Reverse Engineering for Mobile Systems
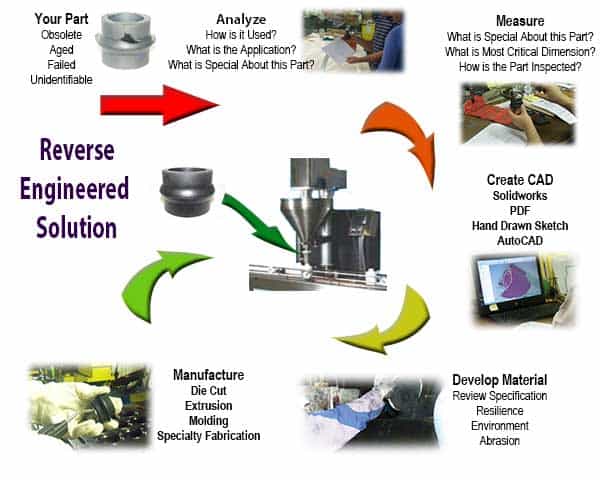
Reverse engineering is the process of analyzing a system to determine how it works. This can be done by examining the system’s code, design, and documentation. Reverse engineering can be used for a variety of purposes, such as:
- To understand the functionality of a system
- To identify vulnerabilities in a system
- To create new products and services
- To improve the performance of a system
Reverse engineering mobile systems can be a challenging task, as these systems are often complex and proprietary. However, there are a number of tools and techniques that can be used to make the process easier.
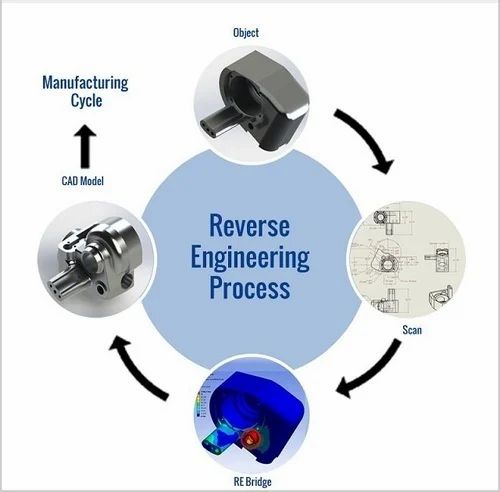
One of the most important tools for reverse engineering mobile systems is a disassembler. A disassembler is a program that takes machine code and converts it into assembly code. This can make it much easier to understand the functionality of a system.
Another important tool for reverse engineering mobile systems is a debugger. A debugger is a program that allows you to step through the code of a system and examine the state of the system at each step. This can be very helpful for understanding how a system works and for identifying bugs.
In addition to these tools, there are also a number of online resources that can be used for reverse engineering mobile systems. These resources can provide information on the architecture of mobile systems, the different types of mobile applications, and the tools and techniques used for reverse engineering mobile systems.
Reverse engineering mobile systems can be a complex and challenging task, but it can also be a very rewarding one. By understanding how mobile systems work, you can identify vulnerabilities, create new products and services, and improve the performance of existing systems.## Reverse Engineering for Mobile Systems
Executive Summary
Reverse engineering is a powerful technique used to analyze and understand mobile systems, enabling developers to gain insights into how they function and identify potential vulnerabilities. This article provides a comprehensive guide to reverse engineering for mobile systems, covering key concepts, techniques, and tools. By understanding the principles of reverse engineering, developers can enhance the security, performance, and functionality of their mobile applications.
Introduction
Reverse engineering is the process of analyzing a software system to understand its design, implementation, and behavior. This information can be used for a variety of purposes, such as security analysis, vulnerability detection, performance optimization, and feature enhancement. Reverse engineering mobile systems presents unique challenges due to the complexity of mobile operating systems, the diversity of mobile devices, and the often proprietary nature of mobile applications.
FAQs
What is the difference between static and dynamic analysis in reverse engineering?
- Static analysis examines the code of a mobile application without executing it, while dynamic analysis involves executing the application and monitoring its behavior in real time.
What are the benefits of using tools for reverse engineering mobile systems?
- Tools can automate repetitive tasks, accelerate the analysis process, and provide specialized features for extracting insights from mobile applications.
What are some common challenges in reverse engineering mobile systems?
- Challenges include dealing with platform-specific technologies, encryption mechanisms, and complex software architectures.
Key Subtopics
1. Decompilation
Decompilation is the process of converting compiled machine code back into high-level source code. This allows developers to analyze the original logic and structure of the application.
- Decompilers for Android: JADX, Procyon, Baleen
- Decompilers for iOS: Hopper, IDA Pro, Ghidra
2. Disassembly
Disassembly is the process of converting machine code into human-readable assembly language. This provides a low-level view of the application’s instructions and data structures.
- Disassemblers for Android: Exodus, radare2, IDA Pro
- Disassemblers for iOS: IDA Pro, Ghidra, Hoppers
3. Debugging and Tracing
Debugging and tracing techniques allow developers to execute mobile applications in a controlled environment and monitor their behavior in real time. This helps identify errors, understand program flow, and analyze system calls.
- Debuggers for Android: Android Studio, Eclipse, GDB
- Debuggers for iOS: Xcode, Instruments, LLDB
4. Memory Analysis
Memory analysis involves examining the memory of a running mobile application. This can provide insights into data structures, memory leaks, and potential security vulnerabilities.
- Memory analysis tools for Android: MAT, LEAKCANARY, MEMORYPROFILER
- Memory analysis tools for iOS: Instruments, LLDB, Reveal
5. Network Analysis
Network analysis monitors the network traffic generated by a mobile application. This helps identify endpoints, communication patterns, and potential network vulnerabilities.
- Network analysis tools for Android: Wireshark, tcpdump, Fiddler
- Network analysis tools for iOS: Charles Proxy, HTTP Toolkit, Appcelerator Titanium Network Logger
Conclusion
Reverse engineering is a powerful technique that provides valuable insights into the design and behavior of mobile systems. By understanding the principles and techniques of reverse engineering, developers can improve the security, performance, and functionality of their mobile applications. This article has provided a comprehensive guide to reverse engineering for mobile systems, covering key concepts, subtopics, and tools.
Keyword Tags
- Mobile System Reverse Engineering
- Android Reverse Engineering
- iOS Reverse Engineering
- Decompilation
- Disassembly
- Debugging
- Memory Analysis
- Network Analysis
