The Basics Of Windows 10 Security: Defender And Beyond

Executive Summary

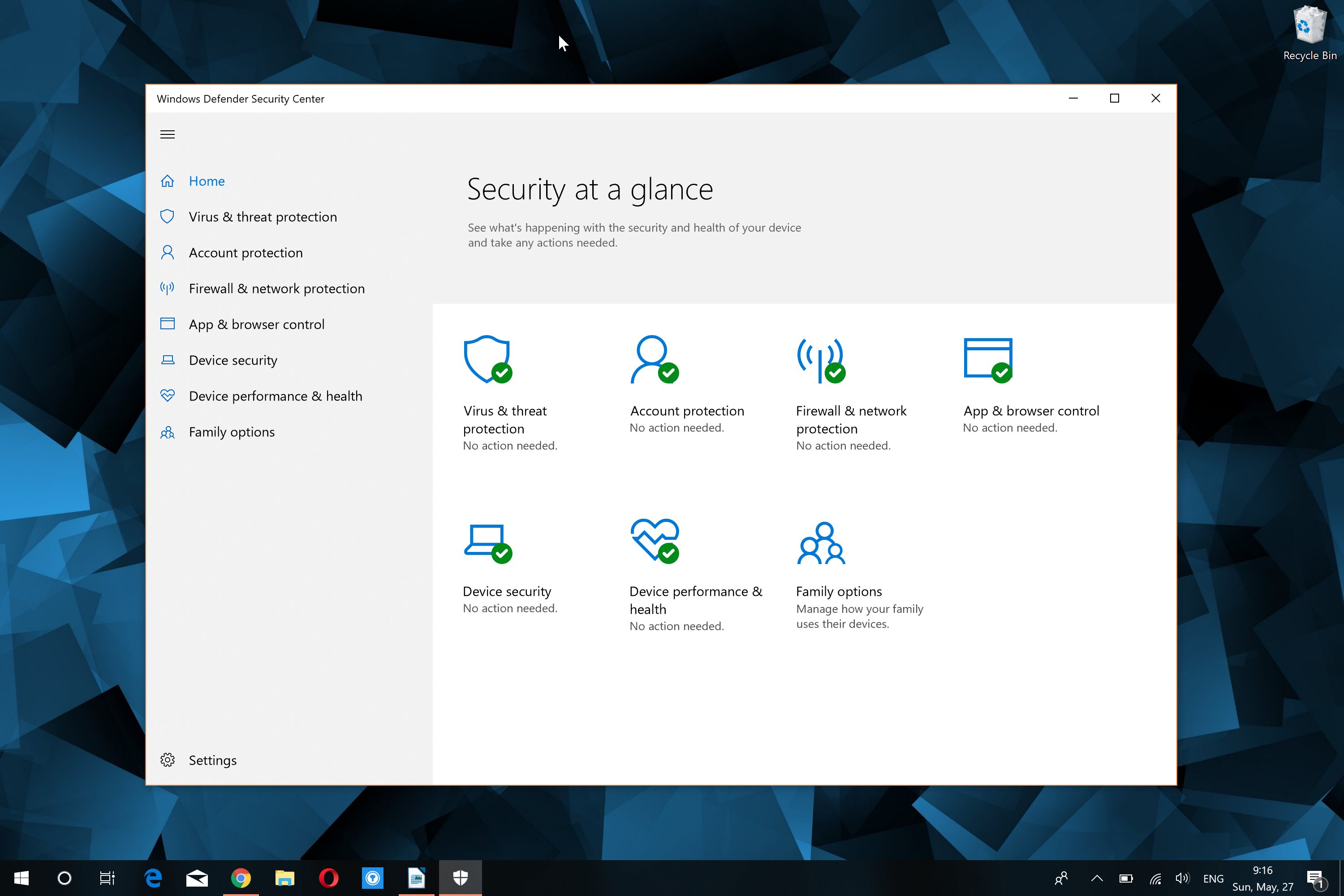
Windows 10 offers comprehensive security features with Windows Defender, but protecting your system requires a multi-faceted approach. This article delves into additional security measures beyond Defender, providing an in-depth guide to enhancing the overall security posture of your Windows 10 device.
Introduction
In today’s digital landscape, ensuring the security of your operating system is paramount. Windows 10 comes equipped with an array of built-in security tools to safeguard your data and protect against malicious threats. While Windows Defender stands as a formidable antivirus and antimalware solution, it’s essential to explore additional measures to fortify your system’s defenses. This comprehensive guide will unveil the many facets of Windows 10 security, empowering you with the knowledge to optimize your system’s protection.
1. Firewalls: A Guardian Against Unwanted Access
Firewalls serve as gatekeepers, monitoring incoming and outgoing network traffic. They scrutinize each connection attempt, blocking unauthorized access to your system.
- Windows Defender Firewall: This built-in firewall provides robust protection, automatically blocking suspicious traffic.
- Third-Party Firewalls: Consider reputable third-party firewalls to complement Defender, offering advanced features like application control and granular traffic filtering.
- Azure Firewall Manager: For enterprise networks, Azure Firewall Manager centralizes firewall management, providing visibility and control across multiple firewalls.
- Physical Firewalls: Hardware-based firewalls offer an additional layer of protection, safeguarding networks from external threats.
2. Application Control: Restricting Unwanted Software
Application control measures prevent the execution of unauthorized software, minimizing the risk of malware infections.
- Windows Defender Application Control: Enforces a strict policy, only permitting approved applications to run.
- Third-Party Application Control Tools: Advanced tools provide granular control over application behavior, allowing you to define specific restrictions and monitor application activities.
- Software Whitelisting: Create a trusted list of authorized software, ensuring only these applications can execute on your system.
- Application Isolation: Deploy virtualization or container technologies to isolate applications from the rest of the system, limiting the impact of compromised software.
3. Device Control: Managing External Connections
Device control restricts the use of external devices, such as USB drives and Bluetooth connections, to mitigate potential threats.
- Windows Defender Device Guard: Enforces hardware-based virtualization to isolate peripherals and prevent unauthorized access.
- BitLocker Drive Encryption: Encrypts external drives to protect sensitive data in case of loss or theft.
- Device Manager: Monitor and manage connected devices, disabling or removing unauthorized ones to prevent unauthorized data transfer or malware infiltration.
- Mobile Device Management (MDM): For enterprise environments, MDM tools provide centralized control over mobile devices, enforcing security policies and restricting peripheral access.
4. Patch Management: Staying Up-to-Date
Applying security patches regularly is crucial to address vulnerabilities exploited by malware.
- Windows Update: Enable automatic updates to ensure timely installation of security patches and bug fixes.
- Third-Party Patch Management Tools: Utilize specialized tools to automate patch deployment across multiple devices, ensuring consistent security across your infrastructure.
- Vulnerability Scanning: Regularly scan for potential vulnerabilities to identify and prioritize patching needs.
- Security Awareness Training: Educate users on the importance of patch management and the risks associated with outdated software.
5. User Education: The Human Firewall
Security breaches often stem from human error. User education empowers individuals to recognize and mitigate potential threats.
- Security Awareness Training: Conduct regular training sessions to educate users on security best practices, such as recognizing phishing emails and avoiding suspicious links.
- Strong Password Management: Implement password policies that enforce strong passwords and encourage the use of password managers.
- Two-Factor Authentication (2FA): Enable 2FA to add an extra layer of protection to user accounts.
- Physical Security Measures: Implement physical safeguards, such as access control systems and security cameras, to prevent unauthorized access to devices and sensitive data.
Conclusion
Windows 10 security extends beyond Windows Defender. By implementing a comprehensive approach that encompasses firewalls, application control, device control, patch management, and user education, you can significantly enhance the security posture of your system. Stay vigilant, embrace best practices, and leverage the available tools to safeguard your data and protect against cyber threats.
Keyword Phrase Tags
- Windows 10 Security
- Windows Defender
- Firewall Protection
- Application Control
- Patch Management
- User Security Awareness

What a cunning guide! It’s like a roadmap to keeping your Windows 10 safe and sound. Defender’s guarding your digital castle, and there’s a whole battalion of other tools ready to charge into battle against any cyber threats. Thanks for the heads-up!
This write-up is as clear as mud! It’s like they tried to cram every security tip under the sun into one jumbled mess. I’m more confused than a lost puppy in a foggy forest. Can someone simplify this for me?
Fascinating insight! The author expertly weaves together fundamental Windows 10 security concepts, providing a comprehensive understanding of Defender’s role and the broader security landscape. This article deserves a standing ovation.
Hold your horses there, buckaroo! While I agree that Defender is a decent watchdog, let’s not forget the third-party security software out there. They often pack a bigger punch and offer more bells and whistles. Don’t limit yourself to just Defender!
Oh, how reassuring! Windows 10 security, the epitome of invincibility. It’s like putting up a cardboard box as a防线fense against a cyber army. Don’t delude yourself, folks!
Wow, mind-blowing stuff! So, Defender is the ultimate security solution, huh? Guess we can all go jump off a cliff and trust our precious Windows 10 to protect us from every cyber menace under the sun. Yeah, right!
Hold on to your hats, folks! Windows 10 security is like a cat chasing its tail—always running around but never quite catching it. Cybersecurity threats are evolving faster than a cheetah on Red Bull. Defender might be a good start, but don’t rely on it to keep your digital bacon safe. Stay vigilant, my friends!
This article is a treasure trove of security know-how! It’s like a beacon of light in the murky waters of cyber threats. Thanks to Defender and the other security measures, I feel like my Windows 10 is wrapped in a suit of impenetrable armor. Keep up the great work!
I’ve seen more convincing arguments in a toddlers’ debate. This article is nothing but a rehash of basic security tips that any tech-savvy person already knows. Defender is not the silver bullet they make it out to be. Stay skeptical, folks!
Well-researched and insightful piece! The author deftly navigates the complexities of Windows 10 security, providing actionable steps to enhance protection. I particularly appreciate the emphasis on multi-layered security strategies. A must-read for anyone concerned about safeguarding their digital assets.
This article ignited a burning passion within me! Windows 10 security has never been so clear and accessible. The author’s enthusiasm is contagious, inspiring me to take immediate action to protect my system. Defender, prepare to unleash your fury upon any cyber villains who dare to trespass!
Umm… what sorcery is this? I’m as lost as a baby bird in a hurricane. This article is like a cryptic puzzle that only a computer genius could decipher. Can someone please translate this into English for the rest of us mere mortals?
Proceed with caution, my friends. While this article touches on some important security measures, I have a sneaking suspicion that it may be painting an overly rosy picture. Don’t be lulled into a false sense of security. Remember, eternal vigilance is the price of digital safety.
Oh boy, here we go again! Another article telling us how Defender is the ultimate security solution. It’s like putting a Band-Aid on a broken leg. Sure, it might stop the bleeding for a while, but it’s not going to fix the underlying problem. Let’s get real, folks!