Reverse Engineering Hardware

Reverse engineering hardware refers to the process of disassembling and analyzing a hardware device or system to understand its design, functionality, and operation. It involves the systematic examination of the device’s physical components, such as printed circuit boards, integrated circuits, and other electronic components.
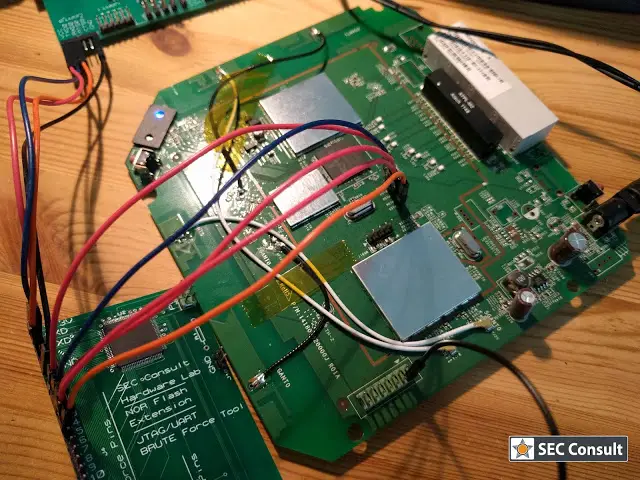
The primary purpose of reverse engineering hardware is to gain insights into the device’s inner workings and potentially modify or reproduce it. This process can be utilized for various reasons, including:

-
Product Optimization: Reverse engineering can help identify areas for improvement in existing hardware products, leading to enhanced performance or efficiency.
-
Hardware Design Verification: By reverse engineering their own or competitor’s hardware, manufacturers can validate the design’s accuracy and identify any potential issues.
-
Intellectual Property Protection: Analyzing the hardware of competitor’s products can provide insights into their design patents and help protect against infringement.
-
Hardware Cloning: In some cases, reverse engineering can lead to the unauthorized reproduction or cloning of a device, often for the purpose of manufacturing counterfeit products.
Reverse engineering hardware typically follows a series of steps, including:
-
Disassembly: The device is carefully disassembled into its individual components.
-
Component Analysis: Each component is examined and identified, including integrated circuits, transistors, resistors, and other components.
-
Schematic Capture: The connections between the components are documented to create a schematic diagram that represents the device’s circuitry.
-
Firmware Analysis: If the device includes firmware, it is extracted and analyzed to understand its functionality and interaction with the hardware.
-
Reconstruction: A detailed report is typically generated, summarizing the findings of the reverse engineering process and outlining any recommended modifications or improvements.## Reverse Engineering Hardware
Executive Summary
Hardware reverse engineering has become increasingly important in several domains, such as security, forensics, troubleshooting, and counterfeiting detection. Reverse engineering is the process of analyzing a product or device to discover its internal workings and design principles. With the rise of sophisticated hardware devices, being able to understand and manipulate hardware has become crucial to stay ahead in today’s competitive market. This comprehensive guide will provide an in-depth exploration of reverse engineering hardware, its applications, challenges, and best practices.
Introduction
For centuries, humans have been reverse engineering hardware to understand the inner workings of devices and machines. From early attempts at replicating mechanical clocks to the modern-day analysis of complex electronic systems, reverse engineering has played a significant role in technological advancements. In today’s fast-paced world, hardware reverse engineering has become essential in several different areas:
- Security: Understanding the hardware components of devices is critical for identifying and mitigating security vulnerabilities.
- Forensics: Reverse engineering hardware can provide invaluable insights during forensic investigations of electronic devices and systems.
- Troubleshooting: Analyzing hardware can help troubleshoot issues and identify root causes of system failures.
- Counterfeiting detection: Reverse engineering techniques can help identify and distinguish genuine products from counterfeit ones.
FAQs
Q: What are the different levels of hardware reverse engineering?
A: There are three main levels: Component analysis, which involves examining individual components, such as ICs and resistors; board analysis, which involves studying the connections and layout of a circuit board; and system analysis, which involves understanding the interactions between different components within a device.
Q: What are the challenges of hardware reverse engineering?
A: Some of the common challenges include lack of documentation, proprietary or custom hardware, complex and dense designs, and security measures designed to prevent reverse engineering.
Q: What tools are used in hardware reverse engineering?
A: A variety of tools are used, including microscopes, probes, logic analyzers, oscilloscopes, and software tools such as design verification tools and simulation software.
Top 5 Subtopics
1. Logic Analysis
Logic analysis involves analyzing digital signals to understand the behavior of hardware circuits. Tools such as logic analyzers and oscilloscopes are used to capture and interpret digital signals, allowing engineers to observe the sequence of events and identify potential issues.
- Types of logic analyzers
- Signal acquisition and analysis
- Timing diagrams and state machines
- Protocol decoding and emulation
2. Circuit Analysis
Circuit analysis is crucial for understanding the electrical behavior of hardware circuits. Circuit diagrams, schematics, and simulation tools are used to analyze the flow of current and voltage, identify components, and troubleshoot circuit malfunctions.
- Basic circuit theory and components
- Circuit simulation and modeling
- PCB layout and design
- Power distribution and noise analysis
3. Embedded Systems Analysis
Embedded systems are pervasive in modern devices, combining hardware and software to perform specific functions. Reverse engineering embedded systems requires a multidisciplinary approach, including understanding microcontrollers, firmware, and software-hardware interactions.
- Microcontroller architecture and instruction sets
- Embedded software analysis and debugging
- Bus protocols and communication interfaces
- Memory management and peripheral devices
4. Security Analysis
Hardware security analysis focuses on identifying vulnerabilities and mitigating security risks in hardware devices. Techniques such as fault injection, side-channel analysis, and reverse engineering of security mechanisms are used to assess the security posture of hardware systems.
- Cryptographic algorithms and implementations
- Side-channel attacks and countermeasures
- Fault injection and testing
- Malware analysis and detection
5. Counterfeit Detection
Counterfeit detection involves identifying and distinguishing genuine products from counterfeit ones. Reverse engineering techniques, such as component analysis, board examination, and supply chain analysis, are used to expose counterfeiting attempts and protect intellectual property.
- Component identification and verification
- PCB layout and design analysis
- Supply chain traceability
- Anti-counterfeiting technologies
Conclusion
Reverse engineering hardware has become an essential skill in various domains, providing valuable insights into device functionality, security, and reliability. This guide has provided a comprehensive overview of the field of hardware reverse engineering, covering its subtopics, challenges, and applications. By leveraging these techniques, engineers and researchers can gain a deeper understanding of hardware systems and pave the way for innovation and technological advancements.
Keyword Tags
- Hardware reverse engineering
- Logic analysis
- Circuit analysis
- Embedded systems
- Security analysis
