Enhancing Content Security with CDN Edge Authentication
Introduction
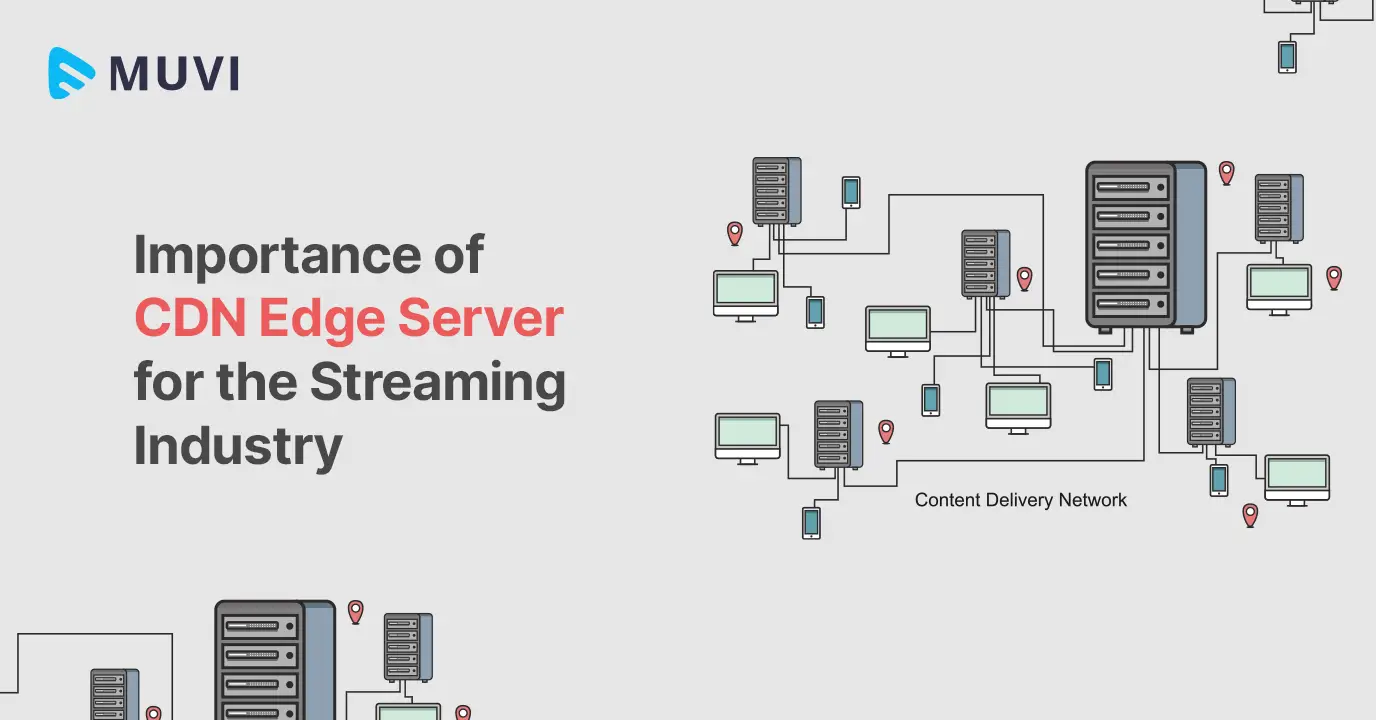
Content Delivery Networks (CDNs) play a crucial role in delivering content to end users with improved speed, reliability, and security. However, traditional CDN delivery methods can be vulnerable to content tampering and unauthorized access. CDN Edge Authentication addresses these concerns by offering a robust mechanism for content validation and protection at the network edge.

CDN Edge Authentication
CDN Edge Authentication is a security protocol that utilizes cryptographic techniques to validate the integrity and authenticity of content delivered from a CDN. It consists of two key components:
- Origin Authentication: Ensures that the content delivered by the CDN is authorized by the content owner or origin server.
- Edge Validation: Allows CDN edge servers to verify the authenticity of content before delivering it to end users.
Benefits of CDN Edge Authentication
- Content Integrity: Prevents unauthorized modification or manipulation of content by ensuring that it has not been altered since it was signed by the origin.
- Data Confidentiality: Protects sensitive data from unauthorized access by encrypting content before delivery to CDN edge servers.
- Reduced Risk of Man-in-the-Middle Attacks: Mitigates the risk of malicious actors intercepting and altering content during delivery.
- Compliance and Regulatory Adherence: Meets industry regulations and standards that require content protection and integrity.
How CDN Edge Authentication Works
CDN Edge Authentication employs a combination of cryptographic hashing and digital signatures:
- Origin Authentication:
- The origin server calculates a cryptographic hash of the content to be delivered.
- It signs the hash using a private key to create a digital signature.
- Both the hash and the digital signature are included in the content headers.
- Edge Validation:
- CDN edge servers receive the content with the headers containing the hash and digital signature.
- They calculate a new hash of the received content.
- They verify the digital signature using the public key associated with the origin server.
- If the calculated hash matches the included hash and the digital signature is valid, the content is considered authentic and can be delivered to end users.
Implementation Considerations
- Certificate Management: Requires careful management of public and private keys for digital signature generation and verification.
- Performance Optimization: Optimizing the authentication process to minimize latency and impact on content delivery performance.
- Compatibility: Ensuring compatibility with different CDN providers and edge server configurations.
- Cost Considerations: CDN Edge Authentication may introduce additional costs associated with key management, encryption, and signature verification.
Conclusion
CDN Edge Authentication is a powerful security enhancement that significantly improves content security by preventing unauthorized content tampering, ensuring data confidentiality, and reducing the risk of malicious attacks. By implementing this protocol, organizations can protect their valuable content, enhance user trust, and meet regulatory compliance requirements.## Improving Content Security with CDN Edge Authentication
Executive Summary
CDN edge authentication is a vital cybersecurity measure that verifies user identities before granting website access. By implementing CDN edge authentication, organizations can enhance content security, mitigate unauthorized access, and safeguard sensitive data from malicious actors. This comprehensive guide delves into the advantages, implementation methods, and best practices associated with CDN edge authentication, providing website owners with the knowledge and tools to protect their content effectively.
Introduction
In today’s digital landscape, securing website content is paramount. CDN edge authentication emerges as a robust solution, empowering organizations to protect their content from unauthorized access, data breaches, and malicious activities. By leveraging advanced authentication mechanisms at the edge of the content delivery network (CDN), this technique ensures that only authorized users are granted access to sensitive information, safeguarding data integrity and website security.
FAQ
Q: What is CDN edge authentication?
A: CDN edge authentication verifies user identities before granting access to website content, providing an additional layer of security against unauthorized access.
Q: Why is CDN edge authentication important?
A: CDN edge authentication prevents unauthorized users from accessing sensitive information, protects websites from data breaches and malicious activities, and enhances overall content security.
Q: How does CDN edge authentication work?
A: CDN edge authentication employs various methods, such as token-based authentication, certificate authentication, and multi-factor authentication, to verify user identities before granting access to content.
Subtopics
1. Types of CDN Edge Authentication
- Token-based authentication: Generates unique tokens for authorized users, allowing them to access content without providing credentials each time.
- Certificate authentication: Uses digital certificates to verify user identities, providing a secure and tamper-proof method of authentication.
- Multi-factor authentication: Requires multiple authentication factors, such as a password and a one-time code, to enhance security and prevent unauthorized access.
2. Benefits of CDN Edge Authentication
- Enhanced security: Protects website content from unauthorized access and malicious activities.
- Data breach prevention: Mitigates the risk of data breaches by preventing unauthorized users from accessing sensitive information.
- Improved user experience: Provides a seamless and secure user experience by eliminating the need for multiple logins.
3. Implementation Methods
- Cloud-based solutions: Leverage cloud-based platforms to implement CDN edge authentication with minimal infrastructure investment.
- On-premises solutions: Deploy authentication servers on-premises for greater control over security and data handling.
- Hybrid solutions: Combine cloud and on-premises elements to optimize security and scalability.
4. Best Practices
- Strong authentication mechanisms: Employ robust authentication methods, such as multi-factor authentication, to ensure maximum security.
- Regular security audits: Conduct regular security audits to identify and address potential vulnerabilities.
- User education and awareness: Educate users about the importance of strong passwords and safe online practices.
5. Use Cases
- E-commerce websites: Protect sensitive customer data, such as payment information, from unauthorized access.
- Healthcare portals: Safeguard patient health records and other confidential information from potential breaches.
- Financial institutions: Enhance the security of online banking and financial transactions.
Conclusion
CDN edge authentication is a powerful tool for securing website content and protecting sensitive data. By implementing effective authentication measures at the edge of the network, organizations can significantly reduce the risk of unauthorized access, data breaches, and other malicious activities. Embracing CDN edge authentication empowers businesses to maintain the integrity of their content, safeguard user privacy, and build trust among customers and stakeholders.
Keyword Tags
- CDN edge authentication
- Content security
- Authentication mechanisms
- Data breach prevention
- Enhanced user experience
