Cloudflare Access: Enhancing Remote Work Security
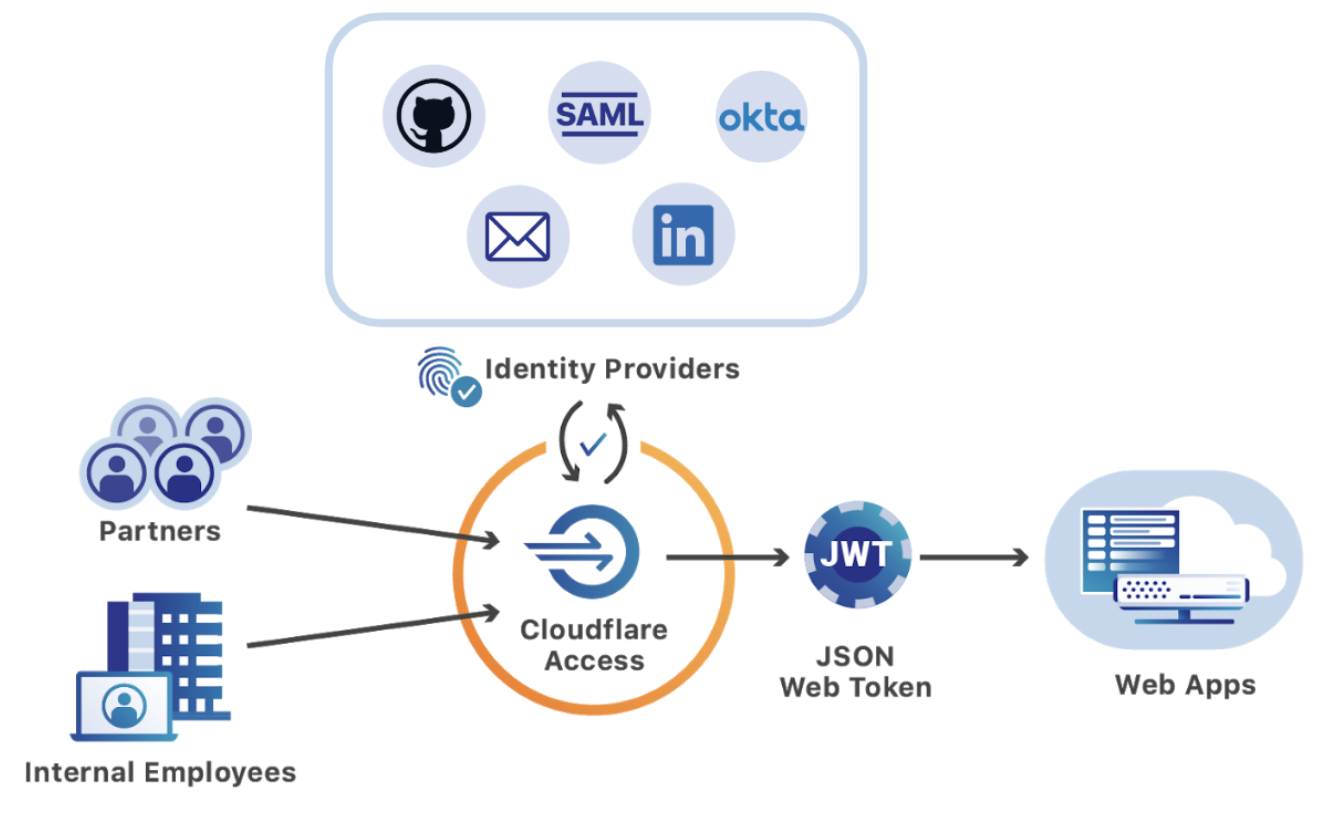
Cloudflare Access is an innovative solution that revolutionizes remote work security. It empowers organizations to safeguard their applications, resources, and data, ensuring seamless and secure access for employees regardless of their location. By leveraging Cloudflare’s vast global network, Access provides unparalleled performance, ensuring unrestricted and efficient access to critical assets from anywhere.
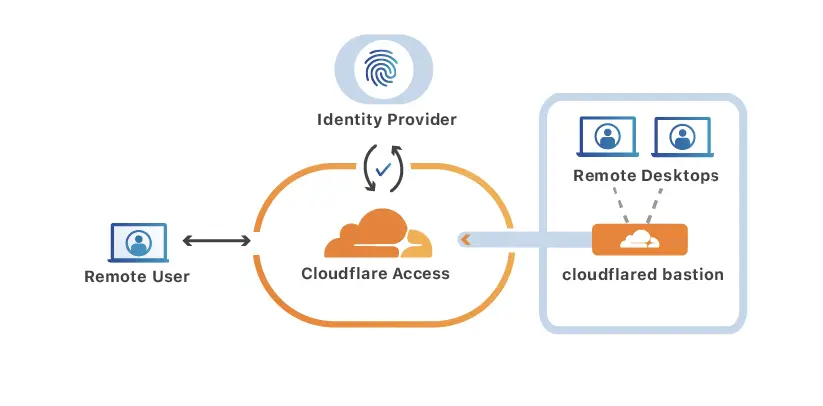
Access offers a comprehensive suite of security measures to protect against unauthorized access and malicious actors. Zero Trust principles guide its architecture, enforcing granular user validation before granting access. Multi-factor authentication and device posture checks further bolster security, mitigating the risk of account compromise or device vulnerabilities.
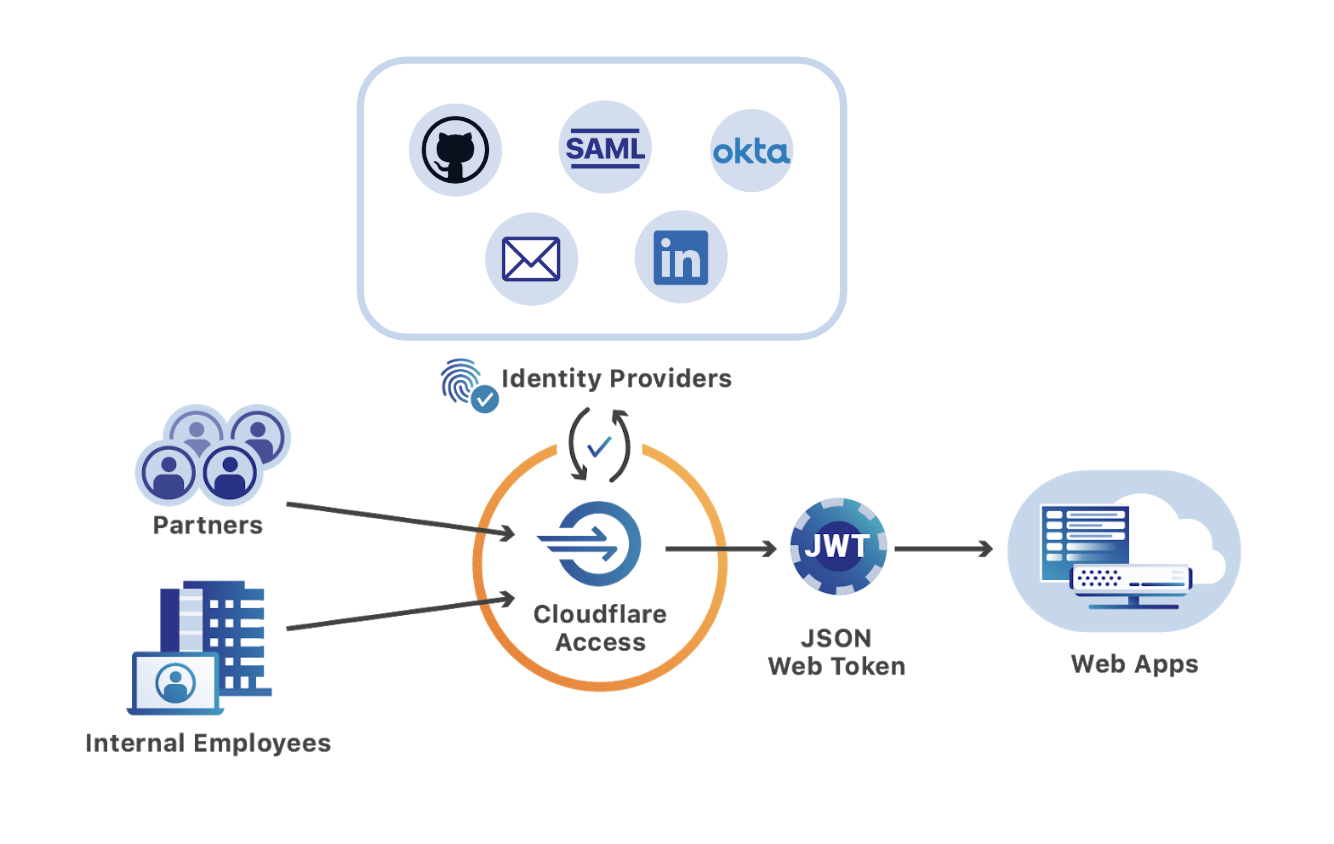
For user convenience, Access employs single sign-on (SSO), enabling employees to access multiple applications with a single set of credentials. This streamlines the authentication process and reduces the risk of password fatigue and security breaches. Additionally, Access supports role-based access control (RBAC), ensuring that users are granted only the necessary level of access based on their job functions or project requirements.
To facilitate seamless integration with existing workflows, Access offers a range of deployment options. It seamlessly integrates with identity providers such as Okta and Azure Active Directory, enabling organizations to extend their existing security infrastructure. Additionally, Access provides flexible configuration options, allowing organizations to tailor access policies to their specific security requirements.
By deploying Cloudflare Access, organizations gain peace of mind knowing that their remote workforce can securely access critical resources without compromising security. Its robust security measures, simplified user experience, and flexible deployment options make it an ideal solution for enterprises seeking to empower their remote teams without sacrificing security.## Cloudflare Access: Securing Remote Work
Executive Summary
Cloudflare Access provides a comprehensive solution for securing remote work by:
- Enhancing security without compromising employee productivity
- Simplifying authentication and authorization with single sign-on and identity-based policies
- Protecting applications and data with granular access controls
Introduction
The rise of remote work has brought new cybersecurity challenges. Cloudflare Access addresses these concerns by offering a cloud-based security solution that safeguards access to applications, data, and networks from anywhere.
FAQs
- What is Cloudflare Access?
Cloudflare Access is a cloud-based security solution that provides secure remote access to applications, data, and networks. - Why use Cloudflare Access?
Cloudflare Access enhances security, simplifies authentication and authorization, and protects applications and data. - How does Cloudflare Access work?
Cloudflare Access uses single sign-on, identity-based policies, and granular access controls to secure remote access.
Top 5 Subtopics
Access Management
Cloudflare Access provides comprehensive access management features:
- Single sign-on (SSO): Enables users to authenticate once and access multiple applications with a single click.
- Identity federation: Integrates with identity providers like G Suite, Azure AD, and Okta to centralize user management.
- Policy-based authorization: Enforces granular access controls based on user identity, device, and session attributes.
Data Security
Cloudflare Access safeguards sensitive data with advanced security measures:
- Encryption-in-transit and at-rest: Encrypts all data during transmission and storage to protect against unauthorized access.
- Public key infrastructure (PKI): Utilizes PKI-based certificates to establish secure connections and prevent data compromise.
- Least privilege access: Grants users only the minimum access permissions required for their roles.
Application Protection
Cloudflare Access protects web applications from malicious attacks:
- Web application firewall (WAF): Blocks malicious traffic and protects against web vulnerabilities such as SQL injection and cross-site scripting.
- Zero-day exploit protection: Detects and mitigates zero-day vulnerabilities to prevent application compromise.
- Rate limiting: Prevents brute force attacks and malicious bot activity by limiting the number of requests per user or device.
Network Security
Cloudflare Access secures remote networks with robust connectivity features:
- Virtual private network (VPN): Establishes secure connections to private networks for authorized users.
- Cloudflare Gateway: Inspects inbound and outbound network traffic to detect and block malicious activity.
- Bring your own IP (BYOIP): Allows organizations to use their own IP addresses for secure access without compromising network security.
User Experience
Cloudflare Access optimizes the user experience for remote workers:
- Centralized access: Provides a single dashboard for users to access all authorized applications and data.
- Seamless authentication: Enforces strong authentication measures without requiring users to remember multiple passwords.
- Self-service portals: Enables users to manage their own access settings and reset passwords independently.
Conclusion
Cloudflare Access empowers organizations to embrace remote work with confidence. By providing comprehensive security controls, simplifying authentication, and protecting applications and data, Cloudflare Access transforms the remote work landscape into a secure and productive environment.
Keywords
- Cloudflare Access
- Remote work security
- Single sign-on
- Data protection
- Application security
