Reverse Engineering for Networked Systems
Executive Summary
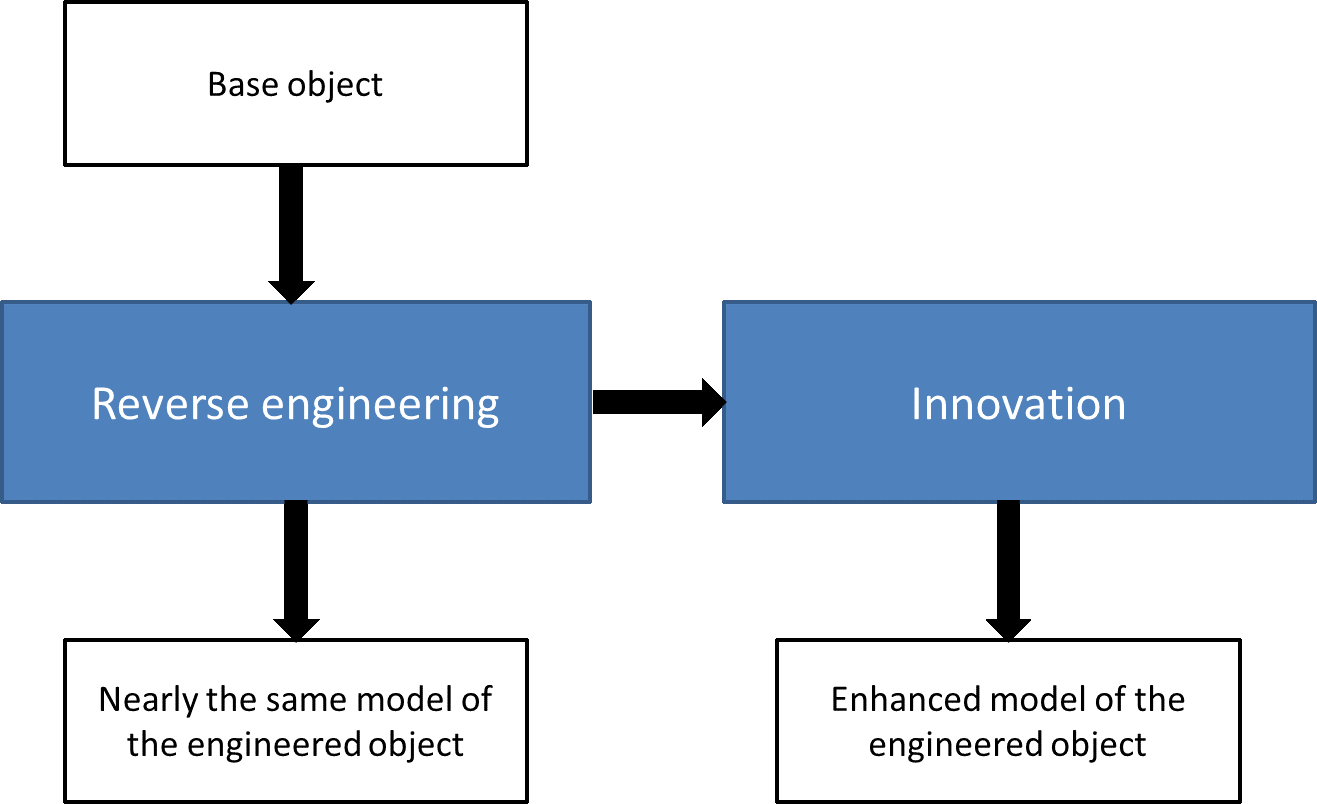
Reverse engineering is a valuable technique that enables organizations to analyze and understand the design and implementation of existing networked systems. By breaking down complex systems into their constituent components, organizations can gain valuable insights into the strengths, weaknesses, and potential vulnerabilities of these systems. This detailed assessment empowers them to make informed decisions regarding system enhancements, security improvements, and compatibility upgrades, ensuring optimal performance and enhanced operational efficiency.

Introduction
Reverse engineering plays a crucial role in the ever-evolving landscape of network systems. As organizations seek to leverage existing systems while navigating an increasingly complex technological environment, the need for a thorough understanding of these systems becomes paramount. Reverse engineering provides the necessary foundation to decipher the intricate workings of these systems, informing strategic decisions and empowering organizations to adapt and innovate in a rapidly changing landscape.
Frequently Asked Questions (FAQs)
Q: What is the primary benefit of reverse engineering networked systems?
A: Reverse engineering allows organizations to gain a comprehensive understanding of existing systems, enabling them to identify areas for improvement, address potential vulnerabilities, and enhance system functionality.
Q: What industries or sectors can benefit from reverse engineering?
A: Reverse engineering finds application in various industries, including software development, cybersecurity, telecommunications, and manufacturing, where analyzing and understanding existing systems is crucial for innovation and progress.
Q: Are there any ethical considerations associated with reverse engineering?
A: Ethical guidelines should be strictly adhered to during reverse engineering processes. Organizations must ensure that they possess the necessary licenses or permissions to access and analyze proprietary systems.
Top Five Subtopics in Reverse Engineering for Networked Systems
1. Protocol Analysis
- Captures and decodes network traffic to identify protocols and communication patterns.
- Identifies potential vulnerabilities and performance bottlenecks within network protocols.
- Provides insights into the structure, functionality, and security measures employed by network protocols.
2. Software Analysis
- Disassembles compiled code to reveal the underlying instructions and logic.
- Facilitates understanding of software behavior, identifying potential flaws or weaknesses.
- Enables the identification of undocumented features or hidden functionality within software.
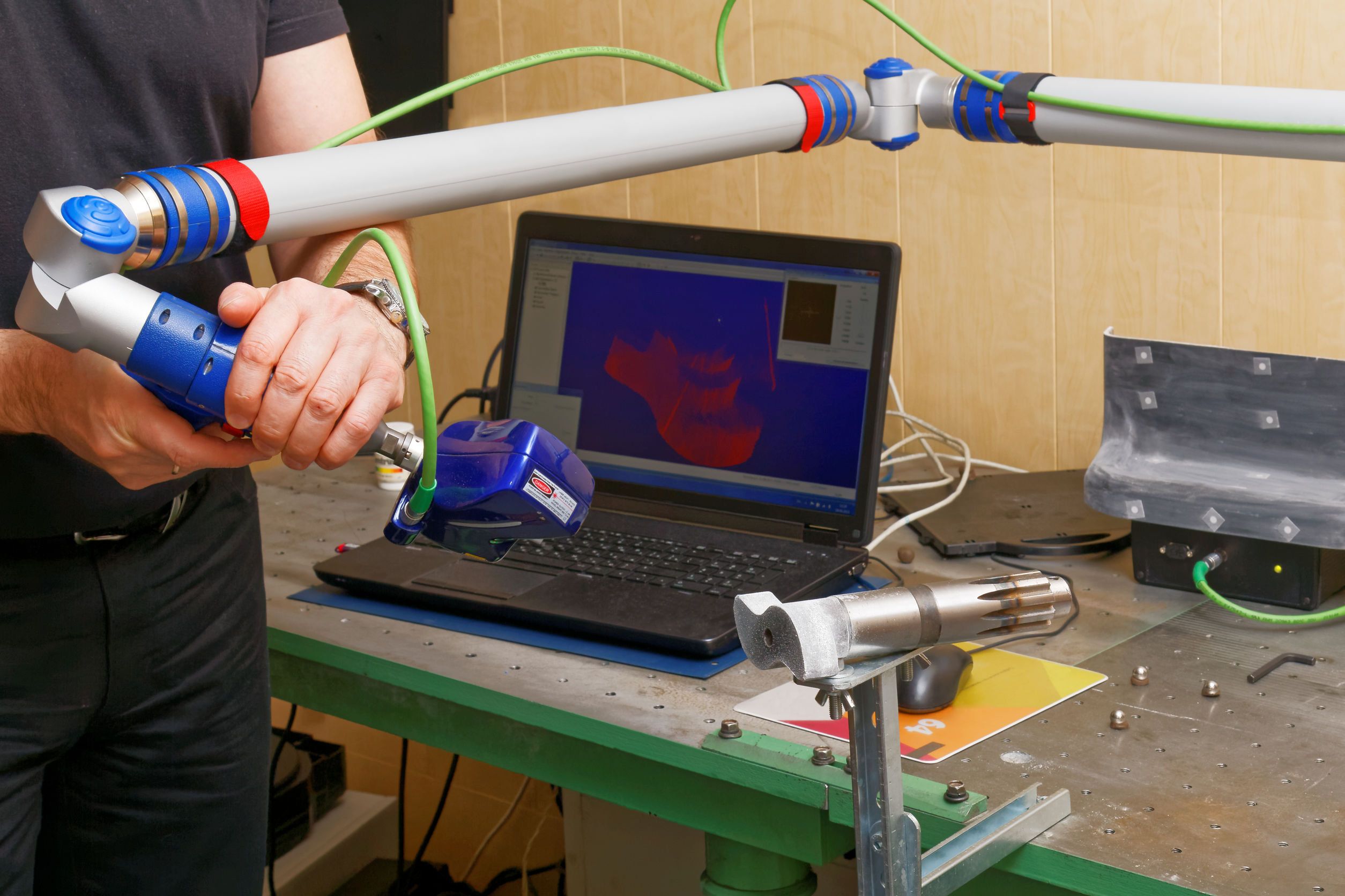
3. Hardware Analysis
- Examines physical components, such as circuit boards and chips, to determine their design and functionality.
- Identifies hardware vulnerabilities, performance limitations, and compatibility issues.
- Supports the development of customized hardware solutions or the integration of existing hardware into new systems.
4. Documentation Discovery
- Recovers or reconstructs lost or incomplete documentation for existing systems.
- Facilitates understanding of system requirements, design principles, and operational procedures.
- Enhances communication and collaboration among stakeholders involved in system maintenance and upgrades.
5. Legacy System Migration
- Supports the transition of outdated systems to newer platforms or technologies.
- Analyzes legacy systems to identify dependencies, data structures, and compatibility issues.
- Ensures smooth migration of critical data and functionality, minimizing disruption to business operations.
Conclusion
Reverse engineering is a powerful technique that empowers organizations to gain a comprehensive understanding of existing networked systems. By breaking down complex systems into their constituent components, reverse engineering enables organizations to identify areas for improvement, address potential vulnerabilities, and enhance system functionality. As the technological landscape continues to evolve, the ability to reverse engineer networked systems will remain a valuable asset for organizations seeking to innovate, adapt, and maintain a competitive edge.
Relevant Keyword Tags
- Reverse engineering
- Networked systems
- Protocol analysis
- Software analysis
- Legacy system migration

