Distributed Denial of Service (DDoS) Defense Dilemmas: Protecting Your Applications
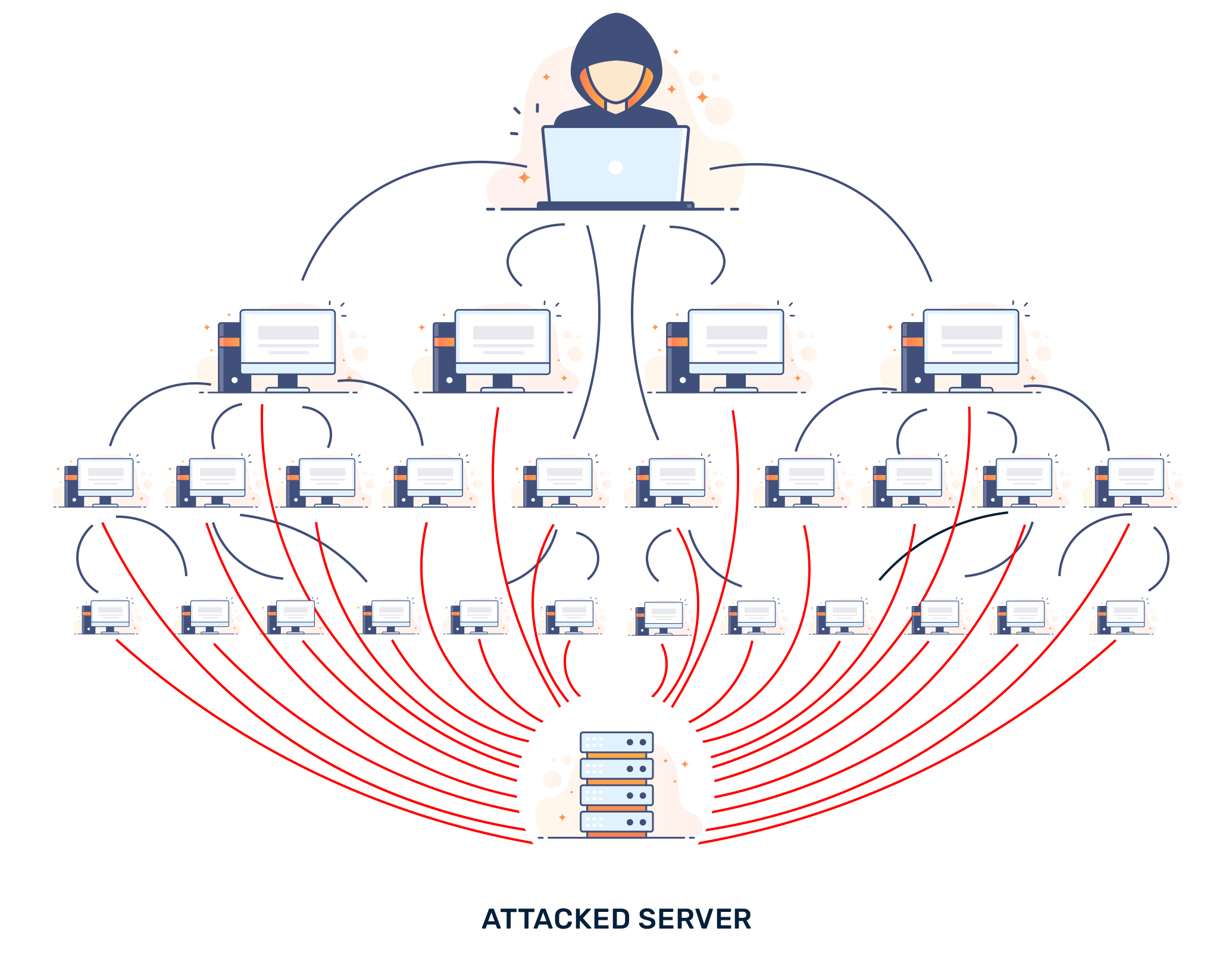
Distributed Denial of Service (DDoS) attacks pose a significant threat to the availability and integrity of online applications. These attacks involve flooding a target system with a large volume of traffic, overwhelming its resources and rendering it inaccessible. Protecting against DDoS attacks requires a comprehensive defense strategy that addresses the unique challenges and dilemmas associated with this type of attack.

Detection and Mitigation Challenges
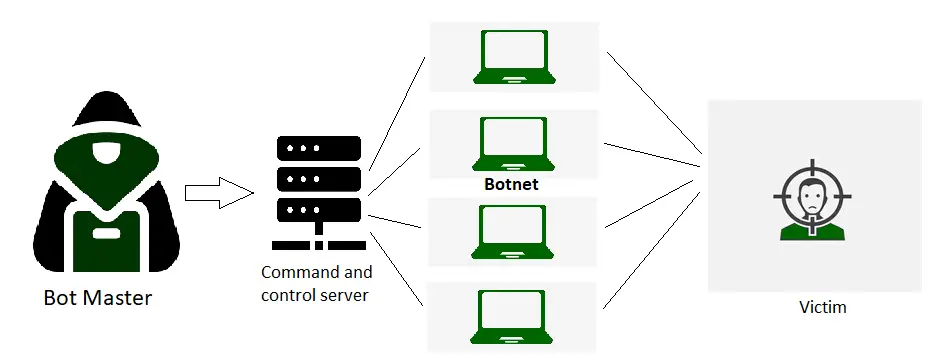
One of the primary challenges in DDoS defense is detecting and mitigating attacks in real-time. DDoS attacks often originate from multiple sources, making it difficult to identify and block the malicious traffic. Additionally, attackers are constantly evolving their techniques, making it challenging to develop and implement effective defense mechanisms.
Resource Consumption
DDoS attacks can consume significant amounts of resources on the target system, including bandwidth, CPU, and memory. Mitigating these attacks requires deploying dedicated hardware and software solutions, which can be costly and complex to manage. Organizations must balance the need for effective DDoS protection with the cost and resource constraints of their infrastructure.
False Positives and Legitimate Traffic
DDoS defense systems often rely on heuristics to identify malicious traffic, which can lead to false positives. This can result in legitimate users being blocked from accessing the target system, potentially harming the organization’s reputation and customer satisfaction. Finding the right balance between detecting and blocking malicious traffic while minimizing false positives is crucial.
Evasive Attacks
Modern DDoS attacks employ various evasion techniques to bypass traditional defense mechanisms. Attackers may use techniques such as encryption, spoofing, and rate-limiting to make their attacks less detectable and harder to mitigate. Defenders must adopt innovative and adaptive defense strategies that can effectively handle evasive attacks.
Proactive Defense Strategies
To address the challenges of DDoS defense, organizations should adopt proactive strategies that include:
- Building Resilient Infrastructure: Implement load balancers, firewalls, and intrusion detection systems to enhance the system’s ability to withstand DDoS attacks.
- Deploying DDoS Mitigation Services: Consider using cloud-based or third-party DDoS mitigation services that provide advanced filtering and blocking capabilities.
- Educating Users and Staff: Educate users and staff about DDoS attacks and best practices for reporting suspicious activity.
- Regular Testing and Simulation: Conduct regular DDoS testing and simulation exercises to assess the effectiveness of defense mechanisms and identify areas for improvement.
Protecting against DDoS attacks is an ongoing challenge that requires a multi-faceted approach. By understanding the dilemmas associated with DDoS defense and adopting proactive strategies, organizations can enhance the availability and integrity of their applications, minimize the impact of attacks, and ensure the continuous operation of their critical services.Distributed Denial Of Service (DDoS) Defense Dilemmas: Protecting Your Applications
Executive Summary
Distributed Denial of Service (DDoS) attacks pose a significant threat to businesses of all sizes. These attacks can cause websites and applications to become unavailable, resulting in lost revenue, reputational damage, and frustrated customers. Preparing a robust DDoS defense strategy is vital for mitigating these risks and safeguarding the reputation of your organization.
Introduction
DDoS attacks originate from multiple devices using different IP addresses and often target the network, application layer, or DNS infrastructure. Understanding the complexities of DDoS attacks, various protection mechanisms, and best practices to effectively mitigate DDoS threats is vital.
Frequently Asked Questions (FAQs)
-
What are the signs of a DDoS attack?
- Abnormally high traffic volume
- Slow website or application performance
- Inability to access the website or application
-
How can I protect my website or application from DDoS attacks?
- Implement DDoS mitigation measures such as rate limiting, firewalls, and DDoS-specific filtering tools
- Partner with a DDoS mitigation provider
- Train staff on DDoS detection and response protocols
-
What are the consequences of a DDoS attack?
- Website or application downtime
- Lost revenue
- Reputational damage
Top 5 Subtopics
1. DDoS Mitigation Techniques
Describes various DDoS mitigation techniques, such as:
- Firewalls: Identify and block malicious traffic based on pre-defined rules
- Rate limiting: Restricts the number of requests a device or IP address can make in a given time
- DDoS filtering tools: Detect and mitigate DDoS attacks in real-time
2. Cloud-Based DDoS Protection
Explores cloud-based DDoS protection services, such as:
- Managed DNS protection: Shields DNS infrastructure from DDoS attacks
- Web application firewalls: Filter malicious traffic targeting web applications
- Global network protection: Distributes traffic across multiple nodes to minimize the impact of DDoS attacks
3. DDoS Detection and Response
Emphasizes the importance of timely DDoS detection and effective response measures, such as:
- Monitoring tools: Track network traffic for anomalies and DDoS activity
- Incident response plan: Outline clear responsibilities and actions for DDoS handling
- Mitigation strategies: Prepare pre-determined responses to different types of DDoS attacks
4. DDoS Best Practices
Outlines best practices for DDoS prevention and mitigation, such as:
- Regular security audits: Identify and address vulnerabilities that could be exploited by DDoS attacks
- Staff training: Train staff on DDoS detection, response, and reporting procedures
- Regular patching and updates: Ensure that software and systems are up-to-date with the latest security patches
5. Emerging DDoS Trends
Highlights emerging DDoS trends and their implications, such as:
- Increased sophistication and volume of attacks: Advanced DDoS techniques and botnets pose new challenges for defense
- Internet of Things (IoT) devices as attack vectors: Exploited IoT devices can participate in DDoS attacks
- Targeted DDoS attacks: Attacks focus on specific organizations or infrastructure
Conclusion
DDoS attacks are serious threats to businesses and organizations. Implementing a comprehensive DDoS defense strategy that includes a combination of techniques, cloud-based protection, detection, response, best practices, and monitoring emerging trends is crucial. By addressing the complexities of DDoS attacks and understanding the available defense mechanisms, organizations can effectively mitigate these threats and safeguard the availability and reputation of their digital assets.
Relevant Keyword Tags
- Distributed Denial of Service
- DDoS Protection
- DDoS Mitigation
- Cloud-Based DDoS Protection
- DDoS Response
