Table of Contents
Effective Firewall Management With Iptables
Executive Summary
This document provides a comprehensive guide to effective firewall management with Iptables, a powerful firewall tool in the Linux operating system. It covers the key aspects of firewall configuration, including setting up basic rules, advanced rule creation, and logging and monitoring mechanisms.
Introduction
Firewalls play a crucial role in protecting network systems from unauthorized access and malicious attacks. Iptables is a versatile firewall tool that allows administrators to define and enforce detailed firewall rules. This guide provides a step-by-step approach to configuring and managing Iptables for enhanced network security.
Subtopics
1. Basic Firewall Configuration
- Define Default Policy: Establish the default action for incoming and outgoing traffic when no specific rules are matched.
- Allow Essential Services: Create rules to permit traffic for necessary services, such as web browsing and email.
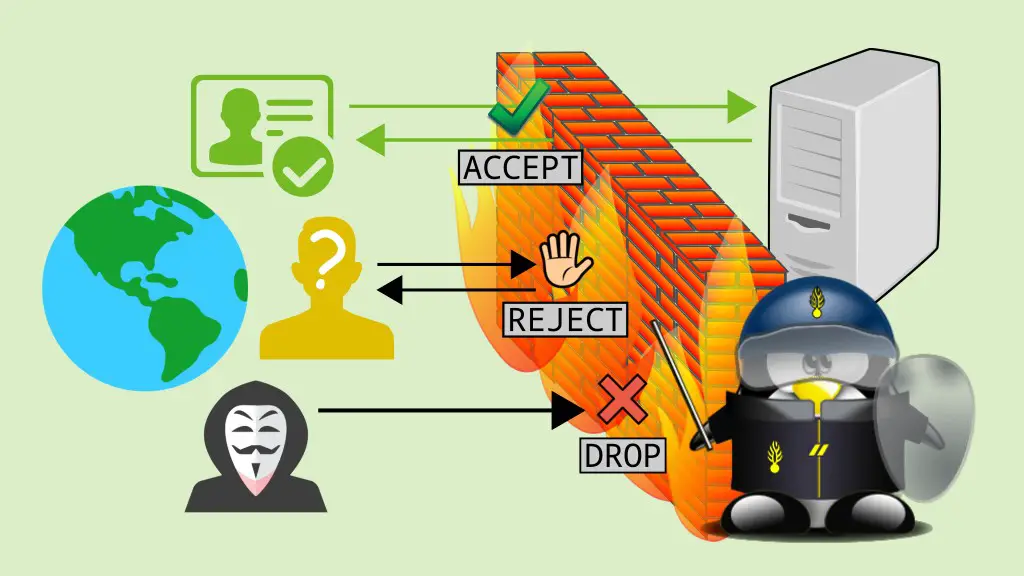
- Block Unwanted Traffic: Create rules to drop or reject traffic from specific sources or for specific protocols.
- Handle Loopback Traffic: Configure rules to allow traffic on the loopback interface.
- Persist Rules Across Reboots: Save firewall rules to a persistent configuration file to ensure they remain in effect after system restarts.
2. Advanced Rule Creation
- Use Chain Targets: Group related rules into chains for better organization and control.
- Implement State Tracking: Establish rules based on the state of network connections, such as established or related.
- Control Destination Traffic: Create rules to allow or block traffic to specific destination addresses or ports.
- Specify Time-Based Rules: Define rules that apply only during specific time periods.
- Use IP Sets: Define IP sets to group IP addresses and apply rules to the sets instead of individual IP addresses.
3. Logging and Monitoring
- Enable Logging: Configure Iptables to log all traffic that matches the rules.
- Specify Log Level: Determine the level of detail to record in the logs, from informational to debugging.
- Monitor Log Files: Regularly review log files to identify suspicious activity and potential security threats.
- Use Log Analyzers: Utilize tools like Logwatch to analyze log files and detect patterns or trends.
- Set Up Alerts: Establish alerts to notify administrators about critical events or security breaches.
4. Performance Optimization
- Minimize Rule Complexity: Keep firewall rules simple and easy to understand to optimize performance.
- Use Standard Rule Sets: Utilize pre-defined rule sets or open-source frameworks to reduce manual configuration.
- Reduce Loopback Traffic: Avoid unnecessary traffic on the loopback interface to improve performance.
- Optimize Rule Placement: Arrange rules in a logical order to reduce packet processing time.
- Consider Hardware Firewalls: Explore hardware-based firewalls for high-performance network protection.
5. Best Practices
- Maintain Regular Updates: Keep the Iptables software and operating system up to date with latest security patches.
- Test Rules Thoroughly: Test all firewall rules carefully before implementing them live to avoid unintended consequences.
- Document Firewall Policies: Create clear documentation that explains the purpose and configuration of the firewall rules.
- Implement Intrusion Detection Systems: Supplement Iptables with intrusion detection systems to enhance security.
- Train Personnel: Ensure that network administrators are properly trained on Iptables and firewall management.
Conclusion
Effective firewall management with Iptables requires a comprehensive understanding of the tool and its capabilities. By following the principles outlined in this guide, administrators can establish robust firewall configurations that protect network systems from unauthorized access and malicious attacks. Regular monitoring, performance optimization, and adherence to best practices are key to ensuring ongoing network security.
Keyword Phrase Tags
- Iptables Firewall Management
- Network Security
- Firewall Configuration
- Advanced Iptables Rules
- Firewall Best Practices



This article is very well-written and provides a lot of valuable information on how to effectively manage your firewall with Iptables. I found the section on how to create and manage custom rules to be particularly helpful.
I’m not sure I agree with the author’s recommendation to allow all incoming traffic on port 80. I think it’s important to be more restrictive with your firewall rules to protect your system from attack.
The author does a good job of explaining the basics of Iptables, but I would have liked to see more advanced examples of how to use the tool. For example, how to create rules to block specific types of traffic or how to set up a firewall for a web server.
I found this article to be very helpful. I’m new to Iptables, and this article gave me a good understanding of the basics. I especially appreciated the examples.
This article is a waste of time. The author doesn’t provide any new information that you can’t find in the Iptables documentation.
I think the author did a good job of explaining the basics of Iptables. However, I would have liked to see more information on how to troubleshoot common problems.
I’m not sure I agree with the author’s recommendation to allow all incoming traffic on port 80. I think it’s important to be more restrictive with your firewall rules to protect your system from attack.
This article is very well-written and provides a lot of valuable information on how to effectively manage your firewall with Iptables. I found the section on how to create and manage custom rules to be particularly helpful.
I’m not sure I agree with the author’s recommendation to allow all incoming traffic on port 80. I think it’s important to be more restrictive with your firewall rules to protect your system from attack.
I think the author did a good job of explaining the basics of Iptables. However, I would have liked to see more information on how to troubleshoot common problems.
I’m not sure I agree with the author’s recommendation to allow all incoming traffic on port 80. I think it’s important to be more restrictive with your firewall rules to protect your system from attack.
This article is very well-written and provides a lot of valuable information on how to effectively manage your firewall with Iptables. I found the section on how to create and manage custom rules to be particularly helpful.
I’m not sure I agree with the author’s recommendation to allow all incoming traffic on port 80. I think it’s important to be more restrictive with your firewall rules to protect your system from attack.
This article is very well-written and provides a lot of valuable information on how to effectively manage your firewall with Iptables. I found the section on how to create and manage custom rules to be particularly helpful.