Securing Digital Content with CDN Encryption and Tokenization
CDN Encryption

- Purpose: Encrypts sensitive data on a content delivery network (CDN) to prevent unauthorized access during storage and transfer.
- Process:
- Content is encrypted before being uploaded to the CDN.
- Encryption keys are managed by the CDN provider.
- When a user requests the content, the CDN decrypts it using the appropriate key.
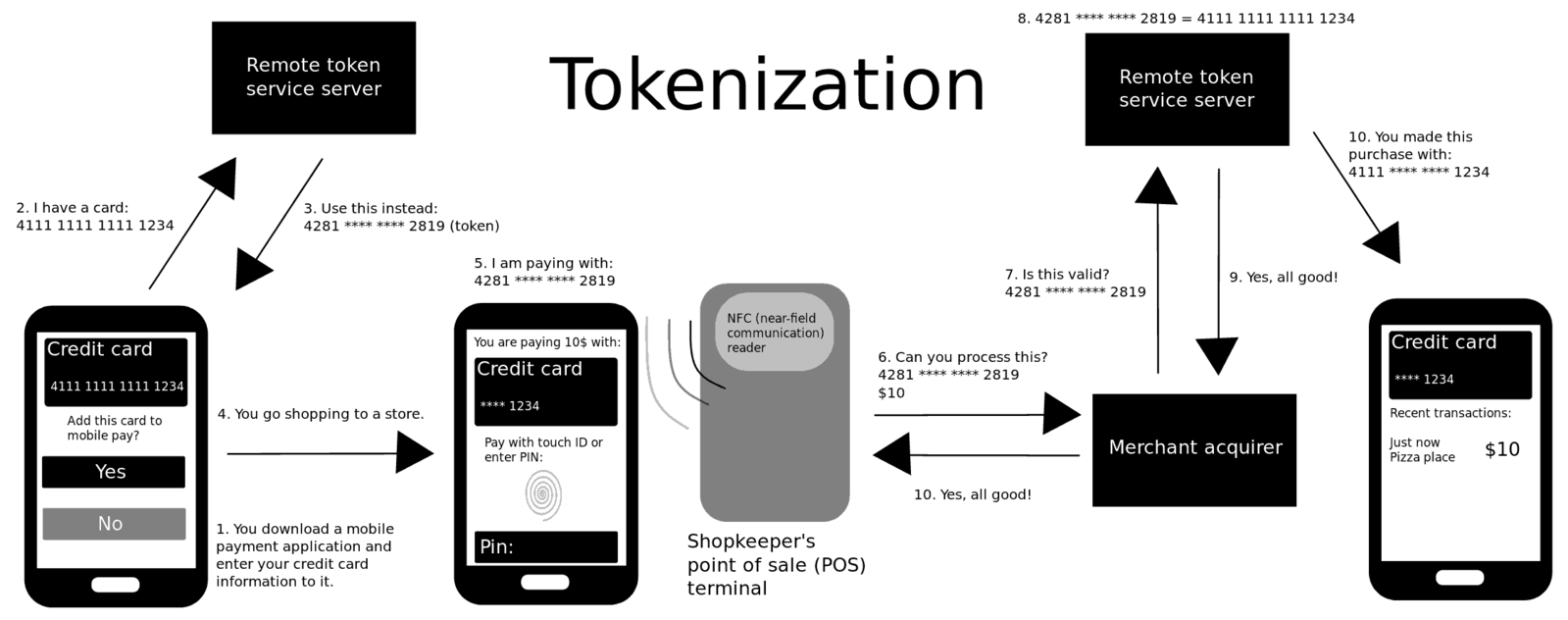
Tokenization

- Purpose: Replaces sensitive data with unique tokens that can be revoked or modified.
- Process:
- A key management system (KMS) generates a token and associates it with the original data.
- The original data is replaced with the token.
- When authorized users need to access the data, they present the token to the KMS, which provides the original data if the token is valid.
Benefits of Combining CDN Encryption and Tokenization
Enhanced Security:
- By using both encryption and tokenization, multiple layers of security are added to protect digital content.
- Unauthorized access is prevented at both the storage and delivery levels.
Performance Optimization:
- CDN encryption allows for efficient content delivery without compromising security.
- Tokenization reduces the need for costly and time-consuming re-encryption when data needs to be modified or revoked.
Regulatory Compliance:
- Both CDN encryption and tokenization meet various industry regulations and standards for data protection, such as GDPR and HIPAA.
Use Cases
- Streaming Media: Secure delivery of video and audio content on streaming platforms.
- E-commerce: Protection of customer data, such as credit card numbers and addresses.
- Healthcare: Encrypted storage and sharing of patient medical records.
- Financial Services: Secure delivery of sensitive financial information.
Implementation Considerations
- Key Management: Ensure secure storage and management of encryption keys.
- Token Expiry: Set appropriate expiry times for tokens to prevent unauthorized access after a certain period.
- Integration with Existing Systems: Integrate CDN encryption and tokenization seamlessly with existing content management and delivery systems.
- Performance Optimization: Monitor and optimize performance to ensure minimal impact on content delivery speed.
Conclusion
Combining CDN encryption and tokenization provides a robust and scalable solution for securing digital content. By leveraging multiple layers of protection, performance optimization, and regulatory compliance, organizations can protect sensitive data while delivering content efficiently to authorized users.## [Securing Digital Content Through CDN Encryption and Tokenization]
Executive Summary
Digital content providers face increasing challenges in protecting sensitive data from unauthorized access and distribution. Traditional encryption methods often prove insufficient, especially when dealing with large-scale content deliveries through Content Delivery Networks (CDNs). This article explores the benefits and implementation of two advanced security measures: CDN encryption and tokenization, providing a comprehensive solution for safeguarding digital content in the modern digital landscape.
Introduction
The proliferation of digital content distribution has created a pressing need for robust security measures to prevent unauthorized access, piracy, and data breaches. Traditional encryption techniques, while effective for small-scale applications, fall short in addressing the challenges of distributing large volumes of content through CDNs. To address these concerns, CDN encryption and tokenization emerged as innovative solutions, providing enhanced protection for digital content.
FAQs
1. What is CDN Encryption?
CDN encryption involves encrypting digital content at the CDN level, ensuring that it remains protected during transmission and storage. This mechanism prevents unauthorized parties from accessing the content even if they intercept it during transit.
2. How does Tokenization Work?
Tokenization involves replacing sensitive data with unique and non-identifiable tokens. These tokens can be used to access the original data but do not contain any inherent meaning or value outside the specific context they were created for.
3. What are the Advantages of Combining CDN Encryption and Tokenization?
Combining CDN encryption and tokenization provides a multi-layered approach to content security. CDN encryption safeguards the content during transit, while tokenization protects the sensitive data stored within the content itself. Together, they offer a comprehensive solution for preventing unauthorized access and data breaches.
Subtopics and Descriptions
1. CDN Encryption
CDN encryption involves encrypting digital content using industry-standard algorithms and storing the encrypted content on CDN servers. This process ensures that the content is secure during transmission and storage.
- Key Management: Robust key management systems are crucial for securing the encryption keys.
- Algorithm Selection: Choosing the right encryption algorithm, such as AES-256 or RSA, is essential for ensuring adequate protection.
- Cipher Block Chaining: CBC mode or other chaining modes ensure that each encrypted block depends on the previous one, enhancing security.
- Content Integrity: Digital signatures or hash values can verify the integrity of the encrypted content, preventing tampering.
2. Tokenization
Tokenization involves replacing sensitive data with non-identifiable tokens. These tokens can be used to access the original data but do not contain any inherent meaning or value outside the specific context they were created for.
- Token Generation: Strong token generation algorithms create unique and unpredictable tokens.
- Token Storage: Tokens should be stored securely and separately from the original data.
- Token Management: Efficient token management systems track and revoke tokens when necessary to prevent unauthorized access.
- Data Privacy: Tokenization effectively de-identifies sensitive data, ensuring privacy and compliance.
3. Content Delivery
Content delivery involves delivering encrypted content to end-users. This process must be optimized to ensure secure and reliable delivery.
- Secure Protocols: HTTPS or TLS protocols are essential for encrypting content during transmission.
- CDN Infrastructure: A robust CDN infrastructure with multiple points of presence ensures fast and reliable delivery.
- Caching Strategies: Effective caching strategies reduce latency and minimize the risk of unauthorized access.
- Access Control: Access control mechanisms restrict content delivery to authorized users only.
4. Security Management
Security management involves monitoring and maintaining the security of the CDN encryption and tokenization solution.
- Security Monitoring: Regular monitoring identifies vulnerabilities and security incidents.
- Incident Response: A comprehensive incident response plan ensures prompt resolution of security breaches.
- Compliance Monitoring: Compliance with industry standards and regulations, such as PCI DSS or GDPR, demonstrates commitment to data security.
- Security Audits: Periodic security audits validate the effectiveness of security measures.
5. Best Practices
Implementing CDN encryption and tokenization effectively requires adherence to best practices.
- Use Strong Encryption: Utilize industry-standard encryption algorithms and key management practices.
- Adopt Zero-Trust Approach: Minimize trust assumptions and implement robust access controls.
- Monitor and Audit Regularly: Continuously monitor the security of the solution and conduct regular audits.
- Stay Updated: Keep abreast of emerging security threats and industry best practices.
Conclusion
CDN encryption and tokenization, when combined, offer a comprehensive solution for securing digital content. By encrypting content during transmission and replacing sensitive data with non-identifiable tokens, these technologies provide robust protection against unauthorized access, piracy, and data breaches. As the digital content landscape continues to evolve, adopting these advanced security measures is crucial for protecting valuable content and maintaining stakeholder trust.
Keyword Tags
- CDN Encryption
- Tokenization
- Digital Content Security
- Data Protection
- Content Delivery Networks
