Reverse Engineering for Distributed Systems

Reverse engineering is the process of analyzing a system to create a representation of its design and implementation. This can be done for a variety of reasons, such as to understand how the system works, to identify potential security vulnerabilities, or to create a new system that is compatible with the existing one.

Reverse engineering distributed systems is a challenging task, as these systems are often complex and dynamic. However, there are a number of tools and techniques that can be used to make the process easier.
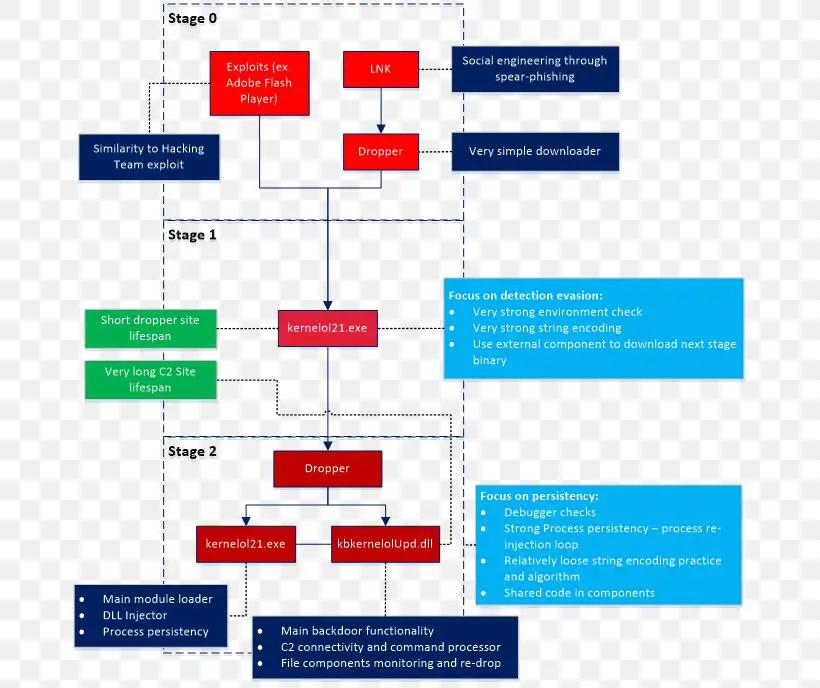
One common approach to reverse engineering distributed systems is to use a system tapping tool. These tools allow you to monitor the network traffic between the components of the system, which can give you a good understanding of how the system works.
Another approach is to use a decompiler. These tools allow you to convert the compiled code of the system into a more human-readable format, which can make it easier to understand the design and implementation of the system.
Once you have a good understanding of how the system works, you can begin to create a representation of its design and implementation. This representation can be used for a variety of purposes, such as:
- Creating documentation for the system
- Identifying potential security vulnerabilities
- Creating a new system that is compatible with the existing one
Reverse engineering distributed systems is a complex and challenging task, but it can be a valuable tool for understanding how these systems work and for creating new systems that are compatible with them.## Reverse Engineering for Distributed Systems
Executive Summary
Reverse engineering distributed systems aids organizations in understanding the intricacies and patterns of their software architecture. By gaining insights into the behaviors, properties, and constraints that govern these systems, organizations can make informed decisions about their future development and maintenance. This in-depth guide delves into the essential concepts and methodologies of reverse engineering distributed systems, providing a comprehensive roadmap for successful implementation.
Introduction
Distributed systems encompass diverse components and services interoperating across a network, presenting challenges in comprehending their intricate behavior. Reverse engineering provides a systematic approach to unraveling this complexity, enabling organizations to not only decipher the system’s current state but also to discern its underlying design principles. By leveraging this knowledge, organizations can optimize system performance, enhance security, and facilitate future enhancements with greater confidence.
FAQs
-
What are the benefits of reverse engineering distributed systems?
- Comprehend system architecture and interdependencies
- Identify potential vulnerabilities and security risks
- Facilitate system upgrades and maintenance
- Provide documentation for existing undocumented systems
-
What are the challenges of reverse engineering distributed systems?
- Collecting accurate and complete data from multiple system components
- Dealing with system complexity and scale
- Potential performance impact during the reverse engineering process
-
How can I ensure the accuracy and integrity of the reverse-engineered model?
- Use multiple data sources and validation techniques
- Consult with domain experts and system architects
- Perform rigorous testing and verification
Subtopics in Reverse Engineering
Communication Analysis
- Protocol Identification: Identify the communication protocols used by the distributed system’s components.
- Message Analysis: Analyze the structure and content of messages exchanged between components.
- Traffic Patterns: Examine the frequency, direction, and volume of messages flowing through the system.
Component Analysis
- Service Discovery Mechanisms: Determine how components discover each other and establish connections.
- Component Interfaces: Analyze the public interfaces of components to understand their externally exposed functionality.
- Dependency Management: Investigate the dependencies between components and how they interact.
Performance Analysis
- Load Balancing Techniques: Assess how the system distributes workload across its components.
- Resource Utilization Monitoring: Measure the utilization of CPU, memory, and network resources by the components.
- Performance Metrics: Define key performance indicators to evaluate the overall performance and efficiency of the system.
Security Analysis
- Vulnerability Scanning: Identify potential security vulnerabilities in the system’s components and network configuration.
- Threat Modeling: Assess the system’s susceptibility to specific threats and develop mitigation strategies.
- Authentication and Authorization Mechanisms: Analyze the methods used to authenticate users and authorize their access to resources.
Data Flow Analysis
- Data Source Identification: Determine the origins of data flowing through the distributed system.
- Data Transformation: Analyze how data is processed and transformed within the system’s components.
- Data Integrity Verification: Ensure that the integrity of data is maintained during its flow through the system.
Conclusion
Reverse engineering distributed systems is a valuable practice that empowers organizations with a comprehensive understanding of their complex software architectures. By leveraging the knowledge gained through this process, organizations can proactively manage their systems, ensuring their reliability, security, and performance. This in-depth guide has provided a thorough overview of the key concepts and subtopics involved in reverse engineering distributed systems, offering organizations a roadmap for successful implementation.
Keywords
- Reverse Engineering
- Distributed Systems
- System Architecture
- Performance Analysis
- Security Analysis
