Containerization Confusion: Docker and Kubernetes Deployment Mistakes
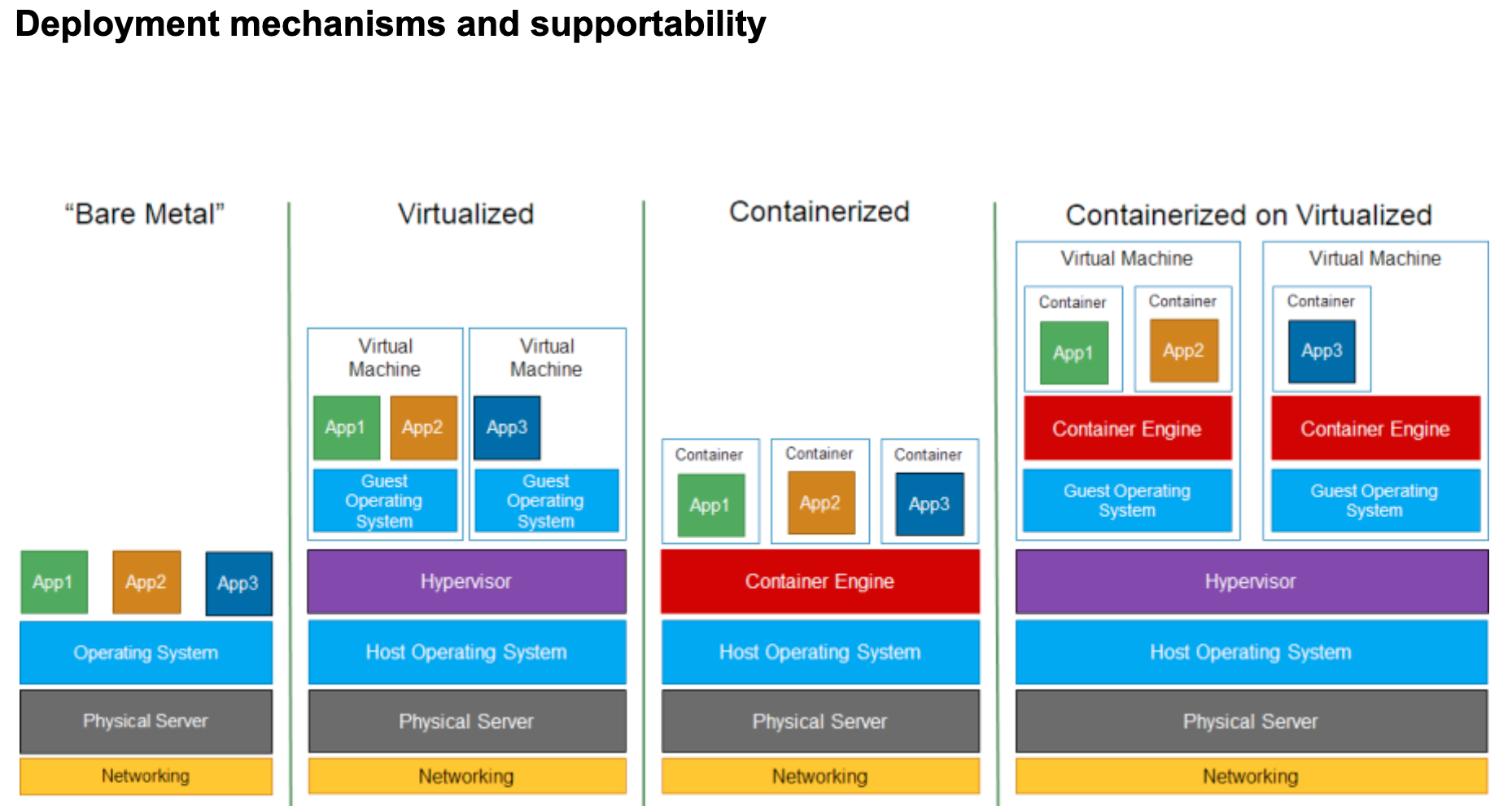
The use of containers has profoundly changed software development practices. Docker and Kubernetes are two of the most popular containerization technologies, but their implementation can be confusing. Common mistakes during Docker and Kubernetes deployments include:
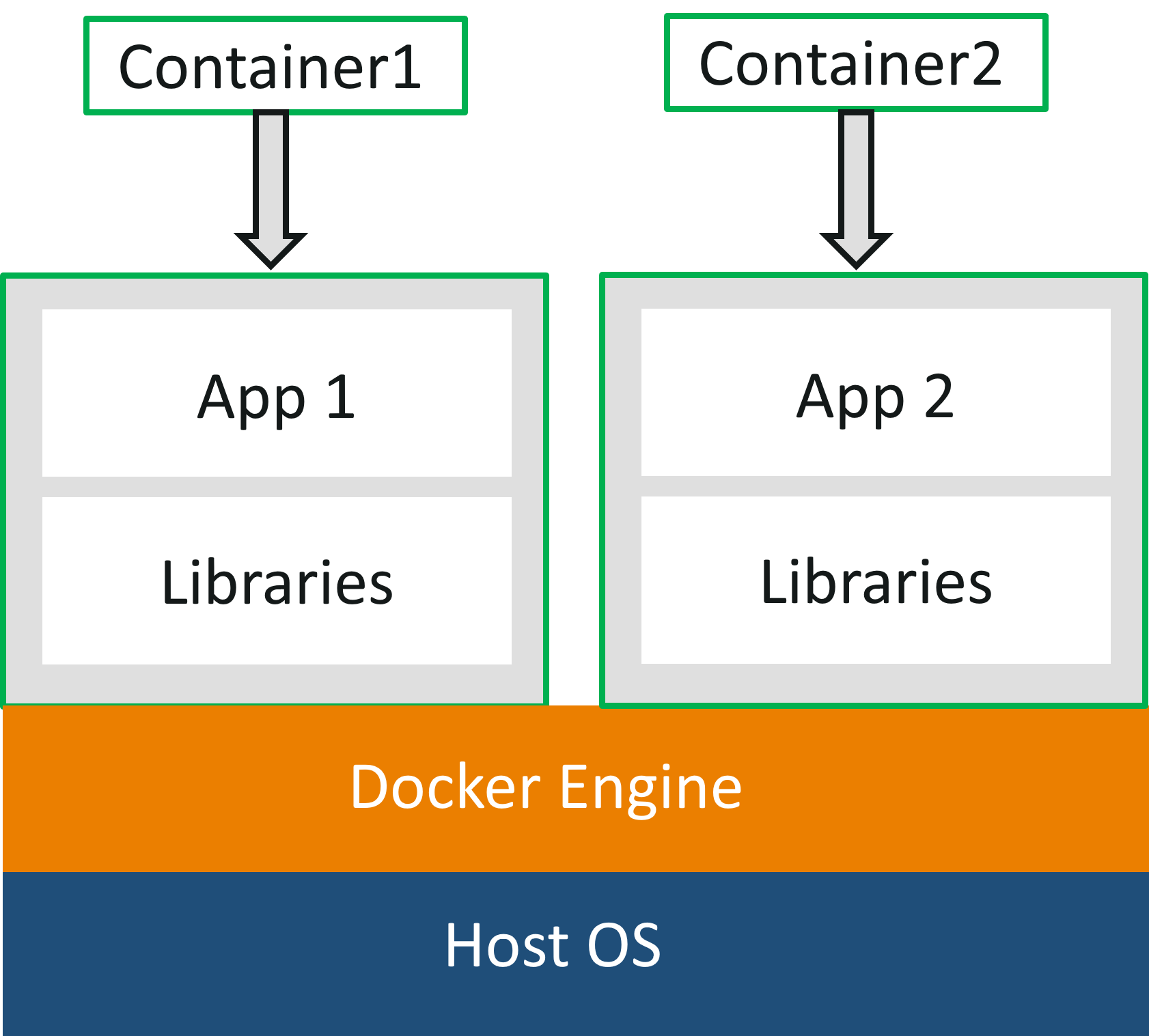
-
Mixing Runtime and Development Environments: Deploying an application directly from a development environment to production can lead to issues due to differences in system configurations. Instead, use a dedicated continuous integration/continuous delivery (CI/CD) pipeline to automate the deployment process.

-
Neglecting Image Security: Container images are packages of software that can include vulnerabilities. Ensure images are scanned for security issues and patched regularly. Consider using a centralized registry to manage and track images.
-
Incorrect Kubernetes Cluster Configuration: Kubernetes components, such as nodes and pods, must be configured correctly to ensure stable and reliable deployment. Misconfigurations can lead to unexpected behavior, performance issues, or even data loss.
-
Inadequate Resource Allocation: Containers require specific resources, such as CPU, memory, and storage. Failing to allocate sufficient resources can result in performance degradation or application failures. Use resource monitoring tools to determine optimal resource allocation.
-
Overlooking Load Balancing and Scalability: Kubernetes provides load balancing capabilities, but it’s important to configure them correctly to handle traffic and maintain application availability. Additionally, plan for scalability by considering how to scale pods based on demand.
-
Ignoring Logging and Monitoring: Collecting and analyzing logs and metrics is crucial for troubleshooting and performance optimization. Ensure adequate logging and monitoring systems are in place to provide insights into application behavior and identify potential problems.
-
Lack of Disaster Recovery Plan: A well-defined disaster recovery plan is essential for mitigating system failures. Establish backup mechanisms, such as regular image backups, and test the plan regularly to ensure data protection and application resilience.
By avoiding these common mistakes, organizations can leverage Docker and Kubernetes effectively to improve their software development and deployment processes. Proper planning, configuration, and maintenance are critical for successful and reliable containerization deployments.## Containerization Confusion: Docker And Kubernetes Deployment Mistakes
Executive Summary
The rapid adoption of containerization technologies such as Docker and Kubernetes has brought about numerous benefits for businesses, including improved agility, scalability, and portability. However, the complexity of these technologies can also lead to deployment mistakes that can hinder the full realization of their potential. This article identifies common Docker and Kubernetes deployment mistakes, providing guidance to help businesses avoid these pitfalls and ensure successful containerization initiatives.
Introduction
Containerization has emerged as a transformative approach to software development and deployment. Docker and Kubernetes are leading containerization technologies that provide numerous advantages, including the ability to package applications and their dependencies into isolated and portable units, known as containers. These containers can be deployed and managed across diverse environments, enabling developers to build and deliver applications more efficiently. However, the complexity of Docker and Kubernetes can lead to deployment mistakes that can compromise the stability, performance, and security of containerized applications. This article delves into these common mistakes and provides practical guidance to help businesses navigate the complexities of containerization and realize its full benefits.
FAQs
1. What is the purpose of Docker in containerization?
Docker is a containerization platform that allows developers to package applications into isolated and portable containers. These containers can be deployed and managed across diverse environments, simplifying the development, deployment, and maintenance of applications.
2. What is Kubernetes and how does it relate to Docker?
Kubernetes is a container orchestration platform that automates the deployment, management, and scaling of containerized applications. It enables developers to manage multiple containers across clusters of machines, ensuring high availability, load balancing, and resource optimization.
3. What are the key benefits of using Docker and Kubernetes?
Docker and Kubernetes provide numerous benefits, including improved agility, scalability, portability, consistency, and efficiency. They enable developers to build, test, and deploy applications more quickly and reliably, while also simplifying the management and scaling of containerized applications.
Common Docker and Kubernetes Deployment Mistakes
Dependency Management
-
Failing to define dependencies explicitly: Clearly defining the dependencies of containerized applications is crucial to ensure consistent and reliable operation. Omitting or incorrectly specifying dependencies can lead to errors and unexpected behavior during deployment.
-
Neglecting version control for dependencies: Managing dependencies effectively requires version control to ensure that the appropriate versions of dependencies are used consistently across environments. Ignoring version control can introduce inconsistencies and vulnerabilities.
-
Mixing local and external dependencies: Mixing dependencies from local sources and external repositories can lead to conflicts and version mismatch issues. It is recommended to rely primarily on external repositories for dependencies to maintain consistency and security.
-
Overlooking security vulnerabilities in dependencies: Dependency management must include regular vulnerability scanning to identify and mitigate security risks. Failing to do so can expose applications to security breaches and compromise the integrity of the containerized environment.
-
Ignoring dependency updates: Regularly updating dependencies is essential to address security vulnerabilities, improve functionality, and maintain compatibility. Neglecting dependency updates can leave applications vulnerable and hinder performance.
Configuration Management
-
Hard-coding sensitive information in configuration files: Containerized applications should not store sensitive information such as passwords, tokens, or encryption keys in plain text configuration files. This exposes the application to security breaches and compromises its confidentiality.
-
Lack of centralized configuration management: Managing configuration across multiple containers can be challenging. A centralized configuration management system ensures consistency, simplifies maintenance, and reduces the risk of misconfigurations.
-
Insufficient documentation of configuration changes: Configuration changes should be documented and tracked to facilitate troubleshooting, auditing, and rollback if necessary. Omitting documentation can hinder system maintenance and recovery.
-
Overriding configuration settings without understanding the implications: Modifying configuration settings without a clear understanding of their impact can result in unexpected behavior or system instability. Thorough evaluation and testing are essential before making configuration changes.
-
Ignoring performance implications of configuration settings: Configuration settings can significantly affect the performance of containerized applications. It is important to consider the performance implications of configuration changes and optimize settings accordingly.
Networking and Security
-
Exposing unnecessary ports: Containerized applications should only expose ports that are absolutely necessary for their operation. Unnecessarily exposing ports creates a potential attack surface for malicious actors.
-
Lack of network isolation: Insufficient network isolation between containers can lead to security breaches and data leaks. It is essential to implement network isolation mechanisms such as security groups and network policies to protect containers from each other.
-
Ignoring security best practices: Containerized applications should adhere to security best practices such as using encryption, implementing authentication and authorization mechanisms, and regularly scanning for vulnerabilities. Neglecting these practices can compromise the security of the containerized environment.
-
Lack of monitoring and logging: Monitoring and logging are critical for identifying and addressing security incidents and system issues. Insufficient monitoring and logging can result in delayed detection and response to potential threats.
-
Insecure container registries: Container registries must be secured to protect container images from unauthorized access and malware. Implementing strong authentication, authorization, and encryption measures is essential to ensure the integrity and security of container images.
Deployment and Management
-
Deploying untested or unstable images: Deploying container images that have not been thoroughly tested or are unstable can lead to application failures and system disruption. It is crucial to implement rigorous testing and quality assurance processes before deploying container images.
-
Manual deployment and management: Manual deployment and management of containerized applications can be error-prone and inefficient. Implementing automated deployment and management tools such as CI/CD pipelines streamlines the deployment process, reduces manual effort, and improves consistency.
-
Scaling without considering resource constraints: Scaling containerized applications without considering resource constraints can lead to performance degradation or even system failures. It is important to monitor resource utilization and proactively scale applications to meet demand while avoiding overprovisioning.
-
Overlooking container health checks: Container health checks are essential for monitoring the health and availability of containerized applications. Neglecting health checks can result in undetected application failures and degraded user experience.
-
Ignoring logs and metrics: Logs and metrics provide valuable insights into the performance and behavior of containerized applications. Ignoring logs and metrics makes it difficult to identify and address performance issues or potential errors.
Conclusion
Adopting Docker and Kubernetes for containerization can bring about significant benefits, but it is crucial to be aware of potential deployment mistakes that can hinder the realization of these benefits. This article has identified common Docker and Kubernetes deployment mistakes and provided practical guidance to help businesses avoid these pitfalls. By addressing these mistakes and following best practices, businesses can ensure the successful deployment and management of containerized applications, maximizing the benefits of containerization and driving digital transformation.
Relevant Keyword Tags
- Docker Deployment Mistakes
- Kubernetes Deployment Mistakes
- Containerization Best Practices
- Container Security
- Cloud-Native Development
