Reverse Engineering Software
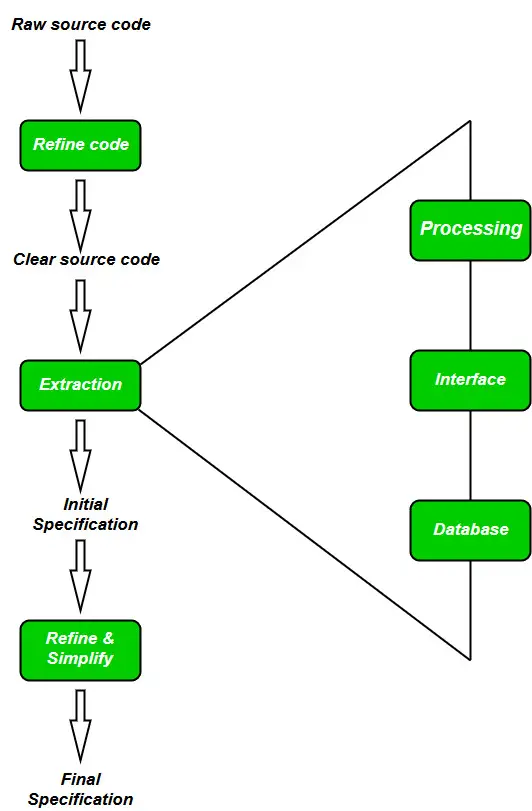
Reverse engineering software is a tool used to analyze and understand the inner workings of a particular software application. It allows developers to gain insights into the structure, functionality, and implementation of the software without accessing its original source code. This process is carried out by examining the compiled code or executable files generated by the software.
How Reverse Engineering Software Works:
Reverse engineering software typically works through a series of steps:
- Disassembly: Breaking down the executable code into assembly language, which is a lower-level representation of the machine instructions.
- Decompilation: Converting the assembly language back into a high-level programming language, such as C++, Java, or Python.
- Analysis: Examining the decompiled code to understand its structure, algorithms, data structures, and dependencies.
- Documentation: Generating reports and documentation based on the analysis results, providing detailed insights into the software’s design and implementation.
Uses of Reverse Engineering Software:
Reverse engineering software has various applications in software development, including:
- Security analysis: Identifying security vulnerabilities and weaknesses by examining the software’s codebase.
- Code optimization: Analyzing performance bottlenecks and identifying areas for code improvement.
- Competitor analysis: Studying and understanding the strategies and techniques used by competing software products.
- Legacy software maintenance: Extending and fixing older software applications for which source code is unavailable.
- Protocol analysis: Decoding and interpreting network communication protocols used by software applications.
Benefits of Reverse Engineering Software:
- Improved understanding: Gaining a deeper comprehension of the software’s architecture and implementation.
- Security enhancement: Identifying and addressing potential security risks and vulnerabilities.
- Code optimization: Enhancing the performance of software applications by optimizing code execution and memory usage.
- Competition analysis: Benchmarking and understanding the strengths and weaknesses of competing products.
- Legacy software support: Maintaining and updating older software systems without having to resort to costly rewrites.## Reverse Engineering Software
Executive Summary:
Reverse engineering software is an invaluable tool for businesses looking to gain a competitive edge. By breaking down existing software programs into their constituent parts, businesses can gain insights into design principles, uncover proprietary algorithms, and identify potential vulnerabilities. This advanced technique empowers businesses to make informed decisions, drive innovation, and enhance their products.
Introduction:
In today’s fast-paced digital landscape, reverse engineering software has become a crucial tool for businesses looking to stay ahead. This sophisticated process allows organizations to analyze and understand the inner workings of competitor’s software, providing valuable insights into their design, functionality, and potential security flaws. By leveraging reverse engineering techniques, businesses can gain strategic advantages and enhance their competitive positioning.
FAQ:
Q1. What is the purpose of reverse engineering software?
A1. Reverse engineering software is primarily used to analyze and understand the design, functionality, and underlying code of existing software programs. Businesses leverage this technique to extract valuable insights, identify vulnerabilities, and enhance their own development process.
Q2. What industries benefit the most from reverse engineering software?
A2. Reverse engineering finds applications in a wide range of industries, including cybersecurity, software development, and manufacturing. Businesses in these industries use this technique to analyze competitor’s products, enhance their existing systems, and improve product design.
Q3. What are the ethical implications of reverse engineering software?
A3. Reverse engineering falls under the larger umbrella of ethical hacking. While it is generally legal to reverse engineer software for non-malicious purposes, such as research or improving interoperability, it is crucial to respect intellectual property laws and avoid infringing on copyrights or patents.
Top 5 Subtopics:
1. Decompilation:
Decompilation is the process of converting compiled code back into its original source code. This allows businesses to understand the structure and logic of a software program and identify potential security vulnerabilities.
- Disassemblers: Break down compiled code into assembly language for analysis.
- Decompilers: Convert the assembly language further into a high-level language.
- Debugging: Identifying and fixing errors in the decompiled code.
2. Binary Analysis:
Binary analysis involves examining the raw binary code of a software program without converting it to source code. This technique is used to analyze low-level details and identify vulnerabilities that may not be apparent in the source code.
- Hex Editors: Allow users to view and modify binary files.
- Binary Disassemblers: Convert binary code into assembly language for analysis.
- Dynamic Analysis Tools: Observe and monitor the behavior of software during execution.
3. Dynamic Tracing:
Dynamic tracing involves monitoring the execution of a software program to identify its behavior, resource usage, and potential vulnerabilities. This technique helps pinpoint performance issues, memory leaks, or security flaws.
- Performance Monitoring Tools: Analyze resource consumption and identify bottlenecks.
- Call Trace Analysis: Track the sequence of function calls and identify potential issues.
- Memory Debugging Tools: Detect memory leaks and memory corruption vulnerabilities.
4. Vulnerability Assessment:
Reverse engineering techniques can be used to assess the security of a software program by identifying potential vulnerabilities and weaknesses. This proactive approach helps prevent security breaches and mitigate risks.
- Fuzz Testing: Subject the software to invalid or unexpected inputs to uncover vulnerabilities.
- Static Analysis Tools: Analyze the code for potential weaknesses without executing it.
- Dynamic Analysis Tools: Monitor the software behavior during execution to identify vulnerabilities.
5. Code Obfuscation:
Code obfuscation is the practice of intentionally making the code of a software program difficult to understand. This technique is used to protect intellectual property, prevent reverse engineering, and mitigate security threats.
- Encryption: Protects sensitive code segments by encrypting them.
- Dead Code Insertion: Add unnecessary or confusing code to the program.
- Control Flow Obfuscation: Modifies the flow of the program to make it difficult to follow.
Conclusion:
Reverse engineering software plays a vital role in the development, optimization, and security of software programs. By breaking down software into its components, businesses can unlock valuable insights, gain a competitive edge, and ensure the integrity of their systems. As technology continues to advance, reverse engineering software will remain an indispensable tool for businesses looking to thrive in the digital age.
Keyword Tags:
- Reverse Engineering
- Software Analysis
- Decompilation
- Binary Analysis
- Vulnerability Assessment
