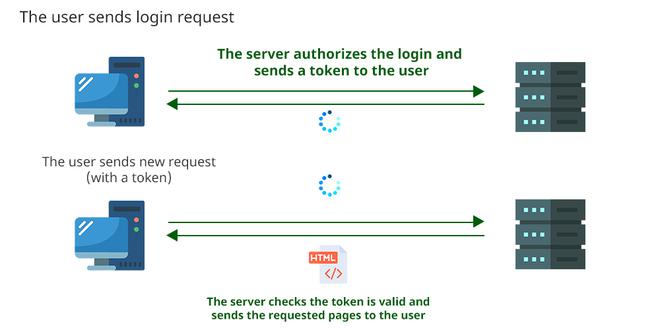
Secure token authentication is typically implemented using a variety of cryptographic techniques, including:
- JSON Web Tokens (JWTs): A standard for creating secure, digitally signed tokens that contain a payload of claims.
- OAuth 2.0: A protocol for authorization and authentication that uses access tokens to grant temporary access to protected resources.
- X.509 Certificates: Digital certificates used to verify the identity of servers and devices.
Conclusion:
Secure token authentication is an essential element of modern CDN services. It provides robust authorization, access control, data protection, and scalability, ensuring the secure and reliable delivery of online content. By implementing secure token authentication, CDN providers can safeguard sensitive data, prevent content theft, and enhance the user experience.## The Significance Of Secure Token Authentication In Cdn Services
Executive Summary
Secure Token Authentication is pivotal in CDN services, safeguarding data integrity and user privacy. By implementing robust token-based authentication mechanisms, CDN providers can effectively prevent unauthorized access, data breaches, and malicious activities, ensuring the reliability and security of their services.
Introduction
Content Delivery Networks (CDNs) play a crucial role in enhancing website performance, delivering content faster and more efficiently to users worldwide. However, with the crescente volume of data transmitted over CDNs, security concerns arise. Secure Token Authentication emerges as a vital solution, enabling CDN providers to safeguard data, protect user privacy, and maintain the integrity of their services.
FAQs
Q: What is Secure Token Authentication?
A: Secure Token Authentication is a method of authenticating users by issuing them unique tokens. These tokens are typically generated on the server side and passed to the client, which can then use them to access protected resources.
Q: Why is Secure Token Authentication important for CDN services?
A: Secure Token Authentication is important for CDN services because it helps to protect data from unauthorized access. By using tokens, CDN providers can ensure that only authorized users can access protected resources.
Q: How does Secure Token Authentication work?
A: Secure Token Authentication works by issuing a unique token to each user. This token is then used to authenticate the user when they access protected resources. The token is typically time-limited and can be revoked at any time.
Key Subtopics
1. Token Generation
- Key Generation: Generating cryptographically secure keys for token creation.
- Algorithm Selection: Choosing a robust hashing algorithm for token generation, such as SHA-256 or bcrypt.
- Timestamp Inclusion: Incorporating timestamps into tokens to prevent replay attacks.
2. Token Distribution
- Secure Channels: Utilizing encrypted channels, such as HTTPS, for token distribution to prevent interception.
- Expiration Policies: Setting appropriate token expiration times to mitigate security risks.
- Rate Limiting: Implementing rate-limiting mechanisms to prevent brute-force attacks.
3. Token Validation
- Signature Verification: Verifying the digital signature of the token to ensure its authenticity.
- Expiration Checking: Confirming that the token is still valid and has not expired.
- Revocation Verification: Checking if the token has been revoked and is no longer valid.
4. Token Management
- Centralized Storage: Utilizing a centralized repository for storing and managing tokens securely.
- Regular Rotation: Regularly rotating tokens to minimize the risk of compromise.
- Revocation Mechanism: Providing a mechanism for revoking tokens in case of security breaches or suspicious activities.
5. Best Practices
- Strong Passwords: Enforcing strong password policies to prevent unauthorized access.
- Multi-Factor Authentication: Implementing multi-factor authentication to enhance security.
- Regular Security Audits: Conducting regular security audits to identify and address vulnerabilities.
Conclusion
Secure Token Authentication is a cornerstone of secure CDN services. By implementing robust token-based authentication mechanisms, CDN providers can significantly reduce the risk of data breaches, protect user privacy, and enhance the overall security of their services. By adopting best practices, employing multi-factor authentication, and conducting regular security audits, CDN providers can ensure the integrity and reliability of their services, fostering trust among their customers.
Keywords
- CDN Security
- Secure Token Authentication
- Token Generation
- Token Validation
- Best Practices

