SSH Key Authentication: A Comprehensive Guide to Enhanced Linux Security
An Overview of SSH Key Authentication
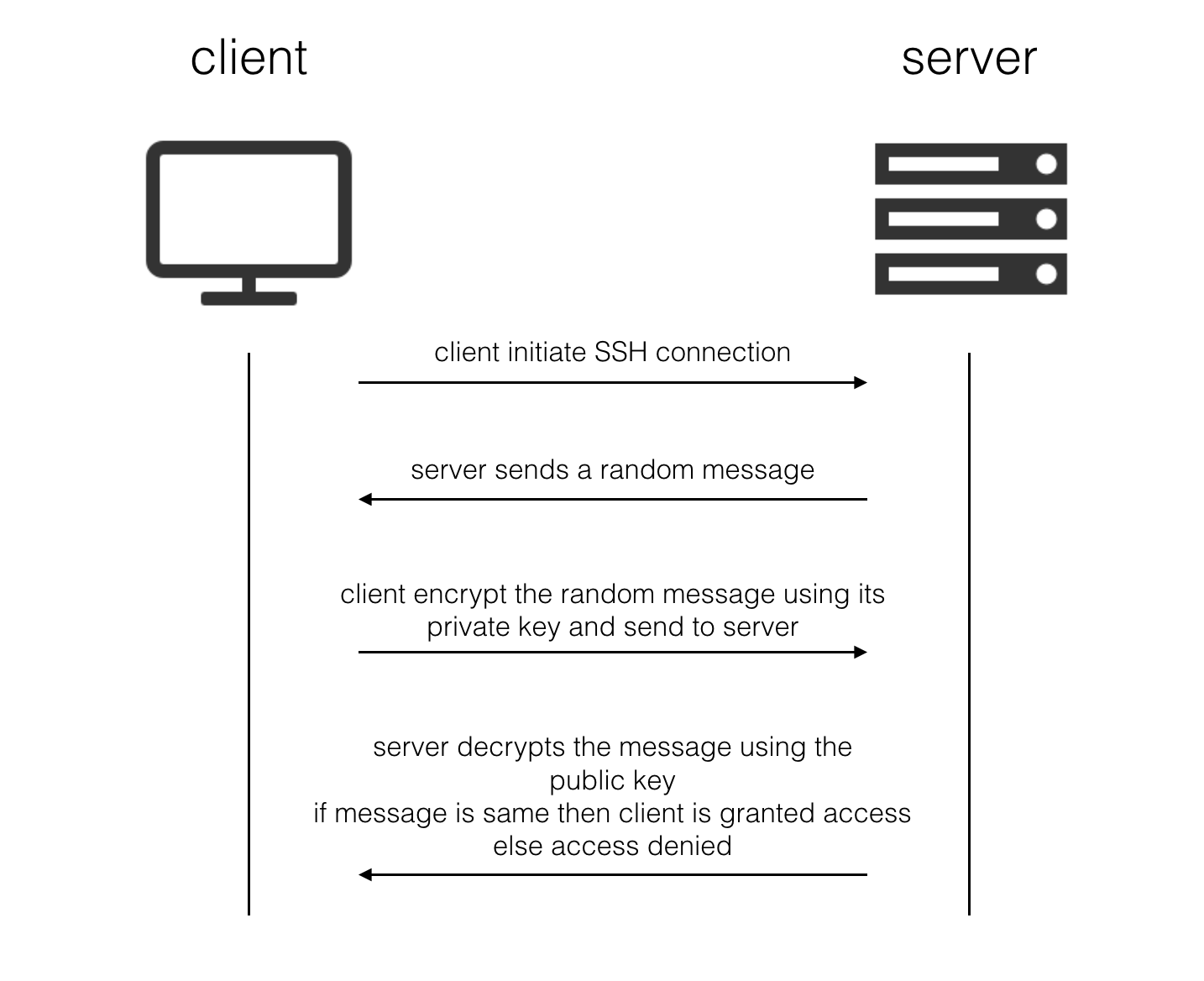
SSH (Secure Shell) key authentication is a method of securing remote logins, providing an alternative to traditional password-based authentication. Instead of relying on a password, key authentication utilizes a public/private key pair, where the private key is carefully guarded on the client device, while the public key is stored on the server.
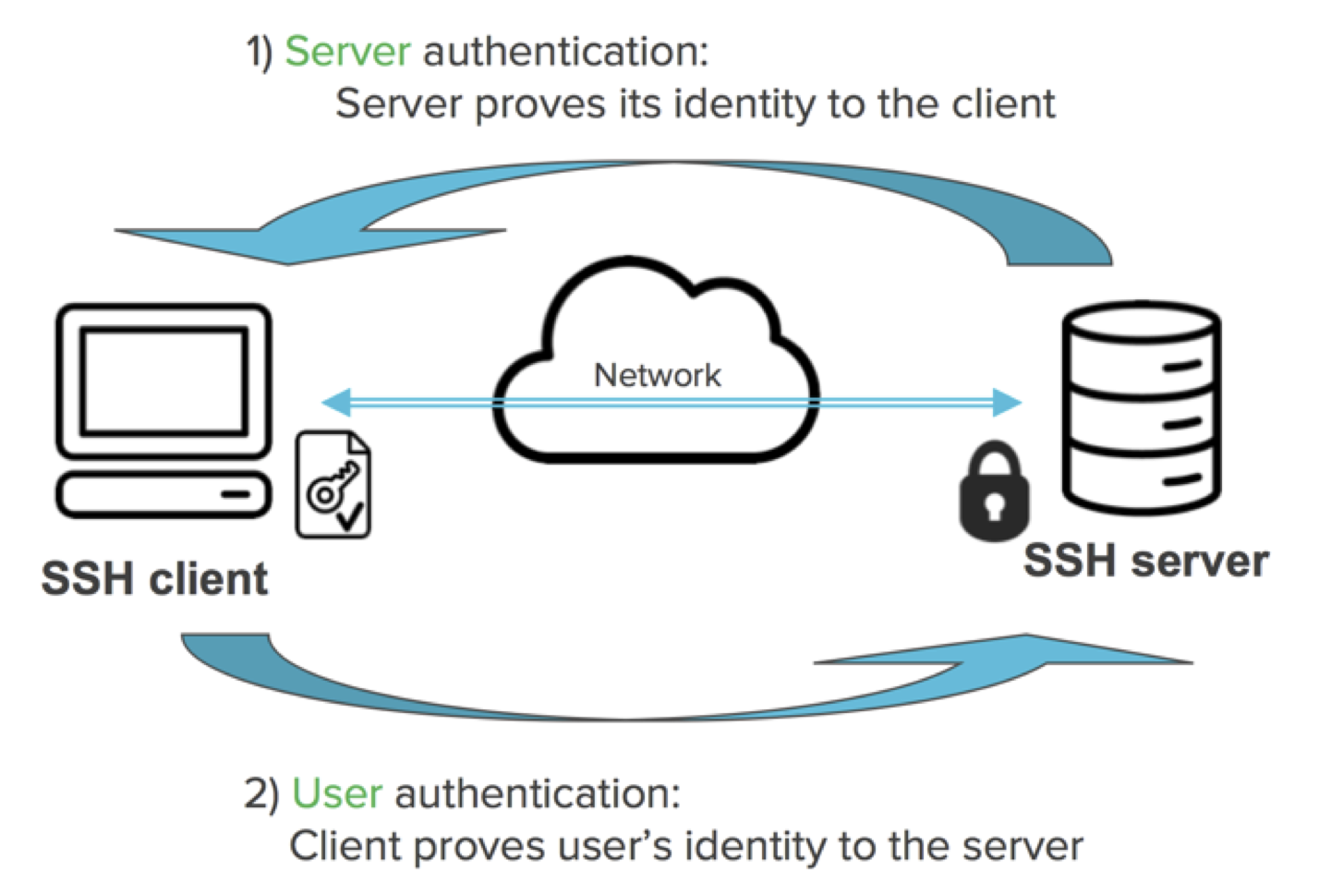
How SSH Key Authentication Works
-
Key Generation: The client device generates a public/private key pair using the ssh-keygen command.
-
Public Key Distribution: The client’s public key is distributed to the remote server using the ssh-copy-id command or manually by copying the key to the authorized_keys file on the server.
-
SSH Login Attempt: When the client connects to the server using SSH, the server verifies if the client possesses the corresponding private key.
-
Authentication Success: If the private key matches the public key stored on the server, the server grants access to the client.
Benefits of SSH Key Authentication
- Strong Security: Public/private key pairs offer significantly enhanced security compared to passwords, making it harder for malicious actors to access systems.
- Eliminates Password Sniffing: Key authentication does not transmit passwords over the network, eliminating the risk of password theft.
- Automated Login: With key authentication, users no longer need to manually enter passwords, reducing potential for errors and simplifying the login process.
- Centralized Key Management: Public keys can be easily stored on a central server, simplifying key management and reducing the risk of losing private keys.
Implementing SSH Key Authentication
- Generate Key Pair on Client:
ssh-keygen -t <type>- Copy Public Key to Server:
ssh-copy-id <username>@<server>- Configure Server:
Modify /etc/ssh/sshd_config to specify the following directives:
PasswordAuthentication noPubkeyAuthentication yes
- Restart SSH Service:
systemctl restart sshdBest Practices for SSH Key Authentication
- Use Strong Passphrase: Consider using a strong passphrase to protect your private key.
- Limit Authorized Keys: Restrict the number of authorized keys to minimize the risk of compromise.
- Use Separate Keys for Different Accounts: Generate a new key pair for each user account to limit the impact of a compromised key.
- Regularly Rotate Keys: Replace your keys periodically to mitigate the potential security risks.
Conclusion
Implementing SSH key authentication provides a substantial boost to Linux security. By replacing password-based authentication with public/private key pairs, IT administrators can significantly reduce the likelihood of unauthorized access while streamlining the login process. The user-friendly implementation and robust security measures make key authentication an essential practice for any organization prioritising data protection.

SSH key authentication is a great way to improve the security of your Linux server. By using SSH keys, you can avoid the risk of password theft and brute-force attacks. In this article, we will discuss the basics of SSH key authentication, and we will provide step-by-step instructions on how to set it up on your server. nice!
SSH key authentication is not as secure as you think. In fact, there are a number of ways to attack SSH keys, and some of these attacks can be quite effective. In this article, we will discuss some of the most common attacks on SSH keys, and we will provide some tips on how to protect yourself from these attacks.
This article provides a comprehensive overview of SSH key authentication. The step-by-step instructions are easy to follow, and the article is well-written and informative.
I disagree with the author’s assessment of the security of SSH key authentication. I believe that SSH key authentication is a very secure way to protect your server. In fact, I have never seen a successful attack on SSH key authentication.
Of course SSH key authentication is secure. It’s like locking your door and then hiding the key under the mat.
SSH key authentication is like a magic spell that protects your server from evil hackers. Just kidding!
I have a better idea! Let’s just use a really long and complicated password. That way, no one will be able to guess it.
SSH key authentication is a well-known and widely used security mechanism. It is based on public key cryptography, which is considered to be very secure. However, it is important to note that no security mechanism is perfect, and there are always potential vulnerabilities that could be exploited by attackers.
I’m not convinced that SSH key authentication is as secure as people say it is. I’ve heard of several cases where attackers have been able to compromise SSH keys and gain access to servers.
I’m new to SSH key authentication, and I’m wondering if it’s really worth the effort to set up. Is it really that much more secure than using a password?
SSH key authentication is a must-have for any server administrator who is serious about security. It’s easy to set up and it can significantly improve the security of your server.
I’m not sure I trust SSH key authentication. What if my private key is stolen? Wouldn’t that give an attacker access to all of my servers?
SSH key authentication is a great way to improve the security of your Linux server. It’s easy to set up and it can help to protect your server from a variety of attacks.
I’ve been doing some research on SSH key authentication, and I’ve found that it’s not as secure as I thought it was. There are a number of ways to attack SSH keys, and some of these attacks can be quite effective.
SSH key authentication is a very secure way to protect your Linux server. However, it’s important to remember that no security mechanism is perfect, and there are always potential vulnerabilities that could be exploited by attackers.