Linux Security: Configuring SELinux and AppArmor

SELinux (Security-Enhanced Linux) and AppArmor are two Linux kernel security modules that enhance the security of the operating system by implementing mandatory access control (MAC). MAC is a security policy that specifies which users can access which resources, and under what conditions.

SELinux and AppArmor are both very powerful security tools, but they can also be complex to configure. In this article, we will provide a detailed guide on nasıl to configure SELinux and AppArmor.
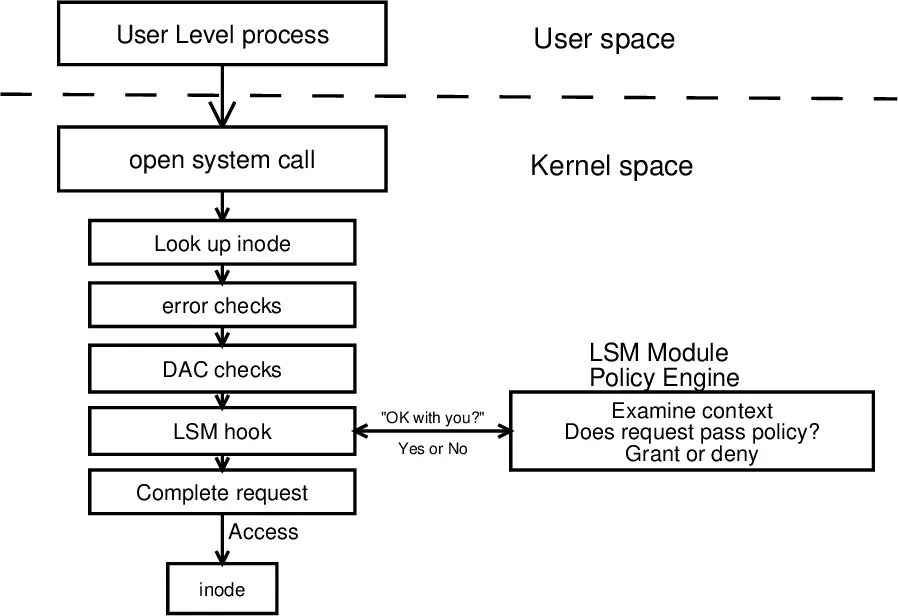
SELinux
SELinux is a mature and widely used security module that has been available in the Linux kernel since version 2.6. SELinux enforces access control based on a set of security policies. These policies are defined in the form of SELinux policy modules.
The default SELinux policy module is called targeted. The targeted policy module provides a good level of security without being too restrictive. However, you can also create your own custom policy modules to meet the specific security requirements of your system.
To configure SELinux, you can use the following commands:
- getenforce – prints the current SELinux enforcement mode
- setenforce – changes the SELinux enforcement mode
- sestatus – displays SELinux status information
- semanage – manage SELinux policies
For more detailed information on how to configure SELinux, please refer to the SELinux documentation.
AppArmor
AppArmor is a newer security module than SELinux, but it is also very powerful. AppArmor enforces access control based on a set of profiles. These profiles are defined in the form of AppArmor profiles.
The default AppArmor profile is called unconfined. The unconfined profile allows all applications to run with full privileges. However, you can also create your own custom profiles to restrict the privileges of specific applications.
To configure AppArmor, you can use the following commands:
- apparmor_status – displays AppArmor status information
- aa-enforce – enables AppArmor enforcement
- aa-disable – disables AppArmor enforcement
- aa-complain – enables AppArmor complain mode
- aa-log – logs AppArmor messages
For more detailed information on how to configure AppArmor, please refer to the AppArmor documentation.
Conclusion
SELinux and AppArmor are both powerful security tools that can enhance the security of your Linux system. However, they can also be complex to configure. In this article, we have provided a detailed guide on how to configure SELinux and AppArmor.Linux Security: Configuring SELinux and AppArmor
Executive Summary
Implementing SELinux and AppArmor security modules enhances the security posture of Linux systems, protecting them from unauthorized access, malware attacks, and other security threats. Through mandatory access control (MAC) and kernel-level restrictions, SELinux and AppArmor provide fine-grained control over system resources and program execution, restricting processes based on security policies.
Introduction
Linux systems are widely used in enterprise and critical infrastructure due to their stability, performance, and open-source nature. However, securing Linux systems is crucial to mitigate security risks. SELinux and AppArmor are two robust security modules that complement each other, offering advanced protection mechanisms for Linux environments.
Subtopics
1. SELinux (Security-Enhanced Linux)
SELinux is a MAC framework that enforces role-based access control (RBAC) policies. It provides a fine-grained approach to managing file system permissions, file access, and system calls.
- Mandatory Access Control (MAC): SELinux enforces security policies that are defined in the system’s security policy file.
- Role-Based Access Control (RBAC): SELinux assigns roles and permissions to users and processes based on specific policies.
- Type Enforcement: SELinux ensures that files and directories are accessed only by authorized programs or users.
- Audit and Logging: SELinux provides extensive audit and logging capabilities, allowing administrators to monitor system activity and identify potential security breaches.
2. AppArmor
AppArmor is a kernel-level security module that limits applications’ access to system resources. It uses a “least privilege” approach, granting programs only the minimum access necessary to perform their designated functions.
- Kernel-Level Enforcement: AppArmor operates at the kernel level, providing a stronger level of security than user-space security tools.
- Confined Environments: AppArmor isolates applications by confining them to specific resource profiles, limiting their access to files, directories, and other system components.
- Fine-Grained Control: AppArmor allows administrators to define detailed security policies that restrict specific actions, such as network access, file or process creation, and device usage.
- Centralized Management: AppArmor provides centralized management capabilities, allowing administrators to configure and monitor security policies for multiple systems from a single interface.
3. Comparison of SELinux and AppArmor
| Feature | SELinux | AppArmor |
|---|---|---|
| Security Model | Mandatory Access Control (MAC) | Least Privilege |
| Level of Enforcement | Enforced at the kernel level | Enforced at the kernel level |
| File System Protection | Type enforcement, file access control | File and directory access control |
| Application Confinement | Not a core feature | Core feature |
| Audit and Logging | Extensive audit and logging capabilities | Limited audit and logging capabilities |
4. Configuring SELinux
- Enable SELinux: Enable SELinux in the kernel configuration or through command-line utilities.
- Define Security Policy: Create and modify security policy files that define roles, permissions, and access rules.
- Audit and Monitor: Enable auditing and logging to track system activity and identify potential security issues.
- Troubleshoot: Use troubleshooting tools and techniques to identify and resolve SELinux-related issues.
5. Configuring AppArmor
- Enable AppArmor: Enable AppArmor in the kernel configuration or through command-line utilities.
- Define Profiles: Create and modify AppArmor profiles that define application resource usage restrictions.
- Test and Monitor: Test profiles and monitor system activity to ensure that applications are confined as intended.
- Troubleshoot: Use troubleshooting tools and techniques to identify and resolve AppArmor-related issues.
Conclusion
SELinux and AppArmor are powerful security modules that significantly enhance the security posture of Linux systems. By providing fine-grained control over system resources and program execution, these modules mitigate security threats, reduce unauthorized access, and protect sensitive information. Implementing a combination of SELinux and AppArmor provides a comprehensive security solution for enterprise and critical infrastructure environments.
Keyword Phrase Tags
- Linux Security
- SELinux
- AppArmor
- Mandatory Access Control (MAC)
- Kernel-Level Security

This is a great article! I’ve been looking for a way to improve the security of my Linux system, and this article has given me some great tips. I’m going to try out these configurations and see how they work for me.
I’m not sure if these configurations are really necessary. I’ve been running Linux for years without them, and I’ve never had any security problems.
These configurations are definitely a good idea if you’re concerned about security. They can help to protect your system from a variety of attacks.
I disagree. I think these configurations are overkill. They’re more likely to cause problems than they are to prevent them.
I’m sure these configurations are very effective. But I’m not going to use them because I don’t want to make my system too secure.
Oh, wow! These configurations are amazing! I can’t believe I’ve been running Linux without them for so long. I’m going to install them right now and see how much better my system becomes.
I’m not sure what these configurations do, but they sound like they could be fun. I’m going to try them out and see if I can make my system go faster.
These configurations are a good starting point, but you may need to customize them to fit your specific needs.
I’m not sure if I’m ready to try these configurations yet. I’m afraid I might mess up my system.
I’m so excited to try these configurations! I’ve been wanting to improve the security of my system for a while now.
I’m interested in learning more about these configurations. Can anyone recommend any good resources?