The Future Of Web Security With Cloudflares Innovations
Executive Summary
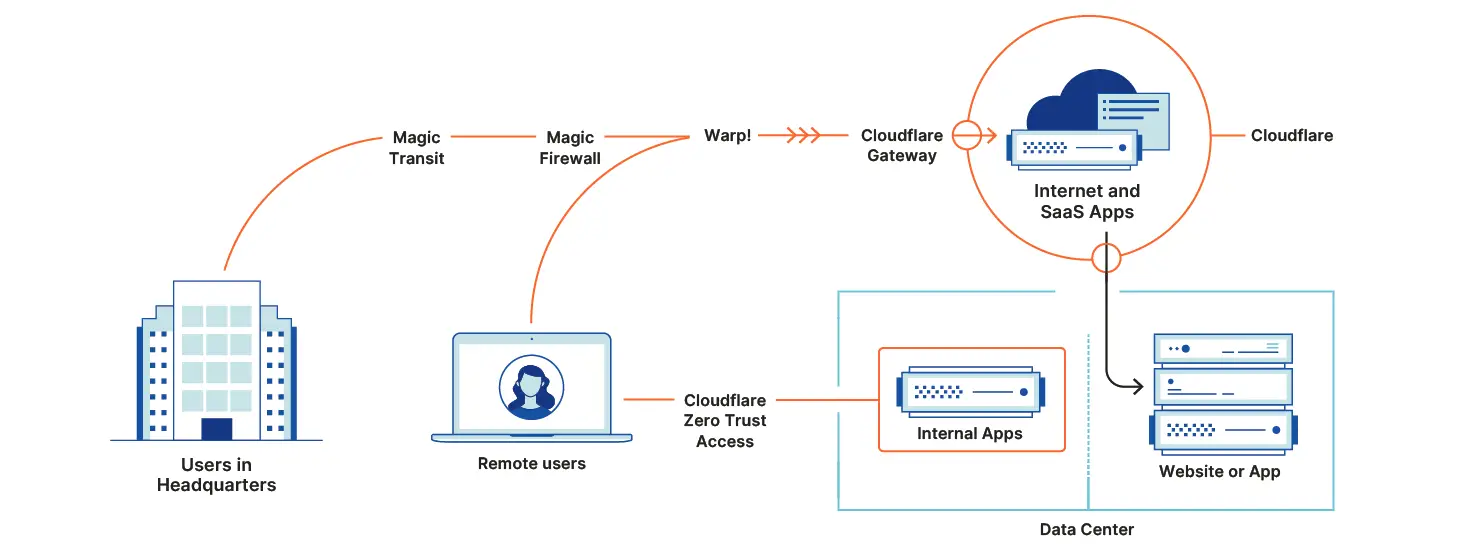
Cloudflare is a leading provider of web security and performance services. Its recent innovations are shaping the future of web security, making websites more resilient against cyberattacks and improving the online experience for users. This article explores Cloudflare’s cutting-edge solutions, their significance, and their implications for the future of web security.
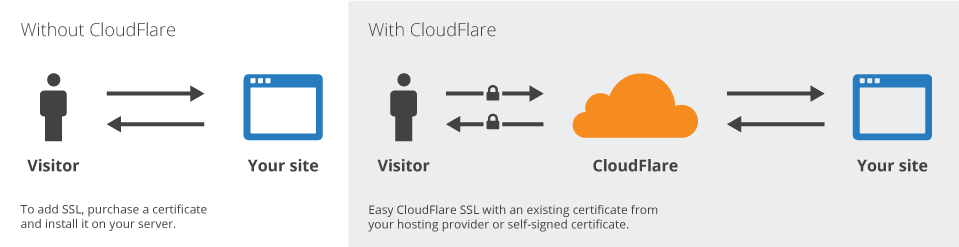
Introduction
The digital landscape is constantly evolving, and so are the threats to web security. Cyberattacks are becoming more sophisticated and frequent, making it imperative for businesses to prioritize their online defenses. Cloudflare is at the forefront of this battle, developing innovative solutions that empower businesses with robust protection against malicious actors.
FAQs
- What services does Cloudflare offer?
Cloudflare provides a comprehensive suite of security and performance services, including website protection, DDoS mitigation, content delivery networks (CDNs), and bot management. - How does Cloudflare improve website performance?
Cloudflare’s global network optimizes website content delivery, reduces latency, and improves website loading speeds, enhancing user experience. - Is Cloudflare suitable for businesses of all sizes?
Cloudflare offers flexible plans tailored to the specific needs of businesses of all sizes, from small startups to large enterprises.
Top 5 Subtopics
1. Zero Trust Architecture
- Description: Zero Trust is a security model that eliminates implicit trust, requiring continuous verification of users and devices before granting access to resources.
- Key Points:
- Identity and access management (IAM): Enforces strict authentication and authorization mechanisms.
- Network segmentation: Divides the network into smaller, more secure segments to limit the impact of breaches.
- Multi-factor authentication (MFA): Requires multiple forms of identification to prevent unauthorized access.
- Least-privilege principle: Only grants users the minimum level of access necessary to perform their tasks.
- Continuous monitoring: Regularly assesses network traffic and user behavior to detect suspicious activities.
2. Bot Management
- Description: Bot management solutions detect and mitigate automated bots that engage in malicious activities, such as web scraping, credential stuffing, and DDoS attacks.
- Key Points:
- Behavioral analysis: Identifies and blocks abnormal bot patterns based on factors like IP address, request frequency, and bot signatures.
- CAPTCHA and challenges: Presents users with challenges to distinguish humans from bots.
- Machine learning (ML): Analyzes large data sets to identify and adapt to new bot threats.
- Rate limiting: Restricts the number of requests that can be made from a single source, preventing bot attacks.
- DDoS protection: Mitigates DDoS attacks by absorbing and distributing traffic across Cloudflare’s global network.
3. Secure Web Gateway (SWG)
- Description: A SWG is a cloud-based firewall that inspects and filters web traffic to prevent malware, phishing attacks, and data breaches.
- Key Points:
- URL filtering: Blocks access to known malicious websites and domains.
- Content filtering: Scans web content for threats, including viruses, malware, and malicious code.
- Data loss prevention (DLP): Prevents sensitive data from being leaked or stolen by monitoring outbound traffic.
- Cloud Access Security Broker (CASB): Integrates with cloud service providers to enforce security policies and control access to cloud applications.
- Detailed reporting and analytics: Provides insights into web traffic patterns, security incidents, and user behavior.
4. Web Application Firewall (WAF)
- Description: A WAF is a specialized firewall that protects web applications from vulnerabilities and attacks, such as SQL injection, cross-site scripting (XSS), and remote code execution (RCE).
- Key Points:
- Positive and negative security models: Whitelists legitimate requests and blocks malicious ones.
- Advanced threat detection: Uses ML and threat intelligence to identify and block zero-day vulnerabilities.
- Rate limiting: Limits the number of requests that can be made from a single source, preventing brute-force attacks.
- IP reputation filtering: Blocks requests from known malicious IP addresses.
- Customizable rules: Allows administrators to define specific security rules based on their specific needs.
5. Content Delivery Network (CDN)
- Description: A CDN is a geographically distributed network of servers that stores and delivers website content to users, improving performance and reducing latency.
- Key Points:
- Reduced bandwidth usage: Caching frequently requested content closer to users reduces bandwidth consumption.
- Improved page loading speeds: Content is delivered from the nearest server, significantly reducing latency and improving user experience.
- Reduced server load: Offloads traffic from origin servers, enhancing website performance and scalability.
- Improved SEO ranking: Faster-loading websites rank higher in search engine results pages (SERPs).
- Global reach: A global CDN ensures that website content is accessible to users worldwide.
Conclusion
Cloudflare’s innovations are revolutionizing web security and shaping the future of the digital landscape. By embracing Zero Trust architecture, implementing bot management solutions, deploying SWGs and WAFs, and leveraging CDNs, businesses can effectively safeguard their websites against cyber threats and enhance the online experience for their users. Cloudflare’s commitment to pushing the boundaries of web security is paving the way for a more secure and resilient Internet.
Keyword Tags
- Web Security
- Cloudflare
- Zero Trust Architecture
- Bot Management
- Secure Web Gateway
