Monitoring and Analyzing System Logs with Syslog
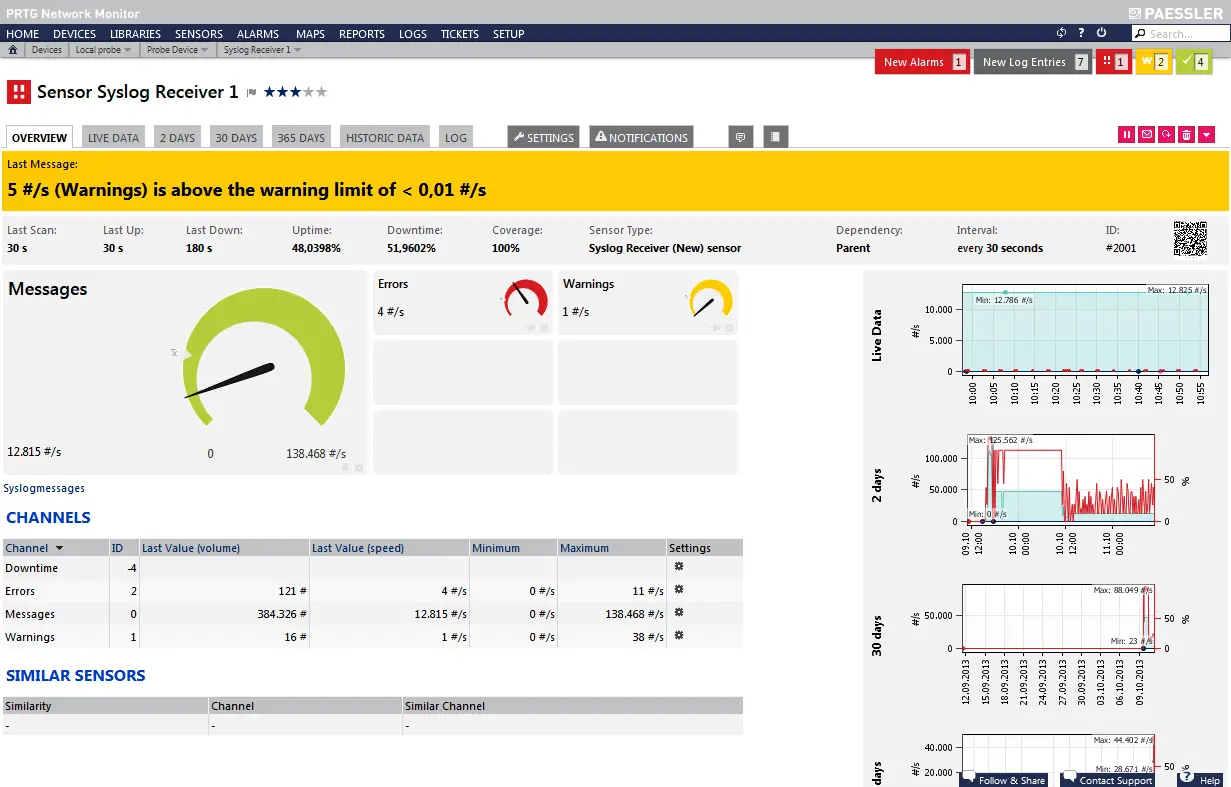
Syslog is a protocol that allows organizations to collect and store system logs from various devices, applications, and systems in a central location. It enables organizations to monitor and analyze these logs to detect anomalies, troubleshoot issues, and ensure compliance.
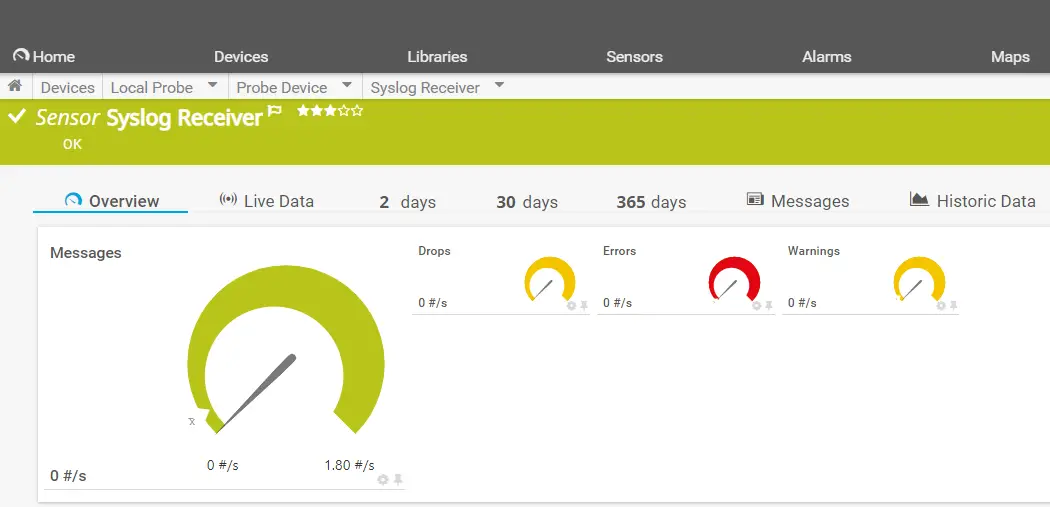
How Syslog Works
Syslog operates on a client-server model. Syslog clients, such as network devices, servers, and applications, generate and send log messages to a central Syslog server. The Syslog server is responsible for receiving, filtering, and storing these log messages.
Log messages in Syslog include various fields, such as the following:
- Timestamp: Time when the log message occurred
- Host: Device or system that generated the log message
- Facility: Service or application that produced the log message
- Severity: Level of importance of the log message
- Message: Textual description of the event or error
Benefits of Syslog
Centralized logging offers several benefits:
- Early detection of issues: Proactively identifies potential problems before they become major incidents.
- Troubleshooting: Aids in diagnosing and resolving system issues by providing detailed information about errors and events.
- Compliance monitoring: Helps organizations demonstrate compliance with regulatory and security standards by auditing and analyzing log data.
- Forensic analysis: Preserves log data for security incident investigations and root cause analysis.
- Capacity planning: Assists in understanding system usage patterns and identifying potential performance bottlenecks.
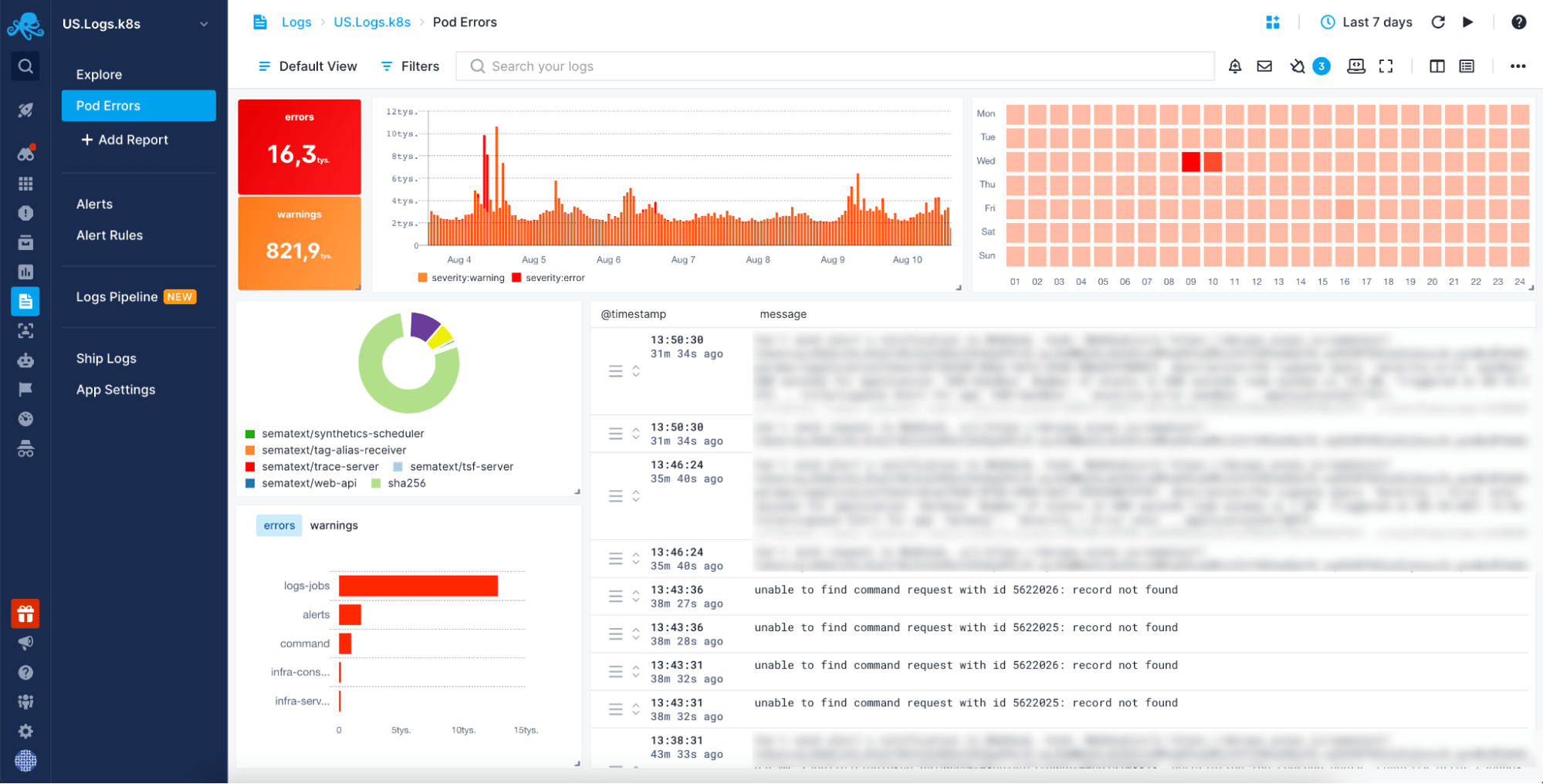
Log Analysis
Once logs are collected and centralized, organizations can leverage log analysis tools to gain insights from the data. These tools provide features like:
- Filtering: Narrow down log messages based on specific criteria, such as severity, facility, or host.
- Searching: Quickly locate specific events or errors within vast log volumes.
- Aggregation: Group similar log messages to identify patterns and trends.
- Visualization: Present log data in easy-to-understand dashboards and reports.
Conclusion
Monitoring and analyzing system logs with Syslog empowers organizations to gain valuable insights into their systems’ operations and security posture. By collecting and centralizing logs, organizations can proactively detect issues, ensure compliance, and optimize their IT infrastructure. Regular log analysis helps organizations maintain system stability, improve performance, and protect against potential threats and vulnerabilities.## Monitoring and Analyzing System Logs with Syslog
Executive Summary
System logs provide crucial insights into the health and performance of IT systems. Syslog is a versatile tool that enables efficient monitoring and analysis of these logs. This comprehensive guide explores the key components of Syslog, its benefits, implementation considerations, and best practices. By leveraging Syslog, organizations can proactively identify and resolve issues, enhance system security, and optimize IT operations.
Introduction
System logs are repositories of events, errors, and informational messages generated by various components within an IT infrastructure. These logs offer invaluable visibility into system behavior and can help administrators troubleshoot issues, track user activities, detect security breaches, and monitor compliance. Syslog, short for System Logging Protocol, is a widely adopted standard protocol for collecting, storing, and analyzing system logs. It provides a centralized mechanism for aggregating logs from multiple devices and applications, enabling comprehensive monitoring and analysis.
Key Components of Syslog
- Syslog Server: A central repository that receives and stores system logs from clients.
- Syslog Client: A program or agent that sends logs to the syslog server.
- Syslog Message: A structured message containing a timestamp, hostname, facility, severity, and log message.
- Facility: A predefined category that indicates the source of the log message, such as kernel, user, or mail.
- Severity: A level that indicates the importance of the log message, such as debug, info, warning, error, or critical.
Benefits of Syslog
- Centralized Logging: Aggregates logs from multiple sources into a single location.
- Standard Format: Facilitates easy parsing and analysis of logs from diverse systems.
- Scalability: Supports large-scale deployments with high log volumes.
- Enhanced Visibility: Provides comprehensive insights into system performance and behavior.
- Improved Troubleshooting: Simplifies the process of identifying and resolving issues.
- Security Monitoring: Enables detection of security events and assists in forensic investigations.
- Compliance Auditing: Provides a central repository for logs required for compliance reporting.
Implementation Considerations
- Log Format: Choose a log format that is compatible with the syslog server and analysis tools.
- Severity Levels: Configure severity levels to prioritize logs based on their importance.
- Network Infrastructure: Ensure reliable network connectivity between syslog clients and the server.
- Log Storage: Determine an appropriate log retention period based on legal and compliance requirements.
- Security: Implement security measures to protect log data from unauthorized access.
Best Practices for Syslog Management
- Regular Monitoring: Regularly review syslog messages to identify trends and anomalies.
- Log Analysis: Use log analysis tools to extract meaningful insights and create custom reports.
- Alerting and Notification: Set up alerts and notifications for critical log messages.
- Log Correlation: Correlate logs from different sources to identify patterns and relationships.
- Data Retention: Retain logs for an appropriate period based on organizational policies and compliance requirements.
- Data Archiving: Archive historical logs for long-term analysis and forensic investigations.
Conclusion
Syslog is an essential tool for effective IT monitoring and analysis. By centralizing logs, standardizing their format, and enabling scalable log management, Syslog simplifies the task of troubleshooting, security monitoring, and compliance auditing. Organizations that implement Syslog best practices can gain invaluable insights into their IT infrastructure, improve operational efficiency, and enhance system security.
Keyword Phrase Tags
- Syslog
- System Logging Protocol
- Log Monitoring
- Log Analysis
- IT Security

This article is quite informative. I was unaware of the existence of syslog and its importance in monitoring system logs. I will definitely look into it further.
This article is useless. It doesn’t provide any specific information on how to configure syslog or use it to analyze system logs.
syslog is an antiquated protocol that has been replaced by more modern and efficient logging mechanisms. This article is not relevant to modern system administration.
Ironic that an article about monitoring system logs would have so many errors in its own log.
Wow, this article is so helpful. I can’t wait to use syslog to monitor my system logs and fix all the problems that I didn’t know I had.
syslog? More like snorelog! Am I right?