The Basics of Cryptography for Programmers
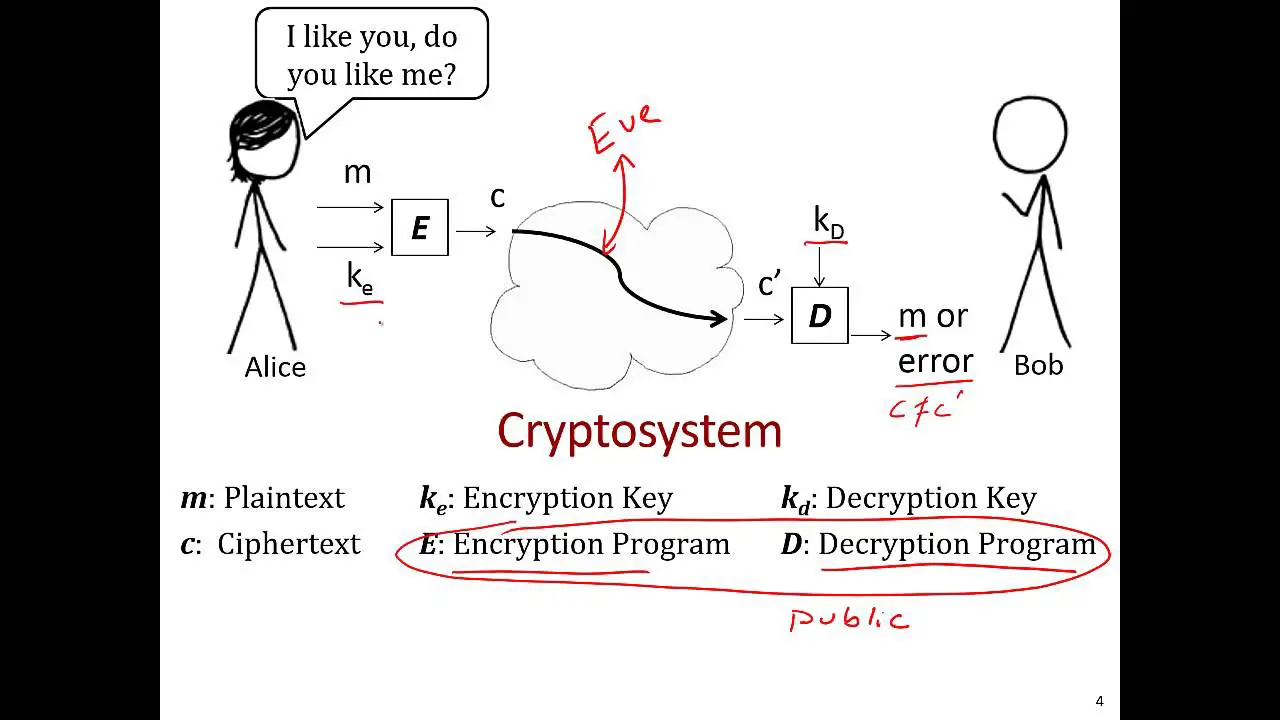
Cryptography is the practice of secure communication in the presence of adversarial behavior. Programmers engage with cryptography for reasons ranging from user authentication to secure data storage. The building blocks of cryptography include cryptographic hashes, symmetric-key encryption, public-key encryption, digital signatures, and random number generation. Mastery of these core primitive operations is essential for programmers working on cryptography-based applications.

A cryptographic hash function is a mathematical operation that takes an arbitrary block of data and produces a fixed-size hash value. Cryptographic hashes are often used to verify the integrity of data, as any change to the data will result in a different hash value. Common cryptographic hash functions include MD5, SHA-1, and SHA-256.

Symmetric-key encryption uses a single key to both encrypt and decrypt data. The key must be kept secret, and both the sender and receiver must have access to it. Symmetric-key encryption is computationally efficient, making it suitable for encrypting large amounts of data. Examples of symmetric-key encryption algorithms include AES, DES, and Triple DES.
Public-key encryption uses two keys: a public key and a private key. The public key is used to encrypt data, and the private key is used to decrypt it. The public key can be shared with anyone, but the private key must be kept secret. Public-key encryption is less computationally efficient than symmetric-key encryption, but it is more secure. Examples of public-key encryption algorithms include RSA, DSA, and ElGamal.
Digital signatures are used to verify the authenticity of a message. A digital signature is created using a private key, and it can be verified using the corresponding public key. Digital signatures are often used to sign contracts, emails, and other documents. Examples of digital signature algorithms include RSA, DSA, and ECDSA.
Random number generation is essential for cryptography. Random numbers are used to generate keys, create nonces, and add randomness to cryptographic operations. There are a variety of different ways to generate random numbers, and the choice of method depends on the specific application.
Understanding the basics of cryptography is essential for programmers working on cryptography-based applications. The core primitive operations of cryptography include cryptographic hashes, symmetric-key encryption, public-key encryption, digital signatures, and random number generation. Mastery of these operations is essential for building secure and reliable cryptographic systems.


This is a great article! I’ve been wanting to learn more about cryptography for a while now, and this article has given me a great overview of the basics. Thanks!
This article is terrible! It’s full of errors and it doesn’t explain anything clearly. I’m so frustrated!
This article is a good starting point for learning about cryptography. However, it doesn’t go into enough detail on some of the more complex topics. I would recommend reading a book or taking a course if you want to learn more.
I disagree with the author’s claim that symmetric-key algorithms are simple to implement. I think they can be quite complex, especially if you need to implement them in a secure way.
Ironic that an article about cryptography is full of errors.
This article is so full of jargon that it’s hard to understand. What does ‘asymmetric-key algorithm’ even mean?
Woof woof! I think cryptography is cool! Woof woof!
I’m not sure I understand what cryptography is. Can someone explain it to me in a way that a five-year-old can understand?
I think cryptography is really important. It helps to keep our information safe from hackers.
Tweet tweet! Cryptography is like a secret code that only the good guys can break! Tweet tweet!