Reverse Engineering Testing
Executive Summary

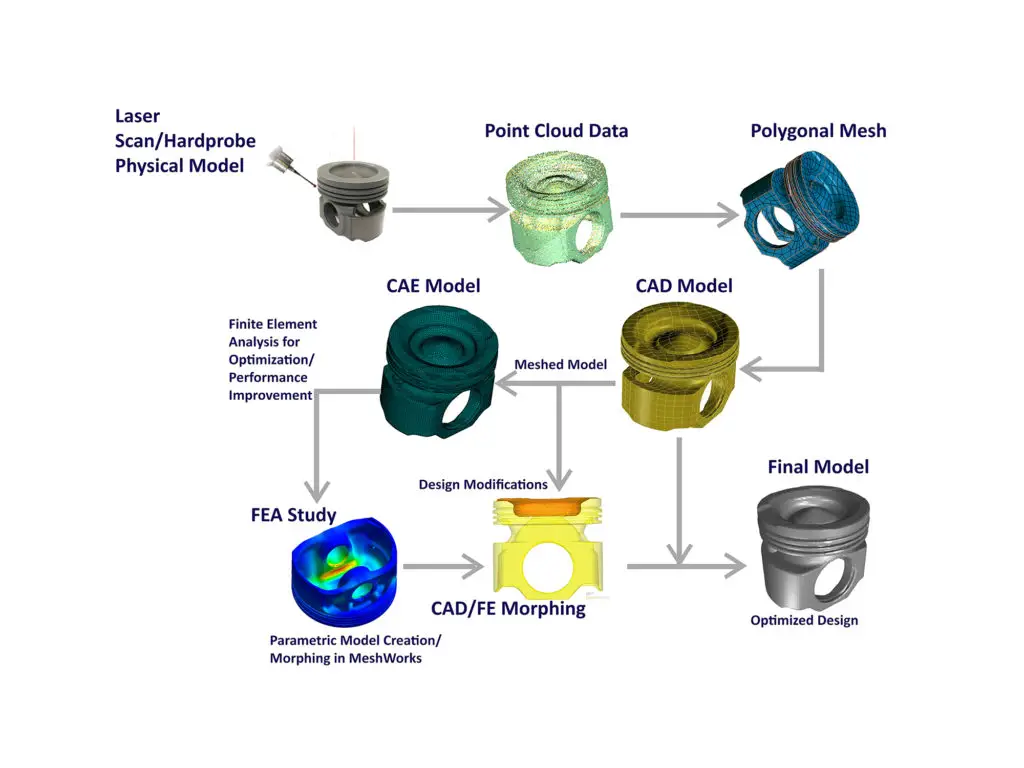
Reverse engineering testing is a crucial software testing technique that involves analyzing and understanding the internal workings of a software product without access to its source code. It enables testers to identify vulnerabilities, assess product quality, and gain valuable insights for further development and improvements. By thoroughly understanding the system’s architecture, functional behavior, and implementation details, reverse engineering testing empowers organizations to make informed decisions and enhance their software development processes.
Introduction
In today’s dynamic and competitive software industry, delivering high-quality software products is paramount. Reverse engineering testing has emerged as a powerful tool for software testing professionals to ensure software reliability, security, and performance. This comprehensive article delves into the world of reverse engineering testing, providing a detailed overview of its techniques, applications, and benefits.
FAQs
1. What is the primary purpose of reverse engineering testing?
Reverse engineering testing aims to provide a thorough understanding of the internal workings of a software product, helping testers identify potential weaknesses, security vulnerabilities, and areas for improvement.
2. What types of software are suitable for reverse engineering testing?
Reverse engineering testing can be applied to any software product, including commercial off-the-shelf (COTS) software, legacy systems, and proprietary software.
3. What are the key advantages of reverse engineering testing?
Reverse engineering testing offers several advantages, including improved software quality, enhanced security, reduced development costs, and accelerated troubleshooting.
Subtopics of Reverse Engineering Testing
1. Static Analysis
Static analysis involves examining a software product’s source code or compiled binary to identify potential errors, vulnerabilities, and code quality issues.
- Source Code Analysis: Reviews the actual source code to identify coding errors, security loopholes, and compliance violations.
- Bytecode Analysis: Analyzes compiled bytecode to uncover potential vulnerabilities and performance issues.
- Control Flow Analysis: Examines the flow of control within the software to detect logical errors and identify potential deadlocks.
2. Dynamic Analysis
Dynamic analysis involves executing the software and monitoring its behavior during runtime to identify errors, performance bottlenecks, and resource leaks.
- Code Coverage Analysis: Measures the extent to which different parts of the code are executed during testing, ensuring thorough testing.
- Runtime Error Detection: Monitors the software’s execution to detect runtime errors, crashes, and memory leaks.
- Performance Profiling: Analyzes the runtime behavior of the software to identify performance bottlenecks and resource utilization issues.
3. Binary Analysis
Binary analysis examines the compiled binary code of a software product to understand its structure, functionality, and dependencies.
- Reverse Assembling: Disassembles the binary code into assembly language, providing insights into the underlying assembly instructions.
- Symbol Resolution: Identifies and resolves symbolic references within the binary code, revealing the relationships between different code segments.
- Dependency Analysis: Discovers the dependencies of the binary on other libraries, frameworks, and operating system components.
4. API Testing
API testing focuses on evaluating the functionality, performance, and security of software interfaces used for communication between different components or applications.
- Functional Testing: Verifies the correctness of the API’s functionality and its ability to meet its intended purpose.
- Security Testing: Assesses the API’s vulnerability to security threats and identifies potential security risks.
- Performance Testing: Evaluates the API’s performance under various load conditions and identifies any bottlenecks or performance issues.
5. Data Mining
Data mining involves analyzing large volumes of software-related data to extract valuable insights, identify patterns, and uncover hidden relationships.
- Usage Analysis: Collects and analyzes data on how the software is used, providing insights into user behavior and identifying areas for improvement.
- Log File Analysis: Examines log files generated by the software to identify potential errors, performance issues, and security incidents.
- Database Analysis: Analyzes the software’s database to uncover data integrity issues, performance bottlenecks, and potential security vulnerabilities.
Conclusion
Reverse engineering testing is a comprehensive and multifaceted software testing technique that empowers organizations to thoroughly evaluate their software products. By understanding the internal workings, vulnerabilities, and performance characteristics of their software, organizations can make informed decisions for product development, risk management, and quality assurance. Reverse engineering testing enhances software security, improves reliability, accelerates troubleshooting, and ultimately contributes to the delivery of high-quality software products that meet the demands of the modern digital landscape.
Keyword Tags
- Reverse Engineering Testing
- Software Testing
- Static Analysis
- Dynamic Analysis
- Binary Analysis
