How Cloudflare Protects Against Phishing and Malware

Phishing is a type of cyberattack that attempts to trick users into revealing personal information, such as passwords or credit card numbers. Phishing emails typically look like they come from a legitimate source, such as a bank or a government agency, but they actually contain malicious links or attachments that can lead to data theft.
Malware is a type of malicious software that can damage computers or steal data. Malware can be spread through a variety of methods, including email attachments, malicious websites, and drive-by downloads.
Cloudflare offers a number of features and services that can help protect users from phishing and malware. These include:
- Email Security: Cloudflare Email Security uses machine learning to identify and block phishing emails. Email Security also blocks malware attachments and suspicious links.
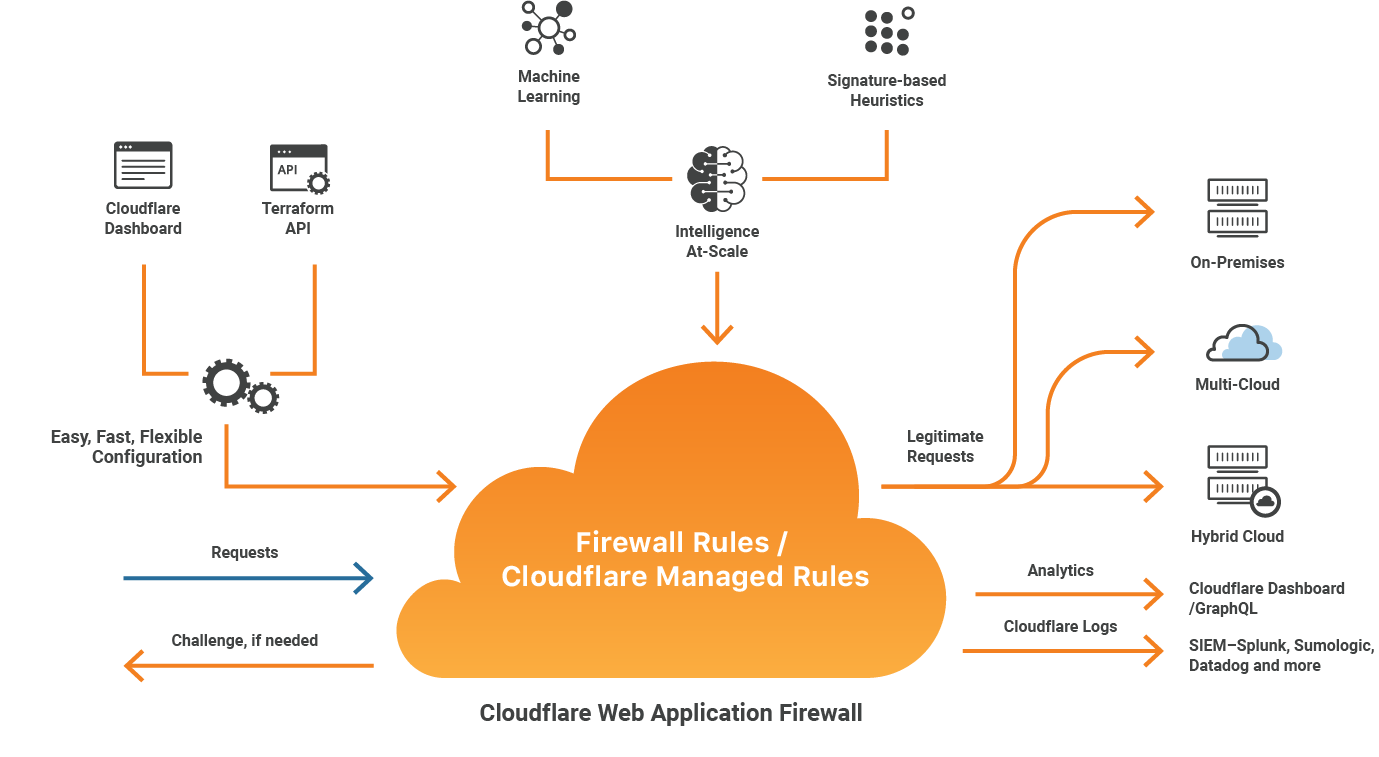
- Web Application Firewall (WAF): Cloudflare WAF helps to protect websites from malware and other attacks. WAF can block malicious traffic, such as SQL injection attacks and cross-site scripting attacks.
- Browser Isolation: Cloudflare Browser Isolation runs websites in a isolated environment, which helps to protect users from malware and phishing attacks. Browser Isolation stops malicious content from executing on the user’s computer.
- Zero Trust: Cloudflare Zero Trust is a security model that helps to protect organizations from phishing and malware attacks. Zero Trust requires users to authenticate themselves before they can access resources, even if they are on the corporate network.
Cloudflare’s phishing and malware protection features are easy to use and can be implemented quickly and easily. These features can help organizations and individuals to protect their data from cyberattacks.## How Cloudflare Protects Against Phishing and Malware
Executive Summary
Cloudflare is a global cloud platform that provides a suite of security services to protect businesses and individuals from cyber threats. These services include DDoS mitigation, web application firewall (WAF), bot management, and content delivery network (CDN). Cloudflare’s services are designed to protect against a wide range of attacks, including phishing and malware.
Introduction
Phishing and malware are two of the most common cyber threats facing businesses and individuals today. Phishing attacks attempt to trick users into revealing sensitive information, such as passwords or credit card numbers, by disguising themselves as legitimate emails or websites. Malware attacks attempt to infect devices with malicious software, which can damage files, steal data, or take control of the device.
Cloudflare’s security services can help to protect against phishing and malware attacks by:
- Blocking malicious traffic at the network edge
- Detecting and blocking phishing emails
- Scanning websites for malware
- Providing a CDN to deliver content quickly and securely
FAQs
1. What is phishing?
Phishing is a type of cyber attack that attempts to trick users into revealing sensitive information, such as passwords or credit card numbers, by disguising themselves as legitimate emails or websites.
2. What is malware?
Malware is a type of malicious software that can damage files, steal data, or take control of a device.
3. How can Cloudflare protect me from phishing and malware?
Cloudflare’s security services can help to protect against phishing and malware attacks by blocking malicious traffic at the network edge, detecting and blocking phishing emails, scanning websites for malware, and providing a CDN to deliver content quickly and securely.
Top 5 Subtopics
1. DDoS Mitigation
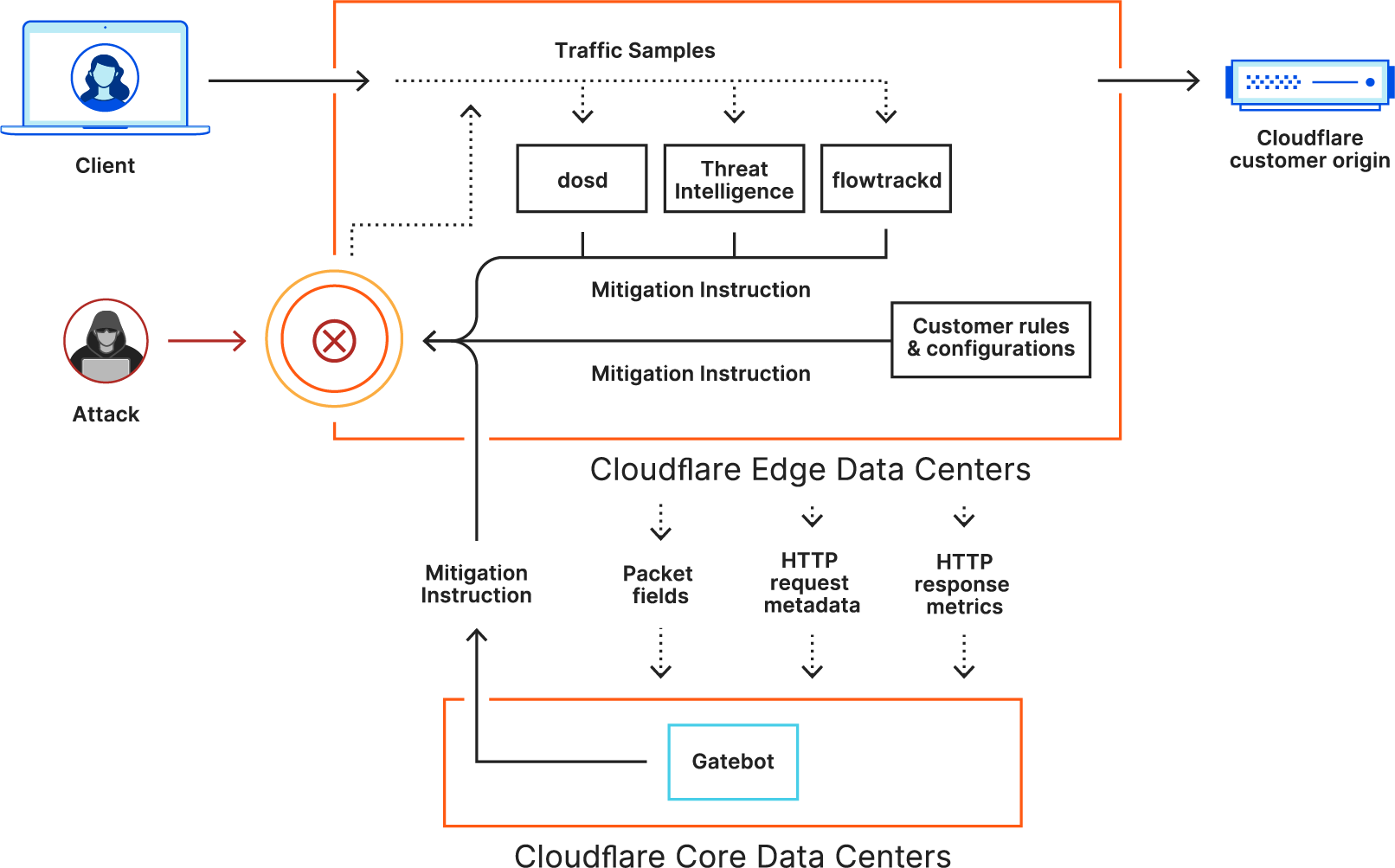
DDoS attacks are attempts to overwhelm a website or server with so much traffic that it becomes inaccessible. Cloudflare’s DDoS mitigation service can help to protect against these attacks by absorbing and dispersing attack traffic.
- Geoblocking: Blocking traffic from specific countries or regions
- Rate limiting: Limiting the number of requests that can be made from a single IP address
- Challenge-response: Requiring users to solve a challenge before accessing a website
2. Web Application Firewall (WAF)
A WAF is a security device that monitors and filters web traffic to block malicious requests. Cloudflare’s WAF can help to protect against a wide range of web attacks, including SQL injection, cross-site scripting, and buffer overflows.
- OWASP Top 10 protection: Protection against the ten most common web application vulnerabilities
- Custom rules: Ability to create custom rules to block specific types of attacks
- Bot management: Detection and blocking of malicious bots
3. Bot Management
Bots are automated scripts that can be used to perform a variety of tasks, including scraping data, spreading malware, and launching DDoS attacks. Cloudflare’s bot management service can help to identify and block malicious bots.
- Challenge-response: Requiring bots to solve a challenge before accessing a website
- Rate limiting: Limiting the number of requests that can be made from a single IP address
- Behavioral analysis: Analyzing bot behavior to identify malicious activity
4. Content Delivery Network (CDN)
A CDN is a network of servers that deliver content to users from the closest location, reducing latency and improving performance. Cloudflare’s CDN can help to protect against phishing and malware attacks by delivering content quickly and securely.
- SSL/TLS encryption: Encryption of all traffic between Cloudflare’s servers and users’ browsers
- HTTP/2 support: Support for the latest HTTP protocol, which improves performance and security
- WebSockets support: Support for WebSockets, a technology that allows for real-time communication between browsers and servers
5. Threat Intelligence
Threat intelligence is information about current and emerging cyber threats. Cloudflare’s threat intelligence team collects and analyzes data from a variety of sources to identify and mitigate threats.
- Global threat network: A network of sensors that collect data on cyber threats
- Machine learning: Use of machine learning to identify and block new threats
- Real-time updates: Continuous updates on the latest threats
Conclusion
Cloudflare’s security services can help to protect businesses and individuals from a wide range of cyber threats, including phishing and malware. These services are designed to be easy to use and affordable, making them a valuable addition to any security strategy.
Keyword Tags
- Cloudflare
- Phishing
- Malware
- DDoS mitigation
- Web application firewall (WAF)
- Bot management
- Content delivery network (CDN)

