Data Encryption Errors: Implementing Secure Encryption Methods
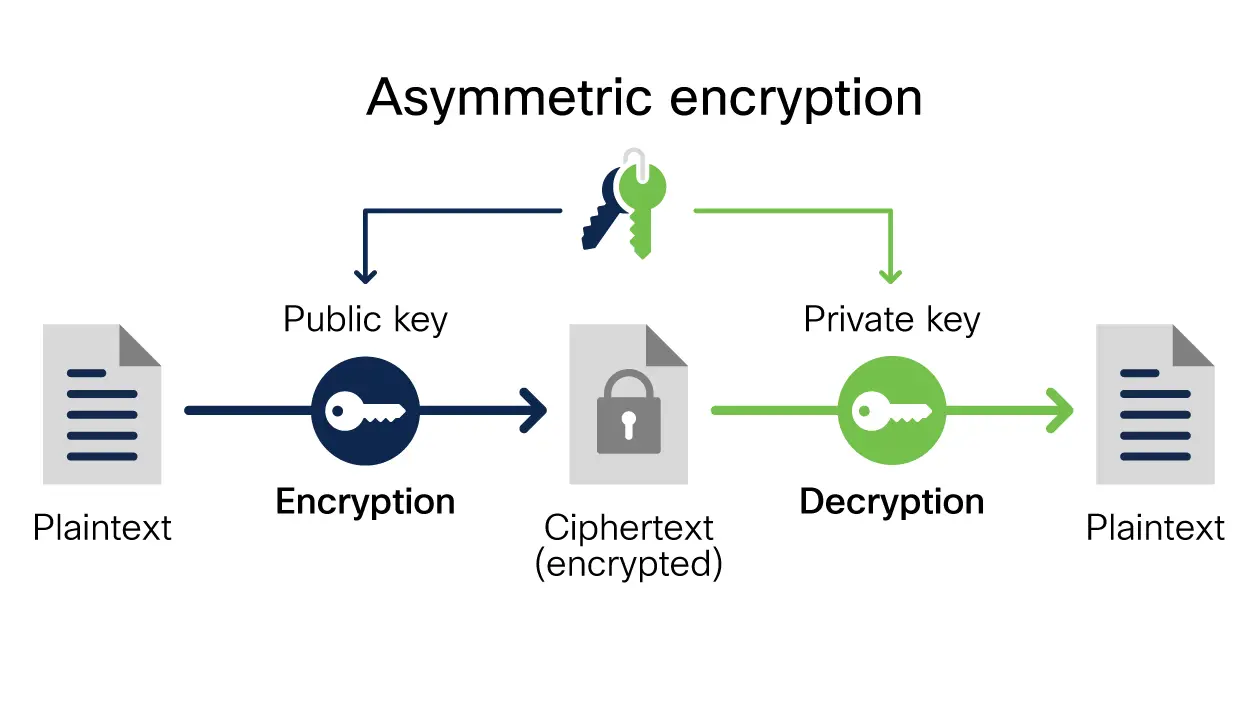
In the digital age, data encryption plays a paramount role in safeguarding sensitive information from unauthorized access. However, organizations often encounter various data encryption errors that compromise their security posture. These errors stem from both human and technical factors, hindering the effective implementation of secure encryption methods.
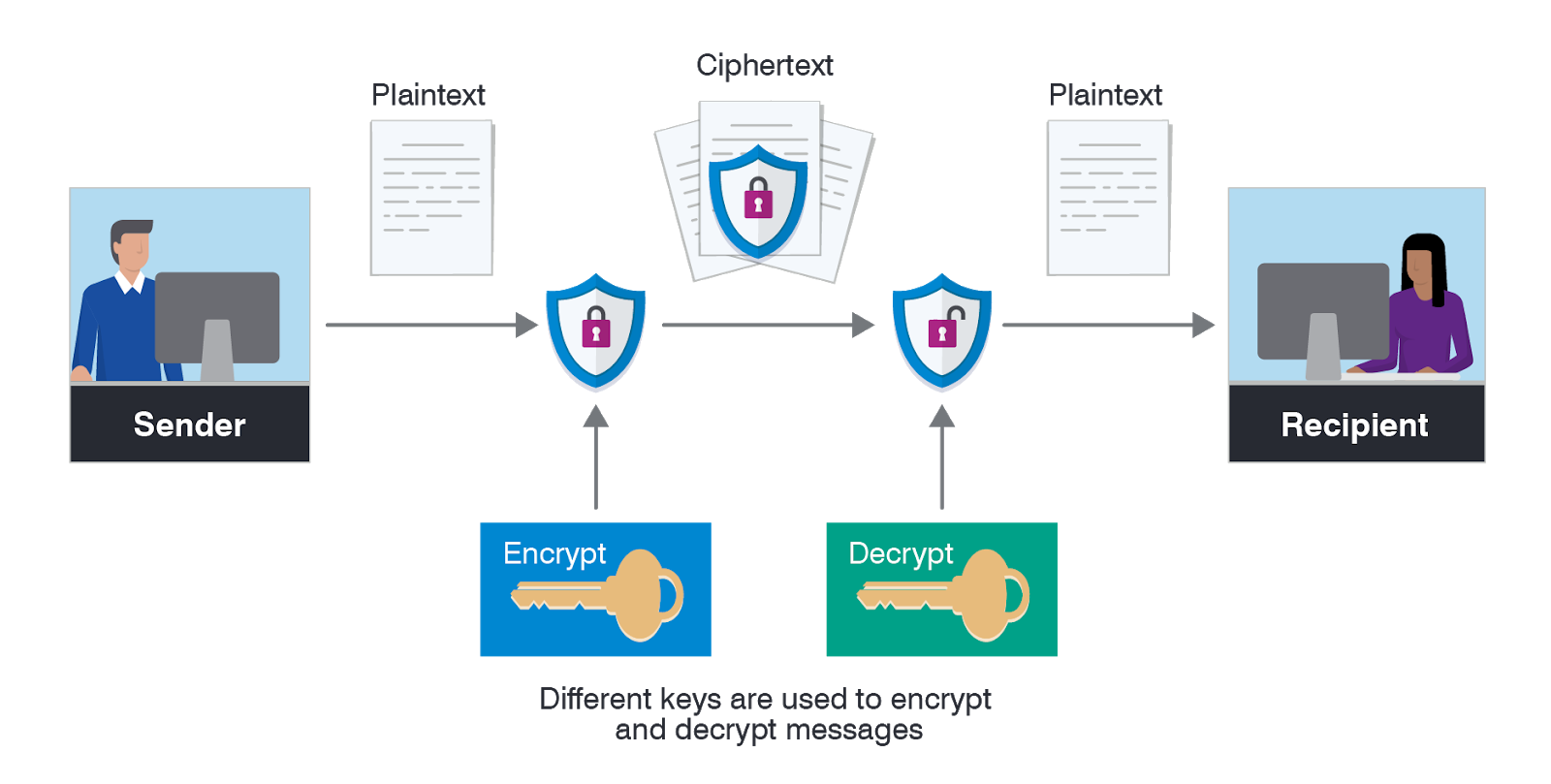
Common Encryption Errors:
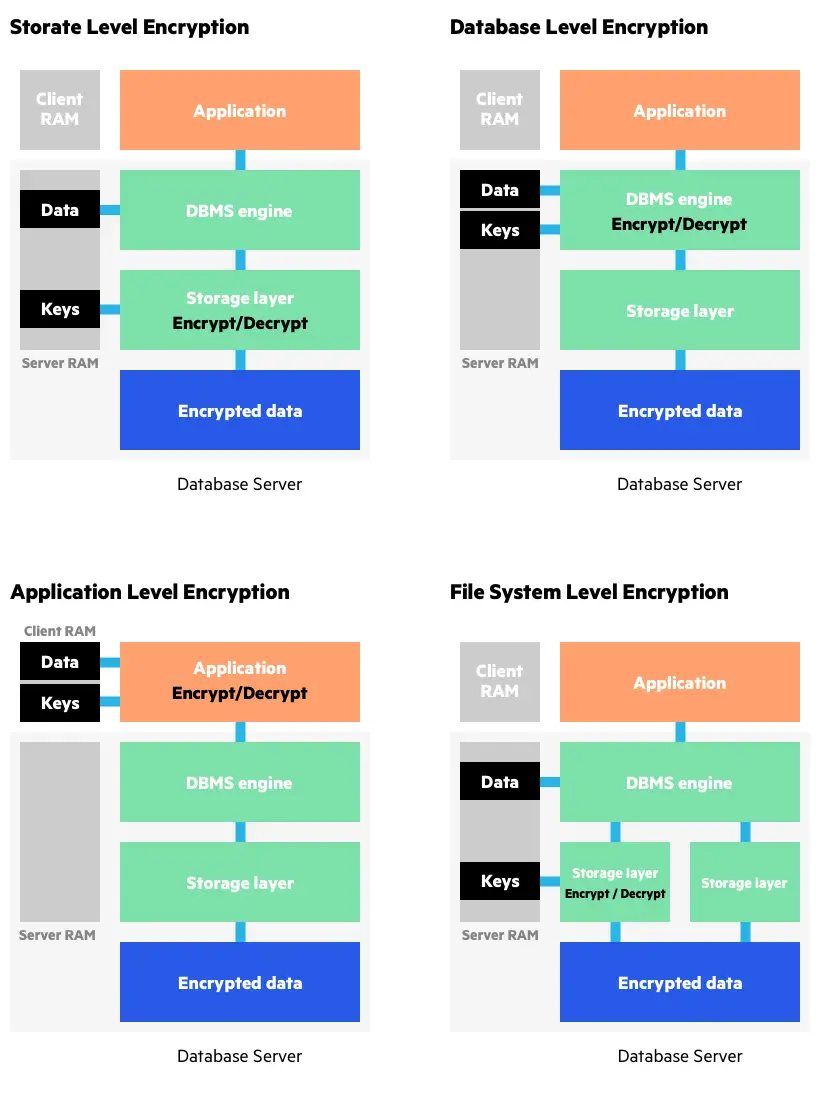
-
Weak Encryption Algorithms: Using encryption algorithms that are outdated or insecure can easily be compromised by modern computing power. Ensure the use of robust algorithms such as AES-256 or RSA-2024.
-
Insufficient Key Management: Poor key management practices, such as weak or predictable encryption keys, can lead to unauthorized decryption. Establish clear key management policies, including key generation, rotation, and storage procedures.
-
Encryption Scope Errors: Failing to encrypt all sensitive data, especially in transit and at rest, leaves vulnerabilities for attackers to exploit. Define a comprehensive encryption strategy that addresses all data types and scenarios.
-
Improper Encryption Implementation: Technical errors during encryption implementation, such as incorrect key lengths or formatting, can render encryption ineffective. Ensure proper configuration and testing of encryption systems to prevent such errors.
-
User Negligence: Human error, such as sharing encryption keys or neglecting security protocols, can create vulnerabilities. Educate users on the importance of data protection and enforce strict encryption protocols.
Consequences of Encryption Errors:
Data encryption errors have severe consequences for organizations:
-
Data Breaches: Sensitive information, such as customer data, financial records, or intellectual property, becomes vulnerable to unauthorized access.
-
Compliance Violations: Failing to implement secure encryption practices can lead to non-compliance with industry regulations and legal requirements.
-
Reputational Damage: Data breaches resulting from encryption errors damage an organization’s reputation and erode trust among customers and partners.
Implementing Secure Encryption Methods:
To mitigate these errors, organizations should focus on:
-
Conducting Security Audits: Regularly assessing encryption practices identifies vulnerabilities and helps organizations stay up-to-date with industry best practices.
-
Adopting Encryption Standards: Utilizing established encryption standards, such as FIPS 140-2 or ISO 27000 series, ensures compliance and reliability.
-
Implementing Encryption Management Solutions: Centralized encryption management platforms streamline encryption tasks, automate key management, and enhance overall security.
-
Training and Education: Educate users on the importance of encryption, proper key handling, and reporting potential vulnerabilities.
By implementing secure encryption methods and addressing common encryption errors, organizations can significantly enhance their data protection posture. Protecting sensitive information in the digital realm is crucial for safeguarding privacy, maintaining legal compliance, and preserving reputational integrity.## Data Encryption Errors: Implementing Secure Encryption Methods
Executive Summary
Encryption is essential for protecting sensitive data, but errors in its implementation can render it ineffective. This article examines common data encryption errors and provides best practices for implementing secure encryption methods. Businesses must address these errors promptly to safeguard their data and maintain regulatory compliance.
Introduction
The proliferation of cyber threats has made data encryption a critical aspect of data security. Encrypting data ensures its confidentiality, integrity, and availability, but errors in the encryption process can compromise its effectiveness. This article presents a comprehensive analysis of common encryption errors, along with practical guidance for implementing robust encryption mechanisms.
Common Data Encryption Errors
1. Weak Encryption Algorithms
Selecting a weak encryption algorithm can leave data vulnerable to decryption attacks. Common errors include:
- Choosing non-cryptographic algorithms (e.g., XOR)
- Using outdated algorithms (e.g., DES, RC4)
- Employing algorithms with known weaknesses (e.g., MD5)
2. Poor Key Management
Proper key management is crucial for data protection. Common errors involve:
- Using weak or predictable keys
- Failing to rotate keys regularly
- Sharing keys insecurely
- Storing keys unencrypted
3. Encryption Context Errors
Misapplying the encryption context can lead to data breaches. Common errors include:
- Encrypting data that should not be encrypted
- Failing to encrypt sensitive data
- Incorrectly configuring encryption variables (e.g., initialization vector)
4. Mishandling Encrypted Data
Proper handling of encrypted data is essential to prevent data exposure. Common errors include:
- Storing encrypted data in an insecure location
- Transmitting encrypted data over an unencrypted channel
- Decrypting data on insecure devices
5. Insufficient Encryption Coverage
Failing to encrypt all sensitive data leaves the organization vulnerable to data breaches. Common errors include:
- Leaving data unencrypted in databases and file systems
- Exposing sensitive data through unencrypted APIs
- Relying on third-party services without encryption safeguards
Conclusion
Errors in data encryption can have severe consequences for businesses. By understanding these common errors and implementing best practices for secure encryption, organizations can strengthen their data protection posture, maintain regulatory compliance, and build trust with their customers and partners.
Keyword Tags
- Data Encryption Errors
- Encryption Algorithm Selection
- Key Management Best Practices
- Encryption Context Management
- Secure Data Handling

