Edge Computing Errors: Challenges In Edge Device Programming
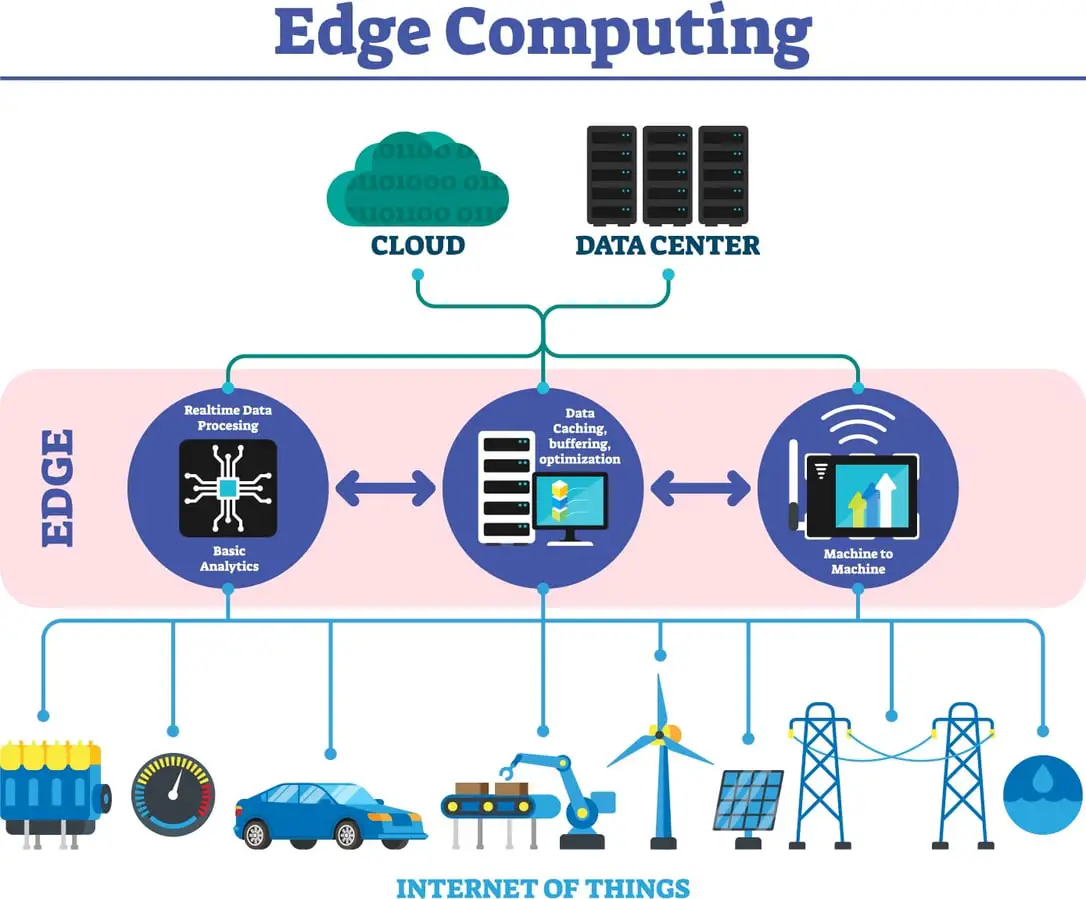
Edge computing has emerged as a critical paradigm shift in the modern digital landscape, offering benefits such as reduced latency, improved responsiveness, and increased privacy. While Edge computing holds immense promise, it also presents unique challenges in device programming. These challenges stem from various factors, including resource constraints, network limitations, and the need for reliable and secure device management.
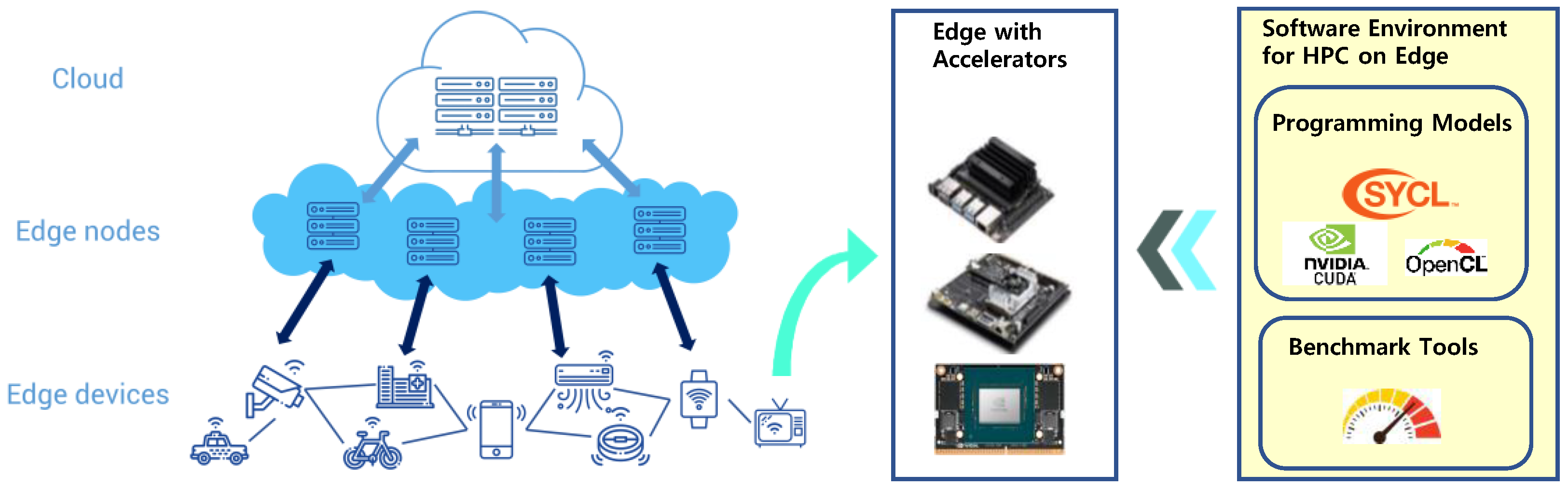
Resource Constraints and Limited Computation Power
Edge devices often have limited computational power and constrained resources compared to traditional cloud-based systems. This limitation can pose significant challenges when executing complex code or running resource-intensive applications at the edge. Developers must carefully optimize their code and leverage efficient data structures to ensure the device can handle the required workload without sacrificing performance.
Network Limitations and Latency Variability
Edge devices often operate in challenging network environments, where connectivity can be unreliable or intermittent. Packet loss, high latency, and bandwidth limitations can affect the performance and reliability of Edge computing applications. Developers must design their applications to be tolerant of network disruptions and implement appropriate error handling mechanisms to ensure data integrity and application stability.
Device Management and Security
Edge devices can be deployed in remote or unattended locations, making device management a critical concern. Establishing robust and secure methods for device provisioning, software updates, and remote troubleshooting is essential to maintain the integrity and security of Edge computing systems. Additionally, measures must be taken to protect devices from unauthorized access, data breaches, and malicious attacks.
Debugging and Troubleshooting
Debugging and troubleshooting Edge computing applications can be challenging due to the distributed nature of the systems. Developers must carefully monitor the devices and applications, leveraging logging and telemetry to identify errors and performance issues. Remote debugging tools and techniques can assist in diagnosing and resolving problems without requiring physical access to the devices.
Conclusion
Edge computing offers significant potential for improving the performance and efficiency of various applications. However, the challenges associated with Edge device programming, such as resource constraints, network limitations, and device management, require careful consideration. By understanding these challenges and adopting appropriate strategies, developers can effectively create and deploy reliable and scalable Edge computing solutions that unlock the full potential of this transformative technology.## Edge Computing Errors: Challenges In Edge Device Programming
Executive Summary
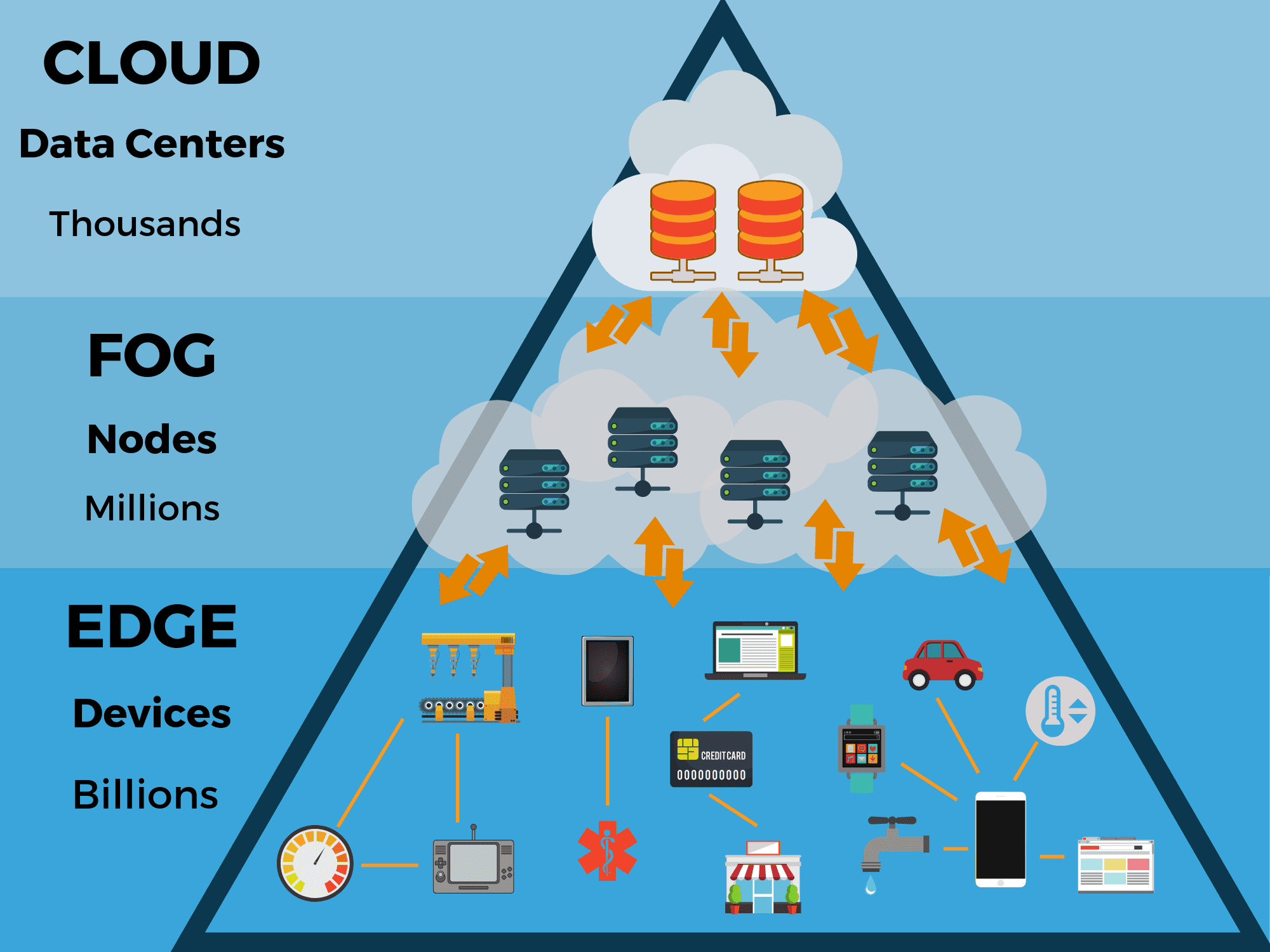
Edge computing is a distributed computing paradigm that brings computation and storage resources closer to the devices and sensors that generate and consume data. This can provide several benefits, such as reduced latency, improved bandwidth, and increased security. However, edge computing also introduces new challenges, including the need to program and manage edge devices.
This document identifies and describes some of the common challenges in edge device programming. It also provides some tips and best practices for overcoming these challenges.
Introduction
Edge devices are typically small, low-power devices with limited resources. This can make it difficult to program and manage these devices. In addition, edge devices are often deployed in remote or harsh environments, which can further complicate programming and management.
FAQs
-
What are the most common challenges in edge device programming?
- Some of the most common challenges in edge device programming include:
- Resource constraints: Edge devices are typically small, low-power devices with limited resources. This can make it difficult to program and manage these devices.
- Remote deployment: Edge devices are often deployed in remote or harsh environments, which can further complicate programming and management.
- Security: Edge devices are often connected to the Internet, which can make them vulnerable to security attacks.
- Some of the most common challenges in edge device programming include:
-
How can I overcome the challenges of edge device programming?
- There are several things you can do to overcome the challenges of edge device programming, including:
- Use the right tools: There are a number of tools and frameworks that can help you program and manage edge devices. These tools can help you to overcome resource constraints, remote deployment, and security challenges.
- Follow best practices: There are a number of best practices that you can follow to make it easier to program and manage edge devices. These best practices include using a modular approach, testing your code thoroughly, and using a version control system.
- Work with a partner: If you are not familiar with edge device programming, you may want to work with a partner who can help you. A partner can provide you with the expertise and support that you need to successfully program and manage your edge devices.
- There are several things you can do to overcome the challenges of edge device programming, including:
-
What are the benefits of using edge computing?
- Edge computing can provide several benefits, including:
- Reduced latency: Edge computing can reduce latency by bringing computation and storage resources closer to the devices and sensors that generate and consume data. This can improve the performance of applications that require real-time data processing.
- Improved bandwidth: Edge computing can improve bandwidth by reducing the amount of data that needs to be transmitted over the network. This can free up bandwidth for other applications and services.
- Increased security: Edge computing can increase security by reducing the risk of data breaches. This is because edge devices are often deployed in remote or harsh environments, which can make them more difficult to access by unauthorized users.
- Edge computing can provide several benefits, including:
Challenges in Edge Device Programming
Resource Constraints
Edge devices are typically small, low-power devices with limited resources. This can make it difficult to program and manage these devices.
- Limited memory: Edge devices typically have limited memory, which can make it difficult to store code and data on the device.
- Limited processing power: Edge devices typically have limited processing power, which can make it difficult to run complex computations on the device.
- Limited battery life: Edge devices often run on batteries, which can limit the amount of time that the device can be used without being recharged.
Remote Deployment
Edge devices are often deployed in remote or harsh environments, which can further complicate programming and management.
- Difficult access: Edge devices are often deployed in remote or harsh environments, which can make it difficult to access the devices for programming and management.
- Environmental factors: Edge devices are often deployed in harsh environments, such as extreme temperatures or high humidity, which can damage the devices or interfere with their operation.
- Security risks: Edge devices are often connected to the Internet, which can make them vulnerable to security attacks.
Security
Edge devices are often connected to the Internet, which can make them vulnerable to security attacks.
- Data breaches: Edge devices can be used to collect sensitive data, such as personal information or financial data. If this data is not properly protected, it could be stolen or used for malicious purposes.
- Denial of service attacks: Edge devices can be used to launch denial of service attacks, which can disrupt the operation of other devices or networks.
- Malware infections: Edge devices can be infected with malware, which can damage the device or steal data.
Conclusion
Edge computing is a new and rapidly evolving paradigm that has the potential to revolutionize the way we collect, process, and store data. However, edge computing also introduces new challenges, including the need to program and manage edge devices.
This document has identified and described some of the common challenges in edge device programming. It has also provided some tips and best practices for overcoming these challenges. By following these tips and best practices, you can make it easier to program and manage your edge devices and take advantage of the benefits of edge computing.
Keyword Tags
- edge computing
- edge device programming
- challenges
- resource constraints
- remote deployment
- security

