Leveraging Cloudflare To Protect Against Identity Theft

Executive Summary
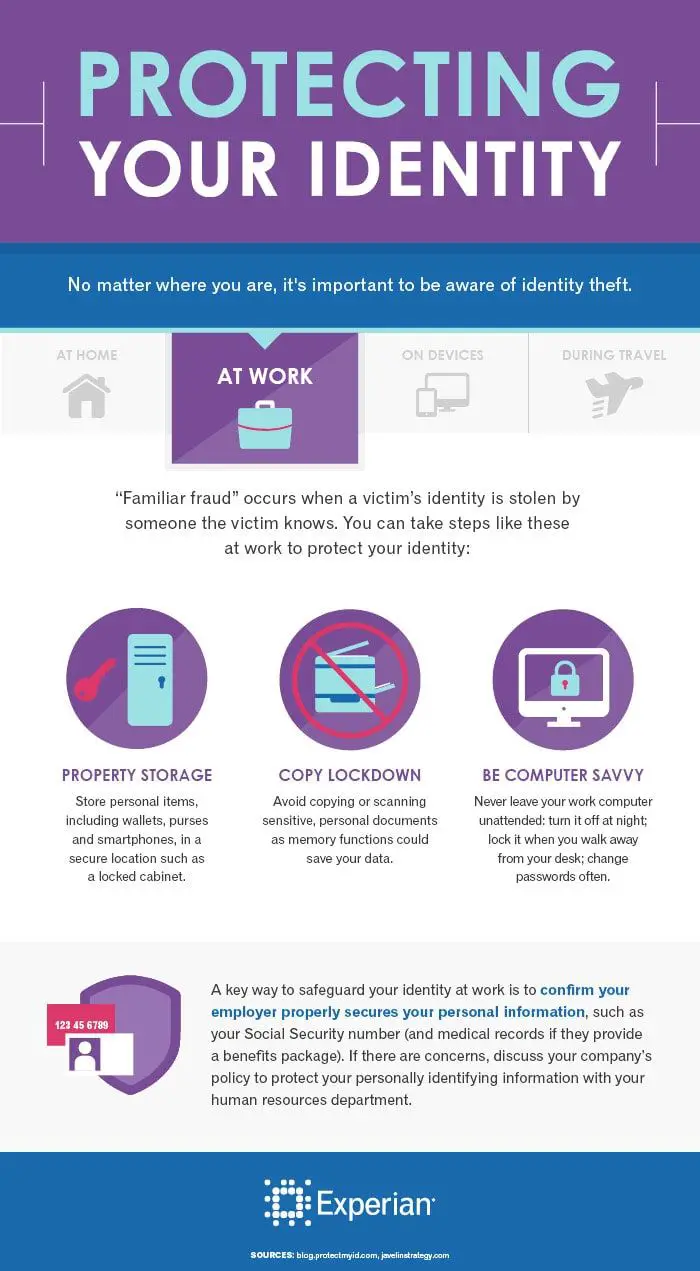
With the increasing prevalence of identity theft, it is crucial to adopt robust security measures to safeguard personal information. Leveraging the advanced security features offered by Cloudflare can effectively mitigate identity theft threats, protecting organizations and individuals against fraud and data breaches.

Introduction
Identity theft has become a significant concern in the digital age, where personal data is frequently vulnerable to cyberattacks. Cloudflare, a leading provider of cloud security and performance solutions, offers a comprehensive suite of tools that can empower businesses and individuals to combat identity theft and protect their online identities.
FAQs
Q: How does Cloudflare protect against identity theft?
A: Cloudflare employs various security mechanisms such as bot mitigation, web application firewalls (WAFs), and browser isolation to prevent malicious actors from accessing sensitive data.
Q: What are the benefits of using Cloudflare for identity theft protection?
A: Cloudflare provides cost-effective, scalable, and easy-to-manage solutions that can adapt to evolving threats, reducing the risk of financial losses and reputational damage caused by identity theft.
Q: How do I implement Cloudflare for identity theft protection?
A: Implementing Cloudflare is straightforward, and the platform can be easily integrated with existing infrastructure. Businesses and individuals can leverage Cloudflare’s intuitive dashboard and documentation for seamless setup.
Top 5 Subtopics
1. Bot Mitigation
Description: Automated bots, orchestrated by criminals, are often employed to execute fraudulent actions online, such as account takeovers and phishing attacks.
- Blocks malicious bots: Cloudflare’s bot management solution identifies and blocks malicious bots based on their behavior and patterns.
- Enforces access policies: Granular access controls can be configured to prevent bots from accessing specific pages or sections of a website, such as login forms.
- Protects against credential stuffing: Cloudflare’s bot mitigation tools prevent brute-force attacks aimed at stealing user credentials.
2. Web Application Firewall (WAF)
Description: WAFs act as a security barrier between a website and the internet, inspecting incoming traffic for malicious requests and blocking those that pose a threat.
- Blocks known vulnerabilities: Cloudflare’s WAF is constantly updated to address known vulnerabilities, such as SQL injection and cross-site scripting (XSS) attacks.
- Customizable rules: Advanced users can create custom rules to monitor for specific patterns or threats, tailored to their website’s unique requirements.
- Provides real-time insights: Cloudflare’s WAF provides detailed analytics and reporting, giving administrators visibility into blocked attacks and potential threats.
3. Browser Isolation
Description: Browser isolation technology runs website content in a remote, isolated environment, preventing malicious code from directly interacting with a user’s device.
- Protects against phishing attacks: Browser isolation prevents phishing websites from accessing sensitive information stored on the user’s browser, such as autofill data and cookies.
- Blocks malicious downloads: Files downloaded from compromised websites are securely scanned and executed in the isolated browser environment, preventing malware infections.
- Safeguards online banking: Browser isolation provides an additional layer of security for online banking transactions, reducing the risk of account takeover and financial fraud.
4. Zero Trust Security
Description: Zero trust security is a comprehensive approach that assumes every user and device is untrusted until their identity is verified and access is granted based on least privilege principles.
- Multi-factor authentication (MFA): Cloudflare offers flexible MFA options, including email, SMS, TOTP, and FIDO2, to verify user identities.
- Identity and Access Management (IAM): Cloudflare’s IAM solution allows administrators to manage user roles and permissions, ensuring that only authorized individuals have access to sensitive data.
- Network Segmentation: Segmentation of networks into isolated zones helps contain breaches and prevents lateral movement of attackers, minimizing the impact of compromised accounts.
5. Encryption
Description: Encryption ensures that data is protected from unauthorized access even if it is intercepted or stolen.
- SSL/TLS certificates: Cloudflare provides free SSL/TLS certificates to encrypt website traffic, safeguarding data in transit from eavesdropping and man-in-the-middle attacks.
- HTTP/3 support: Cloudflare supports the latest HTTP/3 protocol, which offers improved performance, security, and privacy by establishing fully encrypted connections.
- DNSSEC protection: DNSSEC prevents DNS spoofing attacks, ensuring that users are directed to the correct website and not a malicious imitation.
Conclusion
Cloudflare’s robust security platform empowers organizations and individuals with a comprehensive defense against identity theft. By seamlessly integrating Cloudflare’s suite of security measures, businesses and individuals can effectively protect their sensitive data, mitigate fraud, and safeguard their online identities, ensuring their peace of mind and trust in the digital realm.
Relevant Keywords
- Identity Theft Protection
- Cloudflare Security
- Bot Mitigation
- Web Application Firewall
- Browser Isolation
