Cloudflare and the Future of Cybersecurity: Trends to Watch
Cloud computing and the proliferation of internet-connected devices are rapidly changing the world as we know it. At the same time, these advancements have also created new opportunities for cybercriminals to exploit vulnerabilities and launch attacks. In 2024, Cloudflare stood as a pioneer in the cybersecurity realm, playing a crucial role in protecting organizations and individuals from malicious activities.

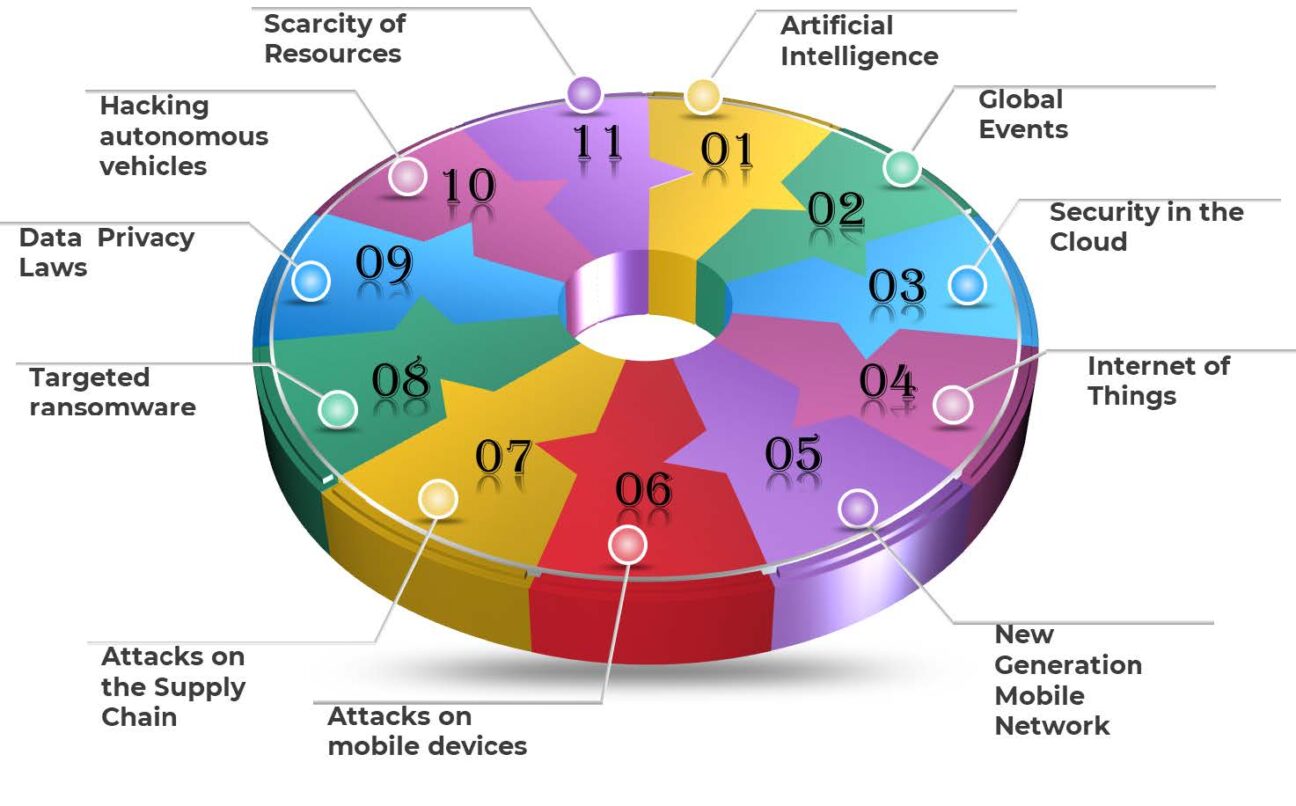
As we look toward the future of cybersecurity, Cloudflare remains at the forefront of innovation. The company has identified several key trends that will shape cybersecurity in the coming years:

-
Increased Automation: Artificial intelligence (AI) and machine learning (ML) are becoming increasingly prevalent in cybersecurity, enabling organizations to automate tasks such as threat detection and response. This increased automation will help organizations to identify and respond to threats more quickly and efficiently.
-
Growing Use of Cloud-Based Security: As more businesses move their data and applications to the cloud, the demand for security solutions that can protect these assets is rapidly growing. Cloudflare offers a suite of cloud-based security solutions that help organizations to protect their data, websites, and applications from attacks.
-
Focus on Data Protection: The increasing value of data has made it a primary target for cybercriminals. As a result, organizations are increasingly focused on data protection, and Cloudflare offers a range of solutions that help organizations to protect their data from unauthorized access, theft, and destruction.
-
Importance of Zero Trust: The traditional perimeter-based security model is no longer adequate in today’s cloud-first world. Organizations are adopting a zero-trust approach to security, which assumes that all users and devices should be considered untrustworthy until they are explicitly verified and authorized. Cloudflare offers solutions that help organizations to implement zero-trust security.
-
Rise of Cyber Insurance: Organizations are increasingly recognizing the importance of protecting themselves from financial losses caused by cyberattacks. Cyber insurance policies can provide businesses with compensation for expenses incurred due to cyberattacks, such as data breaches, loss of revenue, and business interruption. Cloudflare partners with leading cyber insurance carriers to offer policies that meet the unique needs of businesses.
By staying at the forefront of these trends, Cloudflare is well-positioned to help organizations protect themselves from the evolving threatscape. We look forward to seeing how Cloudflare will continue to shape the future of cybersecurity in the years to come.## Cloudflare And The Future Of Cybersecurity: Trends To Watch
Executive Summary
Cloudflare is a rapidly growing player in the cybersecurity space and its recent acquisition of Area 1 Security is a clear indication of its ambition to become a major force in the industry. Cloudflare’s unique approach to cybersecurity, which is based on its global network of data centers, has the potential to disrupt the traditional security market and change the way businesses think about protecting their data and applications.
Cloudflare provides a wide range of cybersecurity services, including DDoS protection, web application firewall (WAF), bot management, and SSL/TLS encryption. Cloudflare’s services are designed to be easy to use and affordable, and they can be deployed in minutes. This makes them a great option for businesses of all sizes, from small businesses to large enterprises.
Introduction
Cloudflare is a global cloud platform that provides a variety of services, including content delivery, security, and analytics. Cloudflare’s mission is to make the Internet faster, safer, and more reliable.
Cloudflare’s network spans more than 200 cities in over 100 countries. This gives Cloudflare a unique vantage point on the global Internet traffic. Cloudflare uses this data to identify and mitigate threats in real time.
Cloudflare’s security products are used by some of the world’s largest companies, including Google, Facebook, and Amazon. Cloudflare’s products have helped these companies to protect their websites and applications from a wide range of cyber threats.
FAQs
What is Cloudflare?
Cloudflare is a global cloud platform that provides a variety of services, including content delivery, security, and analytics. Cloudflare’s mission is to make the Internet faster, safer, and more reliable.
How does Cloudflare work?
Cloudflare operates a global network of data centers that cache content and provide security services. When a user visits a website that is protected by Cloudflare, their request is routed through Cloudflare’s network. Cloudflare’s network then checks the request for malicious content and blocks it if necessary. Cloudflare also caches the content of the website, so that it can be delivered to the user more quickly.
What are the benefits of using Cloudflare?
There are many benefits to using Cloudflare, including:
- Improved website performance – Cloudflare’s network can help to speed up the loading time of your website.
- Increased security – Cloudflare’s security services can help to protect your website from a wide range of cyber threats.
- Reduced costs – Cloudflare’s services are affordable and can help you to save money on your website hosting costs.
Top 5 Subtopics
1. Zero-trust security
Zero-trust security is a security model that assumes that all users and devices are untrustworthy. This model requires all users and devices to be authenticated and authorized before they can access any resources.
Important pieces of zero-trust security:
- Identity and access management (IAM) – IAM is the process of managing user identities and access to resources. IAM systems can help to ensure that only authorized users have access to the resources they need.
- Multi-factor authentication (MFA) – MFA is a security measure that requires users to provide multiple forms of identification before they can access a resource. MFA can help to prevent unauthorized users from accessing resources, even if they have the correct password.
- Device security – Device security is the process of protecting devices from unauthorized access and use. Device security measures can include things like antivirus software, firewalls, and intrusion detection systems.
- Network security – Network security is the process of protecting networks from unauthorized access and use. Network security measures can include things like firewalls, intrusion detection systems, and access control lists.
- Data security – Data security is the process of protecting data from unauthorized access, use, disclosure, disruption, modification, or destruction. Data security measures can include things like encryption, access control lists, and data backup and recovery.
2. Cloud security
Cloud security is the process of protecting cloud computing resources from unauthorized access and use. Cloud security measures can include things like identity and access management, multi-factor authentication, encryption, and data backup and recovery.
Important pieces of cloud security:
- Identity and access management (IAM) – IAM is the process of managing user identities and access to cloud resources. IAM systems can help to ensure that only authorized users have access to the resources they need.
- Multi-factor authentication (MFA) – MFA is a security measure that requires users to provide multiple forms of identification before they can access a cloud resource. MFA can help to prevent unauthorized users from accessing resources, even if they have the correct password.
- Encryption – Encryption is the process of converting data into a form that cannot be easily understood by unauthorized people. Encryption can help to protect data from unauthorized access, use, disclosure, disruption, modification, or destruction.
- Data backup and recovery – Data backup and recovery is the process of creating copies of data and storing them in a separate location. Data backup and recovery can help to protect data from loss due to hardware failure, software corruption, or natural disasters.
3. Artificial intelligence (AI) and machine learning (ML)
AI and ML are rapidly changing the way that businesses approach cybersecurity. AI and ML can be used to automate tasks, detect threats, and respond to incidents.
Important pieces of AI and ML in cybersecurity:
- Automated threat detection – AI and ML algorithms can be used to detect threats in real time. This can help to reduce the time it takes to identify and respond to threats.
- Incident response – AI and ML can be used to automate incident response tasks. This can help to reduce the time it takes to contain and mitigate threats.
- Security analytics – AI and ML can be used to analyze security data and identify trends. This can help to improve the effectiveness of cybersecurity programs.
4. Internet of Things (IoT) security
IoT devices are becoming increasingly common, and they create new challenges for cybersecurity. IoT devices are often vulnerable to attack, and they can be used to launch attacks on other devices.
Important pieces of IoT security:
- Device security – IoT devices should be protected by strong security measures, such as firewalls, intrusion detection systems, and encryption.
- Network security – IoT devices should be connected to secure networks. IoT devices should not be connected to public Wi-Fi networks or other insecure networks.
- Data security – Data collected by IoT devices should be protected from unauthorized access and use. IoT device data should be encrypted and stored in a secure location.
5. Blockchain security
Blockchain is a distributed ledger technology that has the potential to revolutionize many industries. Blockchain technology can be used to secure data and transactions.
Important pieces of blockchain security:
- Decentralization – Blockchain networks are decentralized, meaning that they are not controlled by a single entity. This makes blockchain networks more resistant to attack.
- Transparency – Blockchain networks are transparent, meaning that all transactions are recorded on the blockchain and can be viewed by anyone. This transparency makes it difficult for bad actors to operate on the blockchain undetected.
- Immutability – Once data is recorded on the blockchain, it is immutable, meaning that it cannot be changed or deleted. This immutability makes blockchain networks very secure.
Conclusion
Cloudflare is a rapidly growing player in the cybersecurity space, and its recent acquisition of Area 1 Security is a clear indication of its ambition to become a major force in the industry. Cloudflare’s unique approach to cybersecurity, which is based on its global network of data centers, has the potential to disrupt the traditional security market and change the way businesses think about protecting their data and applications.
Keyword Tags
- Cloudflare
- Cybersecurity
- Zero-trust security
- Cloud security
- AI and ML in cybersecurity
- IoT security
- Blockchain security
