Reverse Engineering For Intelligence Agencies
Executive Summary
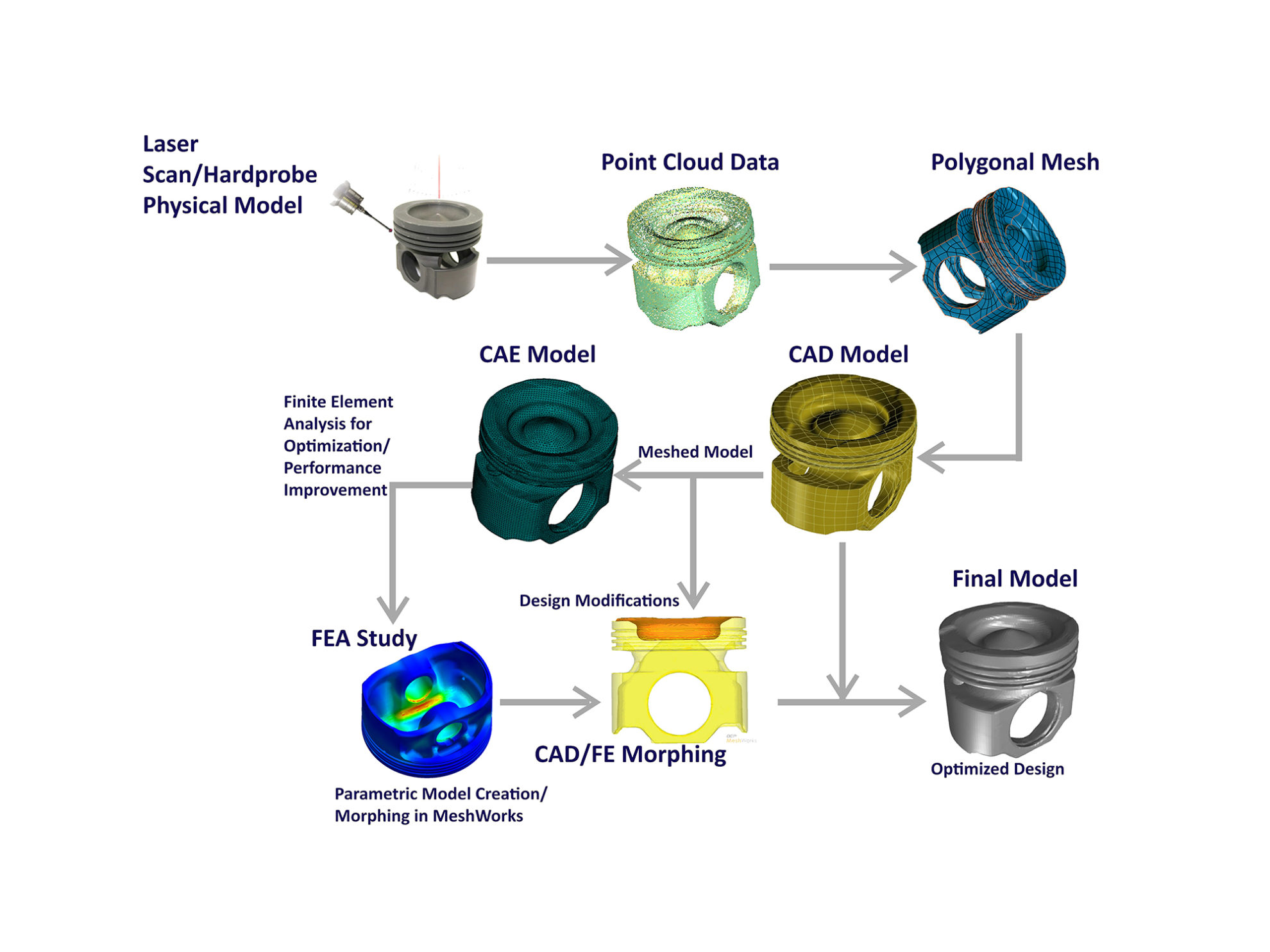
Reverse engineering is a valuable tool for intelligence agencies because it allows them to gain insights into the capabilities and weaknesses of potential adversaries. This article will provide an overview and key benefits of reverse engineering, and will explore its potential applications in the field of intelligence gathering.
Introduction
Reverse engineering is the process of disassembling a device or system to study its design and function. This information can then be used to create a replica of the device or system, or to gain insights into its operation. Reverse engineering is a powerful tool for intelligence agencies because it can provide valuable information about the capabilities and weaknesses of potential adversaries.
FAQs
What are the main benefits of reverse engineering for intelligence agencies?
- Gaining insights into the design and function of foreign weapons systems. This information can be used to develop countermeasures against these systems or to exploit their vulnerabilities.
- Identifying potential threats. By understanding the capabilities of foreign weapons systems, intelligence agencies can assess the potential threats that they pose to national security interests.
- Developing new technologies. Reverse engineering can be used to develop new technologies based on the design of foreign weapons systems.
What are some of the potential applications of reverse engineering in the field of intelligence gathering?
- Disarmament verification. Reverse engineering can be used to verify the compliance of foreign states with arms control agreements.
- Counterterrorism. Reverse engineering can be used to identify the source of terrorist weapons and to develop countermeasures against terrorist threats.
- Cybersecurity. Reverse engineering can be used to identify vulnerabilities in software and hardware systems and to develop defenses against cyberattacks.
Subtopics
1. Reverse Engineering Process
The reverse engineering process typically involves the following steps:
- Disassembly. The device or system is disassembled into its component parts.
- Analysis. The component parts are analyzed to determine their function and how they interact with each other.
- Documentation. The results of the analysis are documented in a report or database.
2. Reverse Engineering Applications
Reverse engineering can be used in a variety of applications, including:
- Product development. Reverse engineering can be used to develop new products based on the design of existing products.
- Quality control. Reverse engineering can be used to identify defects in products and to improve the quality of manufacturing processes.
- Forensics. Reverse engineering can be used to investigate accidents and to determine the cause of failures.
3. Legal and Ethical Issues
Reverse engineering is a legal process in most countries, but there are some ethical issues that should be considered. For example, it is important to respect the intellectual property rights of the original designer of the device or system.
4. Tools and Techniques
A variety of tools and techniques can be used for reverse engineering, including:
- X-rays. X-rays can be used to visualize the internal structure of a device or system.
- Computer-aided design (CAD) software. CAD software can be used to create 3D models of devices or systems.
- Microprobes. Microprobes can be used to analyze the electrical signals in a device or system.
5. Future Trends
The future of reverse engineering is bright. As new technologies emerge, new opportunities will arise for the use of reverse engineering in intelligence gathering and other applications.
Conclusion
Reverse engineering is a valuable tool for intelligence agencies because it provides valuable information about the capabilities and weaknesses of potential adversaries. This information can be used to develop countermeasures against these systems, to identify potential threats, and to develop new technologies. As new technologies emerge, new opportunities will arise for the use of reverse engineering in intelligence gathering and other applications.
Keyword Tags
- reverse engineering
- intelligence gathering
- national security
- product development
- cybercrime
