Cryptography Concept Confusions: Understanding the Basics of Cryptographic Security
Cryptography is often perceived as a complex and technical field, but it’s essential to understand its core concepts to safeguard digital information and protect privacy. Common confusions surround the fundamental principles of cryptography, leading to misunderstandings about its capabilities and applications. This article aims to clarify these confusions, providing a comprehensive explanation of cryptographic security’s basics.

Confusion 1: Encryption and Decryption Are the Same

Cryptography involves two key operations: encryption and decryption. Encryption transforms plaintext (readable information) into ciphertext (scrambled data), making it unintelligible to unauthorized individuals. Decryption is the reverse process, reconstructing the plaintext from ciphertext using a specific key. These operations are not interchangeable; encryption is the act of securing data, while decryption is the process of retrieving it.
Confusion 2: Cryptography Always Ensures Unbreakable Security
While cryptography provides effective data protection, it is not inherently unbreakable. The strength of cryptographic algorithms is measured by their key length, and longer keys result in enhanced security. However, advancements in computing power and analytical techniques can potentially compromise even the most secure encryption algorithms if key lengths are not sufficiently large.
Confusion 3: All Cryptography Algorithms Are Equal
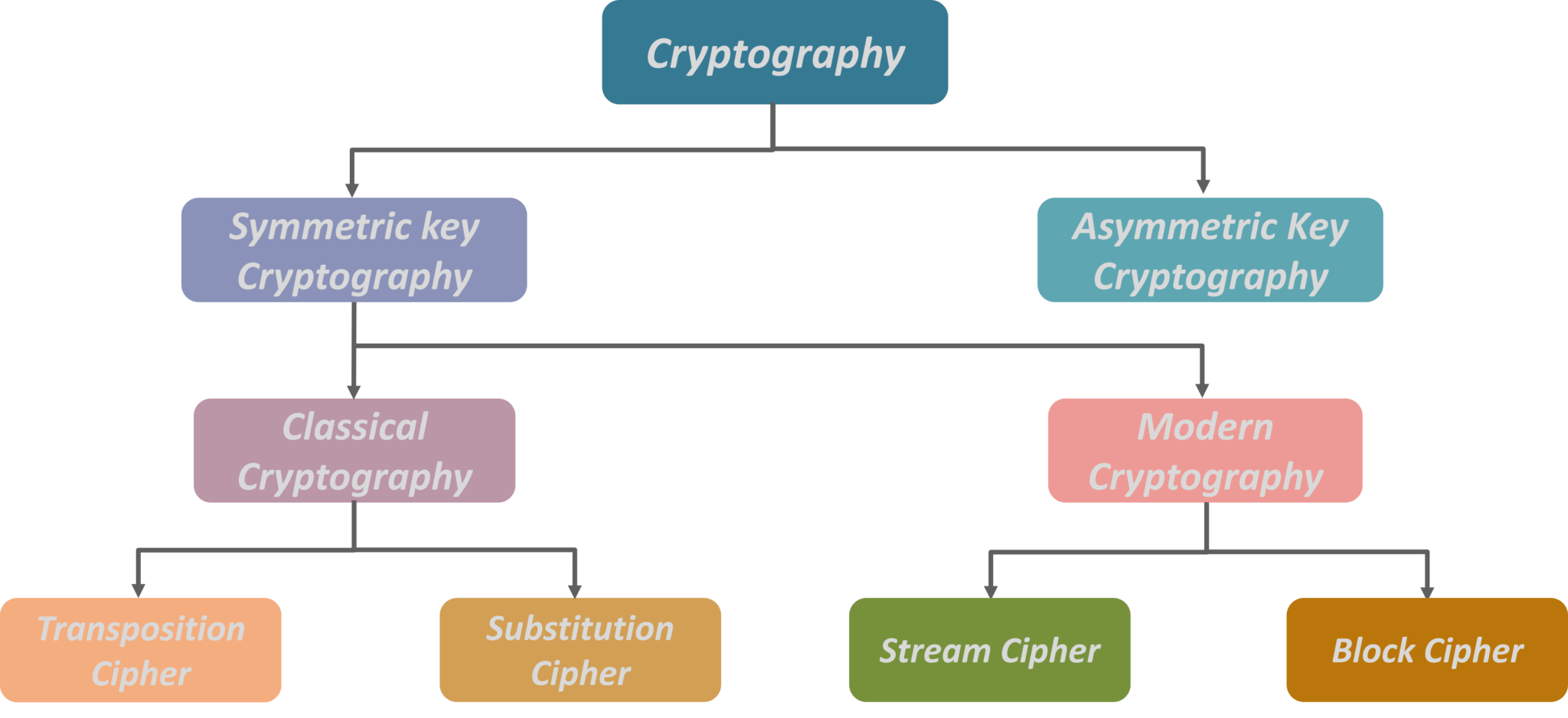
There are various cryptographic algorithms, each with advantages and limitations. Symmetric algorithms use the same key for encryption and decryption, while asymmetric algorithms employ a pair of keys (public and private). The appropriate choice of algorithm depends on the specific security requirements of the application. For instance, symmetric algorithms are efficient and suitable for bulk data encryption, while asymmetric algorithms offer secure key distribution and digital signatures.
Confusion 4: Hash Functions Are Encryption Algorithms
Hash functions are distinct from encryption algorithms. They take an input of varying length and produce a fixed-size output called a hash. Hash functions are irreversible and are commonly used to protect data integrity. Unlike encryption, hash functions do not provide confidentiality; rather, they ensure that data has not been altered or tampered with.
Confusion 5: Cryptography Renders Data Completely Inaccessible
While cryptography conceals data in ciphertext, it does not make it irrecoverable. Authorized parties with the correct decryption key can retrieve the original plaintext. Cryptography’s primary objective is to prevent unauthorized access to confidential information without compromising the ability to access it when necessary.
Understanding the fundamentals of cryptographic security helps avoid common misunderstandings and misconceptions. By demystifying encryption and decryption, acknowledging the limitations of cryptographic strength, distinguishing between algorithms, comprehending hash functions, and appreciating data accessibility, individuals can make informed decisions about implementing cryptographic solutions for safeguarding sensitive information.## Cryptography Concept Confusions: Understanding The Basics Of Cryptographic Security
Executive Summary
In the digital age, cryptography plays a pivotal role in safeguarding sensitive information and ensuring data integrity. However, many individuals struggle to grasp the fundamental concepts underlying this complex field. This guide delves into the basics of cryptography, clarifying common misconceptions and providing a comprehensive understanding of its key principles. By unraveling the complexities of cryptographic techniques, we empower readers to navigate the digital landscape with confidence, ensuring the protection of their data.
Introduction
Cryptography, the art of transforming information in ways that prevent unauthorized access or alteration, forms the backbone of modern cybersecurity. While its principles may appear intricate, understanding the basics is crucial for anyone seeking to protect their digital assets. This guide offers a comprehensive overview of essential cryptographic concepts, clarifying common confusions and equipping readers with the knowledge necessary to navigate the intricate world of digital security.
FAQs
-
What is the difference between encryption and decryption?
- Encryption: The process of transforming plaintext into ciphertext using an algorithm and key, making it unintelligible to unauthorized parties.
- Decryption: The inverse of encryption, converting ciphertext back into plaintext using the same algorithm and key, allowing authorized parties to access the original data.
-
How does cryptography help protect my data?
- Conceals sensitive information from unauthorized access
- Ensures the integrity of data by detecting any unauthorized modifications
- Provides authentication mechanisms to verify the authenticity of digital entities
-
Is cryptography only used for online banking and financial transactions?
- No, cryptography finds applications in various domains, including:
- Secure messaging
- Digital signatures
- Blockchain technology
- Password protection
- Data storage
- No, cryptography finds applications in various domains, including:
Subtopics
Symmetric-Key Cryptography
A type of cryptography where the same key is used for both encryption and decryption.
- Advantages:
- Fast and efficient
- Simple to implement
- Disadvantages:
- Key management can be challenging
- Vulnerable to brute-force attacks
Asymmetric-Key Cryptography
A type of cryptography that utilizes two different keys, one for encryption and one for decryption.
- Advantages:
- Enhanced security against brute-force attacks
- Supports digital signatures
- Disadvantages:
- Computationally more expensive than symmetric-key cryptography
- Key management requires careful attention
Hash Functions
One-way functions that transform data of any size into a fixed-length digest, often used for digital signatures and data integrity checks.
- Properties:
- Irreversibility: Cannot derive original data from the hash
- Uniqueness: Two different inputs rarely produce the same hash
- Collision resistance: Finding two different inputs with the same hash is computationally difficult
Digital Signatures
Electronic signatures that ensure the authenticity and integrity of digital documents.
- Process:
- Sender creates a hash of the document and encrypts it using their private key
- Recipient verifies the signature by decrypting it with the sender’s public key and comparing it to the hash of the received document
- Applications:
- Secure document signing
- Code signing
- Message authentication
Blockchain Technology
A distributed ledger that stores data in a secure and tamper-proof manner, often associated with cryptocurrencies.
- Key Features:
- Decentralized nature
- Data immutability
- Consensus mechanisms
- Applications:
- Cryptocurrencies
- Supply chain management
- Digital identity
Conclusion
Mastering the basics of cryptography empowers individuals to safeguard their sensitive data and navigate the digital landscape with confidence. By understanding the common misconceptions and gaining a thorough understanding of cryptographic techniques, we can effectively protect our privacy, prevent unauthorized access to information, and ensure the reliable communication and storage of data in the interconnected world we inhabit. Embracing these principles forms the foundation for robust cybersecurity practices, ensuring the integrity and confidentiality of our digital interactions.
Keyword Tags
- Cryptography
- Encryption
- Decryption
- Digital Signatures
- Blockchain Technology




