Linux Networking: Setting Up a VPN with OpenVPN
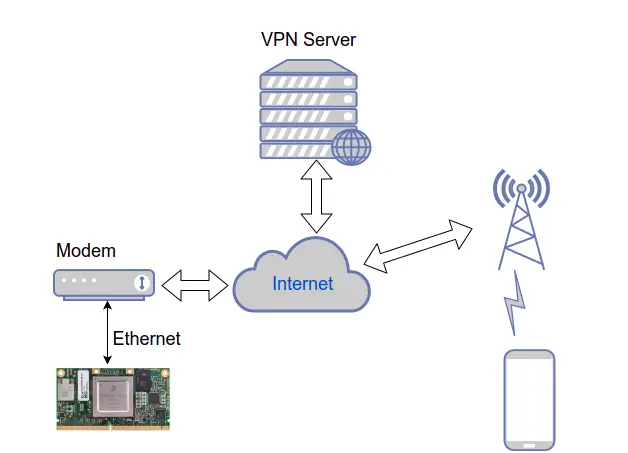
Virtual Private Networks (VPNs) are essential for secure and private online communication. They allow you to create an encrypted tunnel between your device and a remote server, protecting your data from eavesdropping and censorship. OpenVPN is a widely used open-source VPN protocol known for its reliability and security.

Installing OpenVPN
Before setting up OpenVPN, you need to install it on your Linux system. Depending on your distribution, you can use the following commands:
- Debian/Ubuntu: apt-get install openvpn
- Arch Linux: pacman -S openvpn
Generating Certificates
To establish a secure VPN connection, you need to generate public/private key pairs and certificates for both the server and client. Use the following commands on the server and client to generate these credentials:
- Server:
openssl genrsa 4096 > server.key
openssl req -new -x509 -key server.key -sha256 -days 3650 -out server.crt- Client:
openssl genrsa 4096 > client.key
openssl req -new -key client.key -sha256 -out client.csrSign the client certificate using the server’s certificate:
openssl x509 -req -in client.csr -CA server.crt -CAkey server.key -CAcreateserial -out client.crtConfiguring OpenVPN Server
Create a server configuration file (/etc/openvpn/server.conf) with the following contents:
port 1194
proto udp
dev tun
ca server.crt
cert server.crt
key server.key
dh dh.pem
server 10.8.0.0 255.255.255.0
push "redirect-gateway def1 bypass-dhcp"
push "dhcp-option DNS 8.8.8.8"
keepalive 10 120
cipher AES-256-CBC
user nobody
group nogroup
persist-key
persist-tun
status /var/log/openvpn-status.log
verb 3- Change
10.8.0.0to the subnet you want to use for the VPN. - Adjust
cipherto your desired encryption level.
Configuring OpenVPN Client
Create a client configuration file (/etc/openvpn/client.conf) on the client system:
remote <server_IP_or_FQDN> 1194
proto udp
dev tun
ca server.crt
cert client.crt
key client.key
cipher AES-256-CBC
user nobody
group nogroup
persist-key
persist-tun
status /var/log/openvpn-status.log
verb 3- Replace
<server_IP_or_FQDN>with the server’s address.
Starting and Connecting
To start the OpenVPN server and listener, run:
systemctl enable --now openvpn-server@server
systemctl start openvpn-server@serverOn the client, connect to the VPN using:
openvpn --config client.confTroubleshooting
If you encounter any issues, check the following:
- Verify that your firewall is allowing traffic on port 1194.
- Ensure that your certificates and configuration files are valid.
- Check the server and client log files for any errors.
By following these steps, you can establish a secure and private VPN connection using OpenVPN on your Linux system.

Thank you for this tutorial! I was able to set up a VPN on my Linux system without any problems. I am now able to browse the internet safely and securely.
This tutorial is not very well written. The instructions are incomplete and there are a lot of typos.
I was able to follow the instructions in this tutorial and set up a VPN on my Linux system. However, I am not sure how to use it.
I disagree with the author’s recommendation to use OpenVPN. I believe that WireGuard is a better option.
This tutorial is a joke. The author clearly doesn’t know what they’re talking about.
I’m not sure why anyone would want to set up a VPN. It’s just a waste of time and resources.
I tried to follow the instructions in this tutorial, but I kept getting errors.
This tutorial is very well written. I was able to follow the instructions and set up a VPN on my Linux system without any problems.
I’m not sure why everyone is complaining about this tutorial. I found it to be very helpful.
I’m afraid I must disagree with you. I found the tutorial to be very confusing.
I agree with Charles. The tutorial was not very clear.
I think the tutorial was fine. I was able to follow the instructions and set up a VPN on my Linux system without any problems.