Reverse Engineering Security

Reverse engineering security is a process of examining an existing system to determine how it works and how it can be exploited. This can be done for a variety of reasons, such as to identify security vulnerabilities, to improve the security of a system, or to create a new system that is similar to an existing one.
There are a number of different techniques that can be used for reverse engineering security. These techniques include:
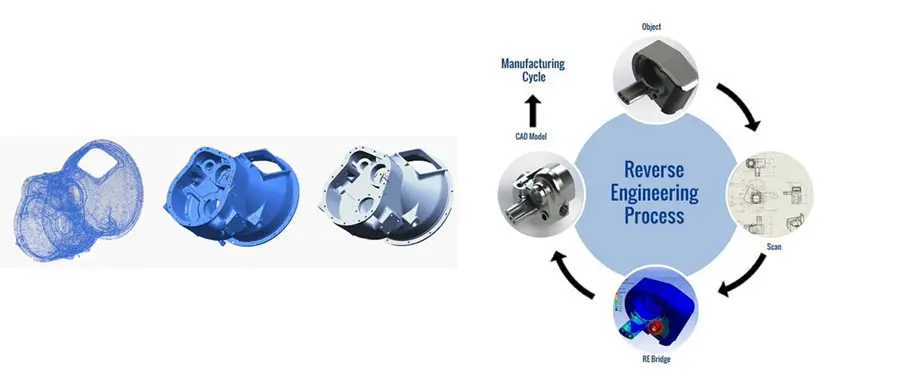
- Code analysis: This involves examining the code of a system to determine how it works. This can be done by using a variety of tools, such as disassemblers, decompilers, and debuggers.
- Network analysis: This involves examining the network traffic of a system to determine how it communicates with other systems. This can be done by using a variety of tools, such as packet sniffers and protocol analyzers.
- Hardware analysis: This involves examining the hardware of a system to determine how it works. This can be done by using a variety of tools, such as oscilloscopes, logic analyzers, and X-ray machines.
The results of a reverse engineering security analysis can be used to identify security vulnerabilities, to improve the security of a system, or to create a new system that is similar to an existing one.
Benefits of Reverse Engineering Security
There are a number of benefits to reverse engineering security. These benefits include:
- Identification of security vulnerabilities: Reverse engineering security can help to identify security vulnerabilities in a system. This information can then be used to patch the vulnerabilities and improve the security of the system.
- Improvement of security: Reverse engineering security can help to improve the security of a system by identifying and fixing security vulnerabilities. This can make the system more resistant to attacks.
- Creation of new systems: Reverse engineering security can be used to create new systems that are similar to existing ones. This can be useful for a variety of purposes, such as creating new versions of existing systems or creating systems that are tailored to specific needs.
Risks of Reverse Engineering Security
There are also some risks associated with reverse engineering security. These risks include:
- Breach of copyright: Reverse engineering security can violate copyright laws if the system being analyzed is copyrighted. This can result in legal action being taken against the person who performed the reverse engineering.
- Damage to the system: Reverse engineering security can damage the system being analyzed if it is not done properly. This can result in the loss of data or the inability to use the system.
- Unauthorized access: Reverse engineering security can be used to gain unauthorized access to a system. This can result in the theft of data or the disruption of the system.
It is important to weigh the benefits and risks of reverse engineering security before performing it. In some cases, the benefits of reverse engineering security outweigh the risks. In other cases, the risks of reverse engineering security outweigh the benefits.## Reverse Engineering Security
Executive Summary
Reverse engineering security involves examining software or hardware to understand its design, function, and potential vulnerabilities. This process can uncover exploitable flaws and inform defensive measures to safeguard systems and data. By delving into the inner workings of security mechanisms, analysts can identify and mitigate weaknesses, enhancing overall security posture and protecting against cyberattacks.
Introduction
In an era of pervasive cyber threats, bolstering security is paramount. Reverse engineering security techniques empower security professionals to dissect and scrutinize security measures, uncovering hidden vulnerabilities and proactively addressing them. This in-depth analysis enables organizations to stay ahead of malicious actors, ensuring the integrity of their systems and data.
FAQs
1. What are the benefits of reverse engineering security?
- Enhanced security by identifying exploitable weaknesses
- Proactive mitigation of vulnerabilities to prevent breaches
- Improved understanding of security mechanisms for effective implementation
2. What are the challenges of reverse engineering security?
- Complexity of modern software and hardware systems
- Time-consuming and labor-intensive process
- Requirement for skilled and experienced analysts
3. Who should consider using reverse engineering security techniques?
- Security professionals and analysts
- Developers and architects responsible for secure software or hardware design
- Organizations seeking to enhance their security posture
Subtopics in Reverse Engineering Security
Reverse Engineering Techniques
- Disassembly: Reconstructing source code from compiled or encrypted binaries
- Debugging: Analyzing code execution to identify vulnerabilities
- Symbolic execution: Evaluating code paths and identifying potential inputs that may trigger flaws
Vulnerability Analysis
- Static analysis: Examining code without executing it to find potential vulnerabilities
- Dynamic analysis: Executing code in a controlled environment to observe its behavior and identify runtime issues
- Fuzzing: Testing software with malformed inputs to trigger vulnerabilities
- Penetration testing: Simulating real-world attacks to assess security effectiveness
Exploitation Techniques
- Buffer overflow: Overstepping memory boundaries to execute malicious code
- SQL injection: Injecting malicious SQL queries to access or manipulate databases
- Cross-site scripting (XSS): Exploiting web applications to inject malicious client-side scripts
Security Hardening
- Code hardening: Modifying code to make it more resilient to attacks
- Encryption and authentication: Protecting data by encrypting it and using strong authentication mechanisms
- Intrusion detection and prevention systems (IDS/IPS): Monitoring networks and systems for suspicious activity and blocking attacks in real time
Remediation and Mitigation
- Patch management: Applying security patches to fix vulnerabilities
- Configuration hardening: Optimizing system and software settings to reduce attack surface
- Incident response and recovery: Establishing procedures for responding to and recovering from security incidents
Conclusion
Reverse engineering security is a crucial aspect of modern cybersecurity. By understanding how security measures function and uncovering potential vulnerabilities, organizations can strengthen their security posture and protect themselves against evolving cyber threats. Through continuous analysis and proactive remediation, reverse engineering security empowers enterprise to safeguard their systems and data, ensuring the integrity of their digital assets in the face of relentless cyberattacks.
Keyword Tags
- Reverse Engineering
- Security Analysis
- Vulnerability Assessment
- Exploit Techniques
- Security Hardening