Enhancing Application Security With OAuth and JWT
In today’s digital landscape, web and mobile applications are essential for businesses of all sizes. However, these applications are also potential targets for malicious attacks. To protect against these threats, developers must implement robust security measures at every stage of the development lifecycle.

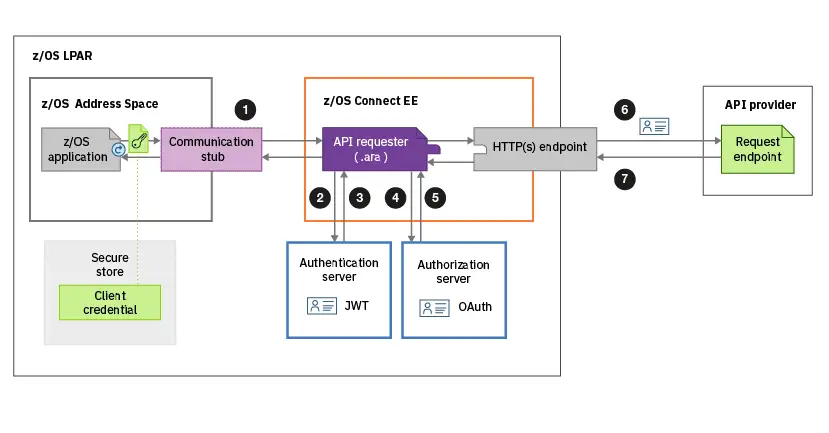
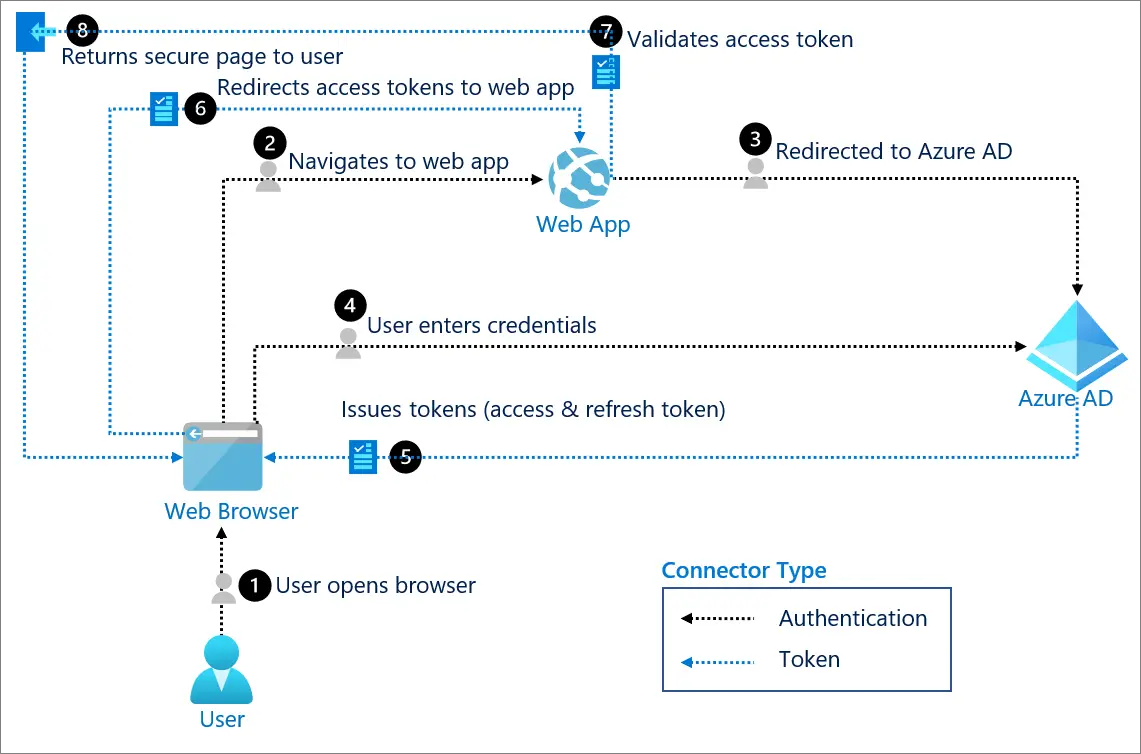
OAuth and JWT are two widely used technologies that can significantly enhance the security of web and mobile applications. OAuth (Open Authorization) is an open-standard authorization framework that allows users to grant third-party applications access to their resources without sharing their credentials. JWT (JSON Web Token) is a compact and self-contained way to represent claims between two parties.
OAuth provides a number of benefits for application security. First, it eliminates the need for users to create and manage multiple passwords for different applications. This reduces the risk of password fatigue and makes it less likely that users will choose weak passwords. Second, OAuth allows users to control the level of access that third-party applications have to their resources. This helps to prevent malicious applications from accessing sensitive data or performing unauthorized actions.
JWT also provides several security benefits for web and mobile applications. First, JWTs are digitally signed, which means that they cannot be tampered with without invalidating the signature. This helps to protect against data tampering and replay attacks. Second, JWTs are self-contained, which means that they do not require access to a database or other external resources to verify their claims. This makes them ideal for use in scenarios where the application needs to be able to verify the user’s identity without having to make a request to a server.
Combining OAuth and JWT can provide even greater security benefits for web and mobile applications. For example, OAuth can be used to authenticate users with a third-party service, such as Google or Facebook. Once the user is authenticated, a JWT can be issued that contains claims about the user’s identity and level of access. This JWT can then be used to authorize the user to access the application’s resources.
By implementing OAuth and JWT, developers can significantly enhance the security of their web and mobile applications. These technologies can help to protect against a wide range of attacks, including phishing, password attacks, and data tampering. As a result, OAuth and JWT are essential tools for any developer who is serious about protecting their application’s data and users.
