Reverse Engineering for Software Developers
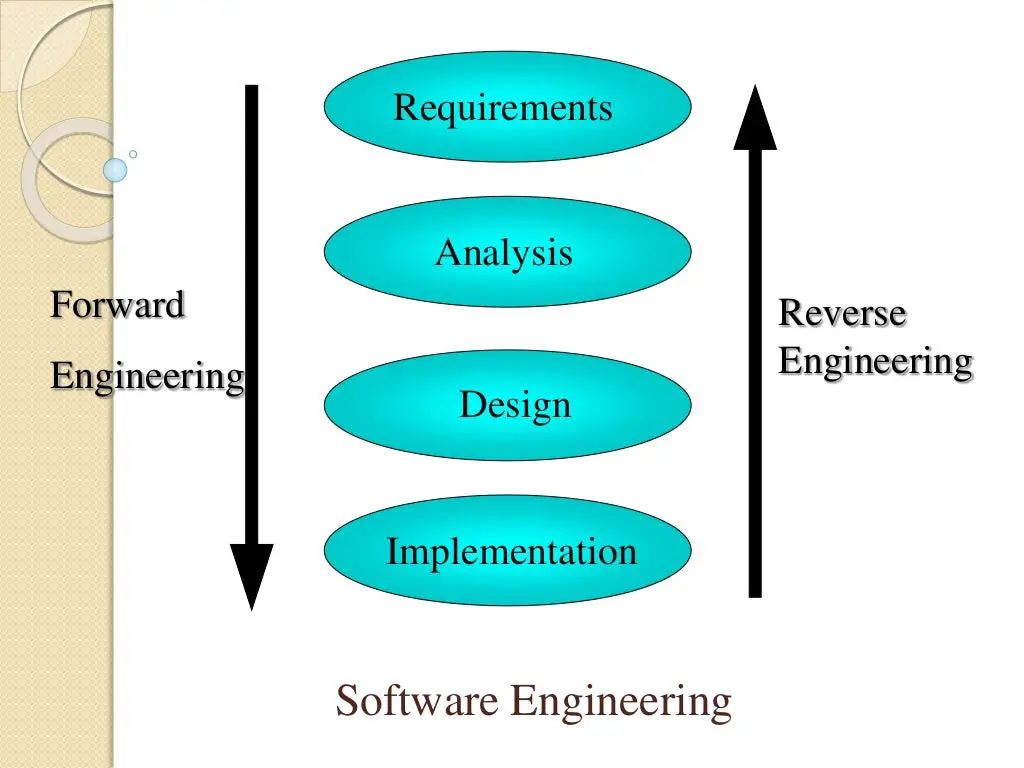
Reverse engineering is the process of analyzing a software product to create a new implementation with the same functionality. It is often used to understand the design and implementation of a complex system, or to create a new version of a software product that is compatible with the original.
There are many different techniques that can be used for reverse engineering, including:
- Static analysis: This involves examining the code of the software product to understand its structure and functionality.
- Dynamic analysis: This involves running the software product and monitoring its behavior to understand how it works.
- Hybrid analysis: This combines static and dynamic analysis techniques.
Reverse engineering can be a challenging process, but it can also be very rewarding. By understanding the design and implementation of a complex system, developers can create new software products that are more efficient, reliable, and secure.
Reasons to Reverse Engineer
There are many reasons why a software developer might want to reverse engineer a piece of software. Some of the most common reasons include:
- To understand how a software product works: Reverse engineering can help developers understand the design and implementation of a software product. This can be useful for a variety of reasons, such as:
- Troubleshooting problems with the software
- Improving the performance of the software
- Creating new features for the software
- To create a new version of a software product: Reverse engineering can be used to create a new version of a software product that is compatible with the original. This can be useful for a variety of reasons, such as:
- Adding new features to the software
- Improving the security of the software
- Making the software more portable
- To learn from the design and implementation of a software product: Reverse engineering can be a great way to learn about the design and implementation of a software product. This can be useful for a variety of reasons, such as:
- Improving your own software development skills
- Getting ideas for new software products
Challenges of Reverse Engineering
There are a number of challenges associated with reverse engineering. Some of the most common challenges include:
- Software complexity: Reverse engineering complex software can be a very difficult task. The code may be very large and complex, and it may be difficult to understand the relationships between different parts of the code.
- Lack of documentation: Many software products do not come with adequate documentation. This can make it difficult to understand the design and implementation of the software.
- Obfuscated code: Some software products are obfuscated, which makes it difficult to read and understand the code.
Benefits of Reverse Engineering
Despite the challenges, reverse engineering can offer a number of benefits. Some of the most common benefits include:
- Increased understanding of software: Reverse engineering can help developers gain a deeper understanding of the design and implementation of a software product. This can be useful for a variety of reasons, such as:
- Troubleshooting problems with the software
- Improving the performance of the software
- Creating new features for the software
- Improved software security: Reverse engineering can help developers identify security vulnerabilities in software. This can help to improve the security of the software and protect it from attacks.
- New ideas for software products: Reverse engineering can help developers get ideas for new software products. This can lead to the development of new and innovative software products that meet the needs of users.## [Reverse Engineering For Software Developers]
Executive Summary
Software Reverse Engineering is the process of understanding and analyzing an already existing software or system’s structure, behavior, and design. The process usually begins with disassembled machine code and produces a high-level description using the source code and design documentation. Reverse engineering plays an important role in various fields of Computer Science in areas including; malware analysis, vulnerability assessment, security assessment, program comprehension, legacy systems migration, recovery of lost source code, and patent infringement analysis.
Introduction
Reverse engineering is a multi-faceted process that has historically been used for various reasons. Initially developed as a way to understand and exploit enemy technology during wartime, reverse engineering is now used even more frequently for commercial and non-malicious purposes, including software development. The following article will serve as an introduction to reverse engineering for software developers to use while working in the field. This is not an exhaustive guide to the entire reverse engineering process, but rather an introduction to the basic concepts involved in the field. After reading this article, software developers should have a fundamental understanding of the reverse engineering process, including specific techniques and tools used in the field of software development.
FAQ
Q: What are some of the main benefits of reverse engineering?
A: 1. It can be used to understand how complex code works. 2. It can be used to troubleshoot and debug code. 3. It can be used to find vulnerabilities in code. 4. It can be used to create new features for existing code. 5. It can be used to port code to new platforms.
Q: What are some of the challenges of reverse engineering?
A: 1. It can be time-consuming to reverse engineer large and complex programs. 2. It can be difficult to understand the intent of the original code. 3. There may not be adequate documentation to guide the reverse engineering process. 4. The original code may be obfuscated or encrypted to make it harder to understand. 5. Reverse engineering can be error-prone, and if done incorrectly, it can produce incorrect results.
Q: What is the difference between static and dynamic reverse engineering?
A: Static reverse engineering is performed on a program’s source code, while dynamic reverse engineering is performed on a running program. Static reverse engineering can be used to identify the structure, behavior, and design of a program. Dynamic reverse engineering can be used to understand how a program behaves while running and can be used to identify performance problems.
Tooling
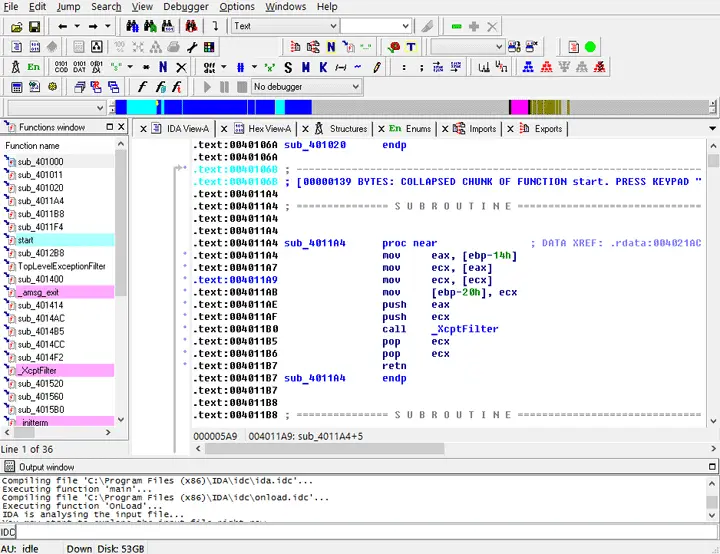
1. Debuggers
Debuggers are software tools that allow a developer to step through a program’s code line-by-line while it is running. This allows the developer to see how the program is executing and can be used to identify errors and performance problems.
2. Disassemblers
Disassemblers are software tools that convert machine code into assembly code. This allows the developer to see the actual instructions that the program is executing. Disassemblers can be used to identify the structure and behavior of a program.
3. Hex Editors
Hex editors are software tools that allow the developer to view and edit the raw binary data of a program. This can be useful for finding hidden data or for modifying the program’s behavior.
4. Symbolic Debugger
This tool allows users to map assembly instructions to their original source code, enabling more convenient debugging and analysis of the code.
Intermediate Language (IL) Generators
1. Compilers and Interpreters
Compilers are software tools that convert source code into machine code. Interpreters are software tools that execute source code directly. IL generators can be used to generate intermediate code that can make reverse engineering easier.
2. Code Coverage Tools
Many code coverage tools are designed to point out sections of a codebase that aren’t executed during runtime. This allows reverse engineers to focus their efforts on analyzing code that is actually being executed.
Decompilers
1. Java Decompiler
The Java decompiler parses Java bytecode and translates it back into readable Java source code. This enables developers to see how Java bytecode maps to its original source.
2. .NET Reflector
.NET Reflector is a tool for disassembling .NET assemblies into Intermediate Language (IL). The tool also enables users to see the original source code for the assembly, making it easier to reverse engineer .NET applications.
3. Ghidra
Ghidra is a software reverse engineering framework used to analyze compiled code from various platforms. It includes a disassembler, a decompiler, a graphical user interface, and numerous plugins to aid reverse engineers.
Languages
1. Assembly Language
Assembly language is a low-level programming language that is close to the machine code that the computer executes. Assembly language is often used for reverse engineering because it allows the developer to see the actual instructions that the program is executing.
2. Intermediate Language
Intermediate language is a language that is generated by a compiler or interpreter. Intermediate language is often easier to read and understand than machine code. Intermediate languagecan be used for reverse engineering because it allows the developer to see the structure and behavior of the program at a higher level than machine code.
Conclusion
Reverse engineering is a powerful technique that can be used for a variety of purposes. It is important to understand the basics of reverse engineering before attempting to use it. The above five topics provide a good overview of relevant topics within the domain of reverse engineering for software development. More information and detailed guides can be found by searching online, reading books, and consulting with knowledgeable software development professionals or experts.
Keyword Tags
- Reverse engineering
- Software development
- Debugging
- Decompilers
- Intermediate Language
