Ethical Hacking Insights: Learning from Security Penetration Testing
Security penetration testing, a pivotal aspect of ethical hacking, serves as a crucial avenue for organizations to evaluate and strengthen their cybersecurity posture. By simulating real-world attack scenarios, penetration testers uncover vulnerabilities and weaknesses that could otherwise be exploited by malicious actors. This practice offers invaluable insights, enabling organizations to prioritize their security investments and mitigate potential risks.

1. Understanding Attacker Techniques:

Penetration testing provides a unique opportunity to observe the tactics and techniques employed by attackers. Skilled penetration testers possess advanced knowledge of hacking tools and methodologies, allowing them to identify vulnerabilities and exploit them in a controlled manner. By studying these techniques, organizations can gain a deep understanding of the threats they face and develop countermeasures to prevent unauthorized access.
2. Identifying System Weaknesses:
Penetration testing involves a thorough examination of an organization’s systems and infrastructure, both internal and external. By conducting vulnerability scans, probing networks, and assessing application security, testers reveal weaknesses that could compromise confidential data or disrupt operations. Organizations can then prioritize remediation efforts, focusing on addressing the most critical vulnerabilities and hardening their systems against potential attacks.
3. Enhancing Security Awareness:
Security penetration testing raises awareness within organizations about the importance of cybersecurity. By exposing potential vulnerabilities, testers demonstrate the real-world consequences of security negligence. This awareness encourages employees to practice proper security measures, such as using strong passwords, being cautious about phishing emails, and reporting suspicious activities.
4. Validating Security Controls:
Penetration testing serves as a litmus test for an organization’s existing security controls. By attempting to bypass or evade these controls, testers evaluate their effectiveness. Organizations can then refine their security strategies, implementing additional measures or enhancing existing ones to ensure comprehensive protection against evolving threats.
5. Continuous Improvement:
Security penetration testing is an ongoing process, as new vulnerabilities emerge constantly. By regularly conducting tests, organizations can proactively identify and address emerging threats, adapting their security measures to meet the dynamic cybersecurity landscape. Continuous testing ensures the ongoing effectiveness of an organization’s security posture, minimizing the likelihood of successful attacks.
Conclusion:
Security penetration testing provides invaluable insights that empower organizations to enhance their cybersecurity strategies and mitigate potential risks. Ethical hackers can uncover vulnerabilities, identify attacker techniques, and validate security controls. By learning from these insights, organizations can strengthen their defenses, protect confidential information, and ensure the continuous security of their critical assets in the face of evolving threats.## Ethical Hacking Insights: Learning From Security Penetration Testing
Executive Summary
Ethical hacking, the art of testing a computer system, network, or software application to find vulnerabilities, has evolved into a valuable tool in the realm of cybersecurity. By emulating the methods of malicious actors, ethical hackers identify weaknesses that could be exploited by attackers. This practice, commonly known as security penetration testing, empowers organizations to proactively address security risks and strengthen their cybersecurity posture.
Introduction
In today’s highly interconnected digital landscape, organizations face a constant threat from cybercriminals and malicious actors. Protecting sensitive data and critical infrastructure requires a proactive approach that goes beyond traditional reactive measures. Ethical hacking is becoming an increasingly indispensable component of cybersecurity strategies, offering substantial benefits in the identification and mitigation of potential security breaches.
FAQs
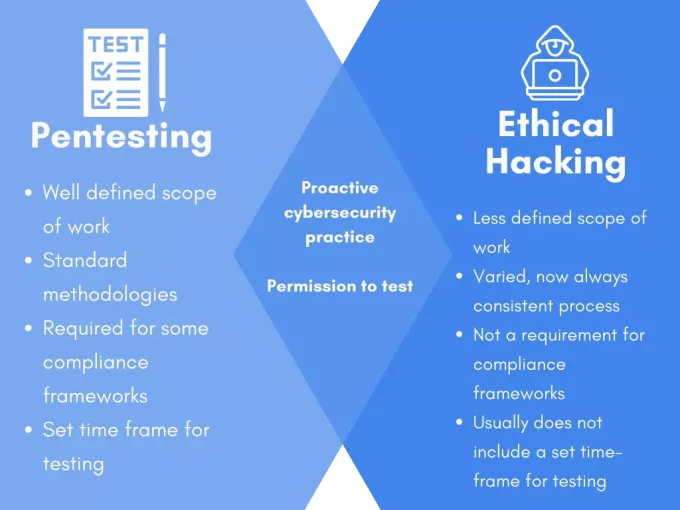
1. What is the difference between ethical hacking and malicious hacking?
Ethical hacking is a legitimate and authorized practice conducted to identify vulnerabilities and improve security. Malicious hacking, on the other hand, involves unauthorized access or destruction of computing systems for illegal or malicious purposes.
2. Is it legal to perform ethical hacking?
Yes, ethical hacking is legal when conducted with proper authorization and in accordance with ethical guidelines and relevant laws. Organizations typically engage ethical hackers through penetration testing companies or hire them as part of their cybersecurity team.
3. What are the benefits of penetration testing?
Penetration testing provides numerous benefits, including:
- Identifying security vulnerabilities and weaknesses
- Assessing the effectiveness of existing security measures
- Improving security policies and procedures
- Meeting compliance requirements and industry standards
Key Subtopics
1. Vulnerability Assessment
Vulnerability assessment involves identifying and evaluating potential weaknesses in a system, network, or application. These weaknesses can result from software bugs, misconfigurations, or design flaws.
- Common vulnerability scoring system (CVSS): A standardized framework for assessing the severity of vulnerabilities.
- Penetration testing tools: Automated and manual tools specifically designed to exploit vulnerabilities and test security.
- Threat modeling: Identifying and prioritizing potential threats based on their likelihood and impact.
2. Security Penetration Testing
This is the process of simulating real-world attacks to identify vulnerabilities and weaknesses in an organization’s defenses. Penetration testers use a variety of techniques, including:
- Black-box testing: Testing without prior knowledge of the target system.
- White-box testing: Testing with full knowledge of the target system’s architecture and design.
- Gray-box testing: Testing with partial knowledge of the target system.
3. Network Security
Penetration testing of network infrastructure involves identifying weaknesses in firewalls, routers, switches, and other network devices. Common techniques include:
- Port scanning: Identifying open ports and services on target hosts.
- Vulnerability scanning: Using automated tools to locate known vulnerabilities in network devices.
- Packet sniffing: Monitoring and analyzing network traffic to identify suspicious activity.
4. Web Application Security
Penetration testing of web applications involves identifying vulnerabilities in web servers, databases, and application code. Common techniques include:
- SQL injection: Attacking a web application by injecting malicious SQL queries.
- Cross-site scripting (XSS): Exploiting vulnerabilities that allow attackers to inject malicious scripts into a web application.
- Buffer overflow: Exploiting vulnerabilities that allow attackers to corrupt system memory.
5. Social Engineering
This type of penetration testing involves using social manipulation techniques to gain access to sensitive data or systems. Common techniques include:
- Phishing emails: Tricking users into clicking on malicious links or downloading malware attachments.
- Spear phishing: Targeting specific individuals or organizations with tailored phishing emails.
- Smishing: Targeting users with malicious SMS messages.
Conclusion
Ethical hacking, particularly through penetration testing, is a vital weapon in the arsenal of any organization seeking to strengthen its cybersecurity defenses. By identifying and addressing vulnerabilities before malicious actors can exploit them, organizations can significantly reduce the risk of data breaches and damage to their reputation and operations.
Relevant Keyword Tags
- Ethical hacking
- Security penetration testing
- Vulnerability assessment
- Web application security
- Social engineering



