Reverse Engineering Software
Reverse engineering software is a type of software tool that allows users to analyze and understand the behavior of existing software. It is used to create a detailed specification of the software, including its source code, data structures, and algorithms. This information can be used to create new software that is compatible with the existing software, or to improve the performance of the existing software.
There are many different types of reverse engineering software available, each with its own strengths and weaknesses. Some of the most popular reverse engineering tools include:
- IDA Pro is a powerful commercial tool that can be used to reverse engineer both 32-bit and 64-bit software. It supports a wide range of programming languages and architectures, and it has a number of features that make it easy to understand and debug complex code.
- Ghidra is a free and open-source reverse engineering tool that is developed by the National Security Agency (NSA). It is designed to be easy to use and understand, and it includes a number of features that make it ideal for beginners.
- Radare2 is a free and open-source reverse engineering framework that is designed to be modular and extensible. It includes a number of different tools that can be used to perform a variety of reverse engineering tasks, such as disassembling, debugging, and decompiling.
Reverse engineering software can be a valuable tool for developers who need to understand the behavior of existing software. It can be used to create new software that is compatible with the existing software, or to improve the performance of the existing software.# Reverse Engineering Software
Executive Summary
Reverse engineering software is a valuable tool for developers, researchers, and security professionals. It allows them to analyze and understand the inner workings of complex software systems and make informed decisions about how to interact with them. This can be essential for debugging, security testing, software maintenance, and more.
Introduction
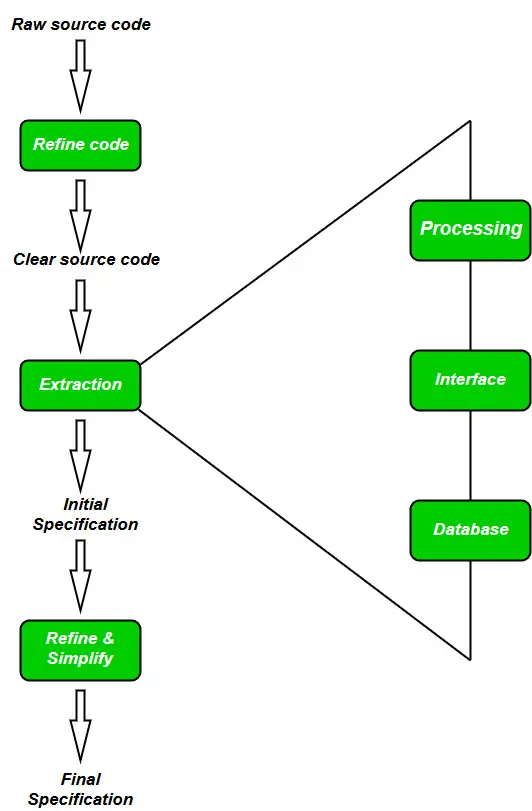
Reverse engineering software is the process of analyzing a software system to create a representation of its design and function. This can be done by examining the source code, binary code, or other artifacts of the software. The goal of reverse engineering is to understand how the software works, identify its components, and determine how they interact with each other.
FAQ
- What are the benefits of reverse engineering software?
- How can I get started with reverse engineering?
- What are some of the challenges of reverse engineering?
Subtopics
Decompilation
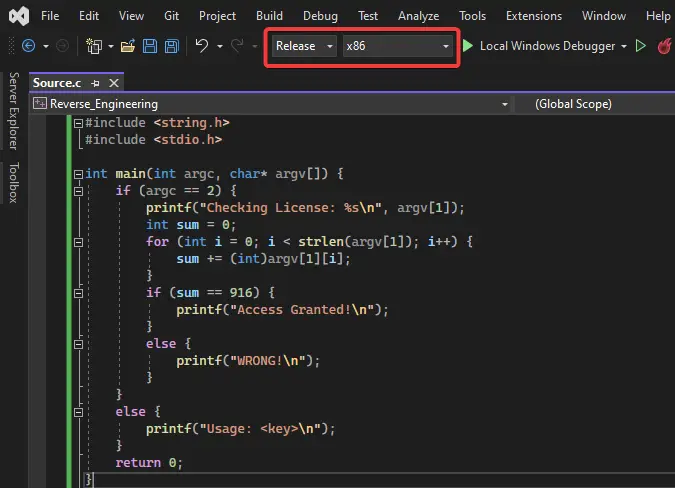
Decompilation is the process of converting compiled code back into human-readable source code. This is possible because compiled code is essentially a serialized representation of the source code. By using a decompiler, it is possible to recover the original source code, or at least a close approximation of it.
Important Pieces:
- Decompilers: Tools that convert compiled code back into source code
- Abstraction: Decompilers can recover the original source code, but they may not be able to recover all of the original abstractions
- Optimization: Decompilers may not be able to recover the original optimizations made by the compiler
- Debugging: Decompiled code can be useful for debugging purposes
- Security: Decompilation can be used to analyze malware and other malicious software
Disassembly
Disassembly is the process of converting machine code into assembly code. This is a more low-level process than decompilation, and it produces a more detailed representation of the code. Disassembly can be used to analyze the code at a very fine level of detail, and it can be useful for identifying security vulnerabilities.
Important Pieces:
- Disassemblers: Tools that convert machine code into assembly code
- Assembly language: A low-level programming language that is close to the machine code
- Machine instructions: The individual instructions that are executed by the CPU
- Opcode: The numeric code that represents an instruction
- Operand: The data that is operated on by an instruction
Dynamic Analysis
Dynamic analysis is the process of analyzing a software system while it is running. This can be done by using a variety of tools, such as debuggers, profilers, and code coverage tools. Dynamic analysis can provide insights into the behavior of the system at runtime, and it can be useful for identifying performance bottlenecks, memory leaks, and other issues.
Important Pieces:
- Debuggers: Tools that allow you to step through the code and examine the state of the system
- Profilers: Tools that collect data about the performance of the system
- Code coverage tools: Tools that measure how much of the code is executed
- Runtime behavior: The behavior of the system while it is running
- Performance bottlenecks: Areas of the code that slow down the system
Static Analysis
Static analysis is the process of analyzing a software system without executing it. This can be done by examining the source code, binary code, or other artifacts of the software. Static analysis can be used to identify a variety of issues, such as coding errors, security vulnerabilities, and design flaws.
Important Pieces:
- Static analysis tools: Tools that analyze code without executing it
- Coding errors: Errors in the code that can cause the system to crash
- Security vulnerabilities: Flaws in the code that can be exploited by attackers
- Design flaws: Inefficient or incorrect designs that can lead to problems
- Code reviews: Manual inspections of the code that can help to identify issues
Binary Analysis
Binary analysis is the process of analyzing the binary code of a software system. This is a more challenging task than analyzing source code, but it can be necessary in cases where the source code is not available. Binary analysis can be used to identify the components of the system, determine how they interact, and identify security vulnerabilities.
Important Pieces:
- Binary analysis tools: Tools that analyze binary code
- Binary code: The machine-readable code that is produced by the compiler
- Reverse engineering: The process of recovering the design and function of a system from its binary code
- Security analysis: The analysis of binary code to identify security vulnerabilities
- Malware analysis: The analysis of binary code to identify malware
Conclusion
Reverse engineering software is a powerful tool that can be used to analyze and understand complex software systems. It can be used for a variety of purposes, including debugging, security testing, software maintenance, and more. By understanding the inner workings of a software system, it is possible to make informed decisions about how to interact with it.
Keyword Tags
- reverse engineering
- decompilation
- disassembly
- dynamic analysis
- static analysis
