Reverse Engineering for Digital Systems

Executive Summary
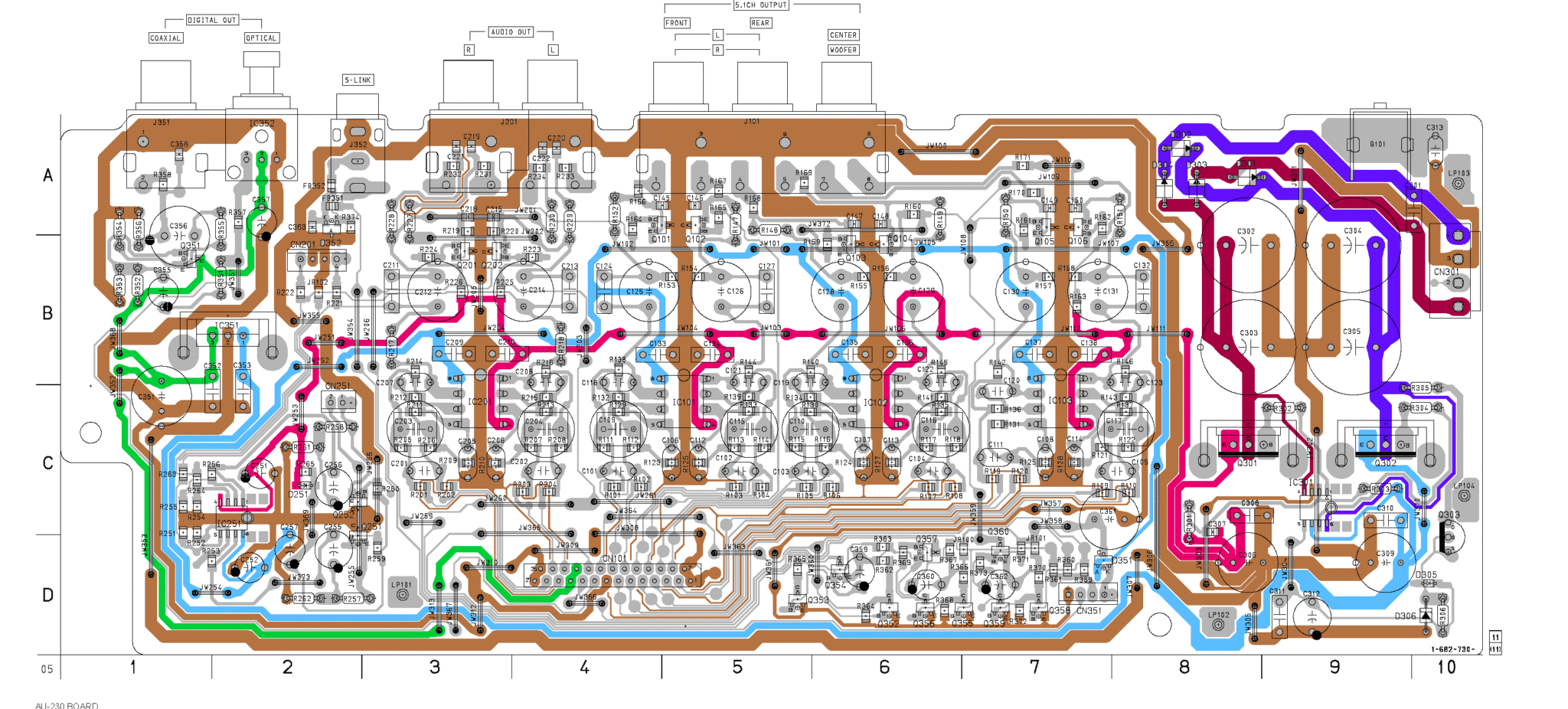
Reverse engineering is the process of analyzing a system to create a representation of its components and their relationships. This representation can be used to understand the system’s functionality, design, and implementation. Reverse engineering is used in a variety of applications, including:
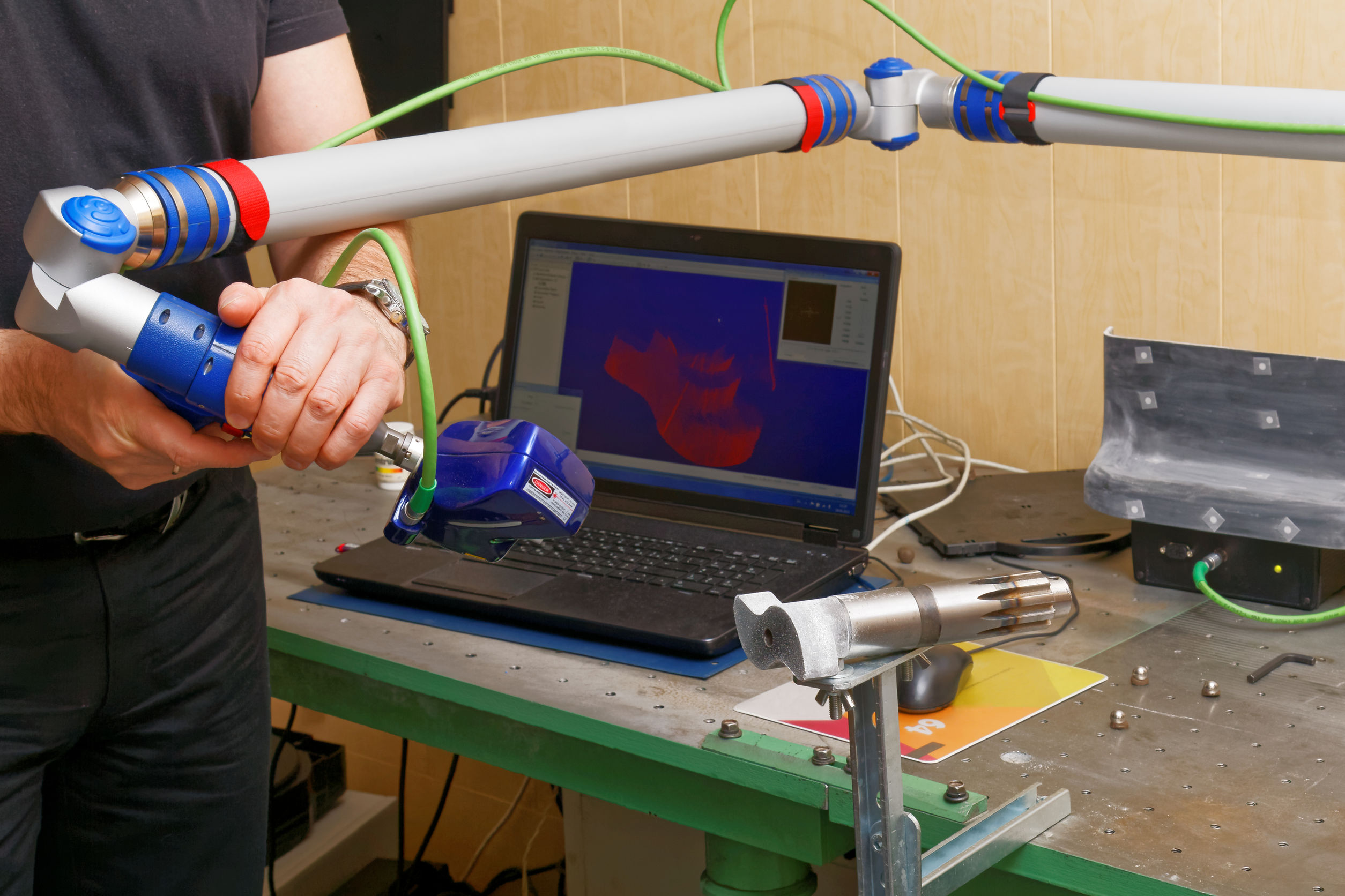
- Product development: Reverse engineering can be used to create a product that is similar to an existing product, but with different features or functionality.
- Maintenance and repair: Reverse engineering can be used to identify and fix problems with a system.
- Security analysis: Reverse engineering can be used to identify vulnerabilities in a system and develop security measures to protect against them.
Introduction
Reverse engineering is a complex process that requires a variety of skills and techniques. However, with the right tools and knowledge, it is possible to reverse engineer even the most complex systems.
FAQs
1. What are the benefits of reverse engineering?
Reverse engineering can provide a number of benefits, including:
- Reduced development time and cost: Reverse engineering can help to reduce the time and cost of developing a new product or system by providing a starting point for the design process.
- Improved product quality: Reverse engineering can help to improve the quality of a product or system by identifying and fixing problems in the design.
- Increased security: Reverse engineering can help to increase the security of a system by identifying vulnerabilities and developing security measures to protect against them.
2. What are the challenges of reverse engineering?
Reverse engineering can be a challenging process, particularly for complex systems. Some of the challenges of reverse engineering include:
- Lack of documentation: Many systems do not have complete or accurate documentation, which can make it difficult to understand the system’s functionality.
- Proprietary technology: Some systems use proprietary technology that is not publicly available, which can make it difficult to reverse engineer the system.
- Complex designs: Some systems are very complex, which can make it difficult to understand the system’s functionality and design.
3. What are the tools and techniques of reverse engineering?
A variety of tools and techniques can be used for reverse engineering, including:
- Software tools: There are a number of software tools that can be used to help with reverse engineering, such as disassemblers, decompilers, and source code recoverers.
- Hardware tools: Hardware tools, such as logic analyzers and oscilloscopes, can be used to analyze the behavior of a system at the hardware level.
- Documentation: Documentation, such as user manuals, schematics, and source code listings, can be used to provide information about the system’s functionality, design, and implementation.
Subtopics
1. Hardware Reverse Engineering
Hardware reverse engineering involves analyzing the physical components of a system to understand its functionality and design. This process includes:
- Physical inspection: The physical components of the system are visually inspected to identify the different components and their connections.
- Functional testing: The system is tested to determine its functionality.
- Logic analysis: Logic analyzers are used to analyze the signals on the system’s buses and other internal connections.
- Schematic capture: The logic analysis data is used to create a schematic diagram of the system’s hardware.
2. Software Reverse Engineering
Software reverse engineering involves analyzing the source code of a software system to understand its functionality and design. This process includes:
- Decompilation: The software is decompiled to convert it from machine code into a high-level programming language.
- Data flow analysis: The data flow of the software is analyzed to identify the different functions and modules and their relationships.
- Control flow analysis: The control flow of the software is analyzed to determine the order in which the different functions and modules are executed.
- Source code recovery: The decompiled and analyzed code is used to create a source code listing for the software.
3. Firmware Reverse Engineering
Firmware reverse engineering involves analyzing the firmware code of a system to understand its functionality and design. This process includes:
- Extraction: The firmware code is extracted from the system’s memory.
- Disassembly: The firmware code is disassembled to convert it from machine code into a high-level programming language.
- Analysis: The disassembled code is analyzed to identify the different functions and modules and their relationships.
- Reconstruction: The analyzed code is used to reconstruct the firmware code in a high-level programming language.
4. Protocol Reverse Engineering
Protocol reverse engineering involves analyzing the protocol used by a system to communicate with other systems or devices. This process includes:
- Capturing: The protocol data is captured using a protocol analyzer.
- Decoding: The captured data is decoded to identify the different fields and messages in the protocol.
- Analysis: The decoded data is analyzed to identify the different functions and messages and their relationships.
- Modeling: A model of the protocol is created to document its functionality and design.
5. System Reverse Engineering
System reverse engineering involves combining the results of hardware, software, firmware, and protocol reverse engineering to create a complete understanding of the system’s functionality and design. This process includes:
- Integration: The results of the different reverse engineering techniques are integrated to create a system model.
- Analysis: The system model is analyzed to identify the different components and their relationships and to understand the system’s overall functionality.
- Documentation: The system model is documented to provide a complete description of the system’s functionality and design.
Conclusion
Reverse engineering is a powerful tool that can be used to understand the functionality and design of complex systems. With the right tools and knowledge, it is possible to reverse engineer even the most complex systems.
Keyword Tags
- Reverse engineering
- Digital systems
- Hardware reverse engineering
- Software reverse engineering
- Firmware reverse engineering
- Protocol reverse engineering
- System reverse engineering
