Decompiling Code: A Comprehensive Guide to Reverse Engineering Software
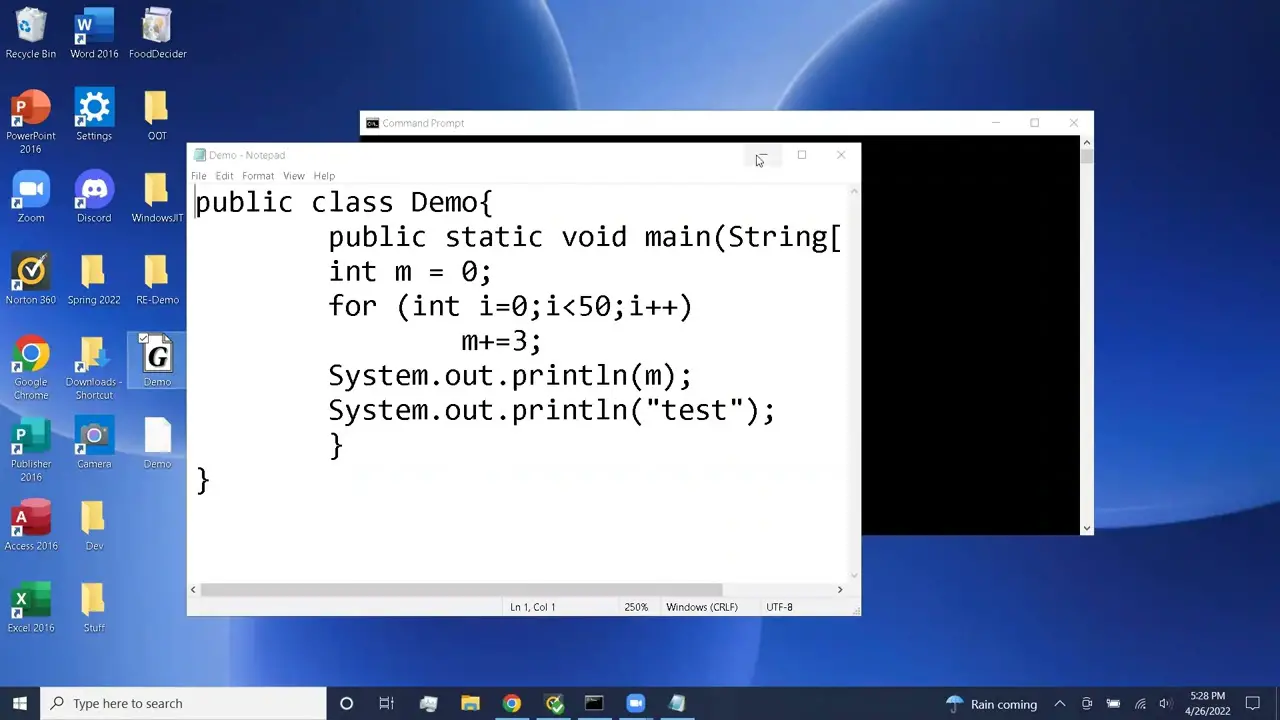
Reverse engineering software involves disassembling compiled code back into its original source code or a human-readable format. One of the key techniques used in reverse engineering is decompilation. Decompilers are tools that automate this process, converting compiled code into a high-level programming language representation.

Understanding Decompilation
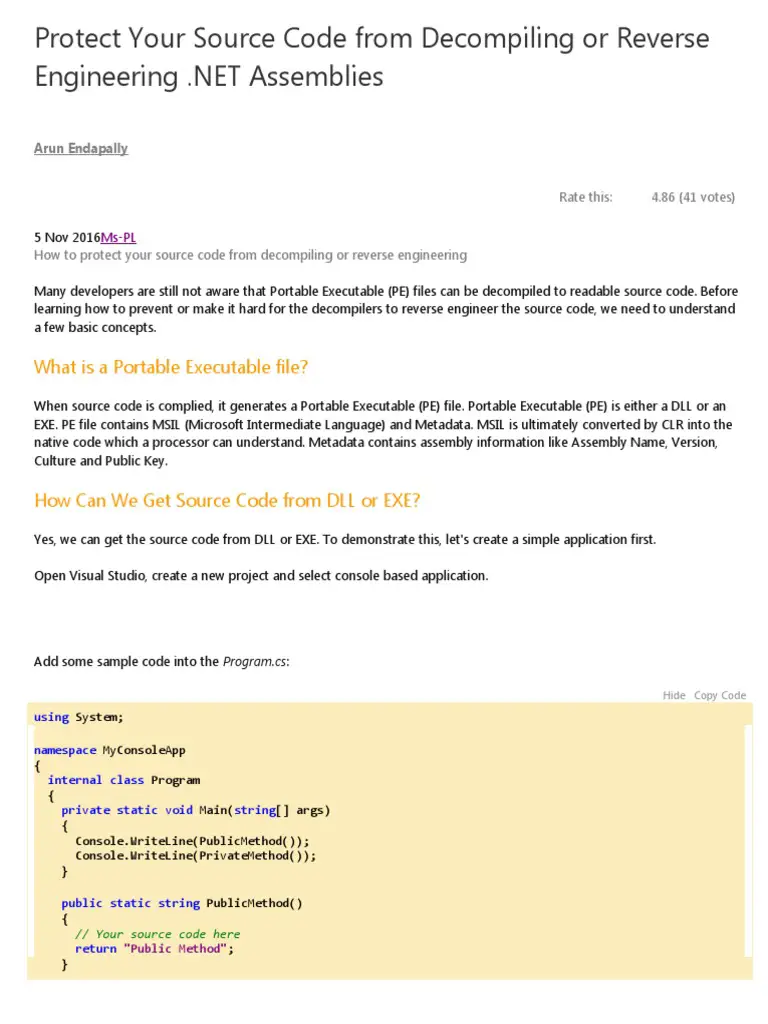
Decompilation is a complex process that involves several steps. Firstly, the decompiler analyzes the compiled code to understand its structure and functionality. It then attempts to reconstruct the original source code by identifying variables, functions, and control flow statements.
The accuracy of decompiled code depends on various factors, including the decompiler’s capabilities, the complexity of the compiled code, and the availability of additional information such as symbol tables or debugging information.
Applications of Decompilation
Decompilation serves various purposes, including:
-
Debugging and Maintenance: Decompiling code can be useful in debugging or maintaining legacy software for which the original source code is unavailable.
-
Security Analysis: Decompilers are often used in security analysis to identify vulnerabilities or malicious code in software.
-
Software Compatibility: Decompilation can be employed to create compatible versions of software for different platforms or operating systems.
-
Educational Purposes: Decompilers can be valuable tools for learning about the inner workings of software and understanding programming techniques.
Challenges in Decompilation
Decompilation can be challenging due to several reasons:
-
Obscured Code: Compiled code often undergoes optimizations and transformations, making it harder to decompile.
-
Lack of Information: The absence of symbol tables or debugging information can make decompilation more difficult.
-
Incomplete or Inaccurate Results: Decompilers may produce incomplete or inaccurate source code, especially for complex programs.
-
Legal and Ethical Considerations: Decompiling copyrighted software without permission may raise legal and ethical concerns.
Decompilation Tools
Numerous decompilation tools are available, both open-source and commercial. Some popular options include:
-
Ghidra: A free and open-source decompiler developed by the National Security Agency (NSA).
-
IDA Pro: A commercial decompiler known for its powerful features and customization options.
-
Jad: A popular Java decompiler known for its accuracy and ease of use.
-
CodeCracker: A free and open-source decompiler for C/C++ code.
-
CFR: A Java decompiler that focuses on readability and maintaining the original code’s structure.
Choosing the Right Decompiler
The choice of decompiler depends on several factors:
-
Programming Language: Consider the programming language used in the compiled code. Not all decompilers support all languages.
-
Complexity of Code: The complexity of the compiled code affects the decompiler’s ability to produce accurate results.
-
Availability of Information: Assess whether symbol tables or debugging information is available, as these can aid decompilation.
-
Purpose: Consider the intended use of the decompiled code, whether it’s for debugging, security analysis, or educational purposes.
Conclusion
Decompilation is a powerful technique that enables the reverse engineering of software. It involves disassembling compiled code into a human-readable format. Decompilation has various applications, including debugging, security analysis, software compatibility, and educational purposes. While decompilation tools are readily available, the process itself can be challenging due to factors such as code complexity and the availability of information. Choosing the right decompiler and understanding the limitations are crucial for successful decompilation.Decompiling Code: A Guide To Reverse Engineering Software
H2: Executive Summary
Decompiling code is a process used to investigate the inner workings of a program by recovering its source code from its machine code. It allows programmers and developers to examine the structure and functionality of software, improve code efficiency, enhance security, troubleshoot errors, and more. With continued advancements in technology, decompilation techniques have become more powerful and versatile, opening up new opportunities for deeper analysis and understanding of software.
Introduction
Reverse engineering software through decompilation is a complex process that involves dissecting the executable code into its constituent components and reconstructing the source code. By cracking open the inner workings of a program, reverse engineering can serve various purposes, including the study of algorithms, understanding code logic, improving performance, and unearthing security vulnerabilities.
H2: Steps Involved in Decompilation
-
Disassembly: The first step in decompilation is disassembling the executable code into its machine instructions. This process involves converting the binary instructions into assembly language, which is human-readable. Disassemblers, such as IDA Pro, Ghidra, and Radare2, can perform this task efficiently.
-
Analysis: Once the assembly code is obtained, it undergoes thorough analysis to understand its structure, functionality, and implementation details. This involves carefully examining the instructions, tracing their flow, identifying loops, branches, and other control structures, and understanding the purpose of each section of the code.
-
High-Level Translation: The next step is to translate the assembly code into a high-level programming language. Decompilers, like Hex-Rays Decompiler, Hopper Disassembler, and Binary Ninja, employ various algorithms and heuristics to reconstruct the source code from the assembly instructions. The result is a high-level representation that closely resembles the original source code.
-
Optimization: The decompiled code often contains redundant or unnecessary instructions, making it inefficient and challenging to read. Optimizers can be used to refine and streamline the decompiled code, improving its readability, performance, and maintainability.
-
Reconstruction: Finally, the optimized code is restructured into a compilable form. This may involve adding appropriate variable names, comments, and documentation to make the code easier to comprehend and modify.
H2: Key Considerations in Decompilation
-
Understanding the Purpose: Clearly understanding the purpose and functionality of the software is crucial before attempting decompilation. This helps in setting the right goals and focusing on relevant aspects of the code.
-
Choosing the Right Tools: Selecting appropriate decompilers and disassemblers is essential for successful decompilation. Different tools offer varying features, capabilities, and compatibility with different platforms and programming languages.
-
Patience and Persistence: Decompilation can be intricate, and it’s important to have patience and perseverance when working through complex code. It may take several iterations and trials to achieve the desired results.
-
Legal and Ethical Implications: Decompiling software may raise legal and ethical considerations depending on the jurisdiction and the licensing terms of the software. It’s essential to ensure compliance with relevant laws, regulations, and license agreements before engaging in decompilation.
-
Security Concerns: Decompiling copyrighted or proprietary software without authorization poses security risks and could lead to copyright infringement or other legal issues. It’s crucial to address security concerns and ensure the integrity and confidentiality of the decompiled code.
Conclusion
Decompiling code is a valuable technique that enables programmers and developers to gain insight into the inner workings of software, facilitate learning, improve code quality, and address security vulnerabilities. However, it’s important to approach decompilation ethically and responsibly, ensuring compliance with legal and licensing requirements. As technology continues to evolve, decompilation techniques will likely become even more refined and accessible, empowering developers to delve deeper into the software realm and extract valuable knowledge.
Keyword Phrase Tags:
- Code Decompilation
- Reverse Engineering Software
- Disassembly and Analysis
- High-Level Translation and Optimization
- Decompilation Considerations

!Congratulations on the general post. are you able to help my sister add and apply a bit more examples after reversing binary code and how would we automate the process?
This article is a bit too difficult for me, but thanks for the info
The first part was a bit over my head, but the section on decompiling managed code may come in handy in the future.
complete rubbish
The write-up is quite amazing. Nevertheless, some more references would make the article even more comprehensive.
You show! I no comprende
This looks like a handy skill to have.
I’d love to see a tutorial on how to do this.